Falco Feeds extends the power of Falco by giving open source-focused companies access to expert-written rules that are continuously updated as new threats are discovered.

Data — such as personally identifiable information (PII), protected health information (PHI), and financial records — are the coin of the realm for organizations and adversaries alike. This data fuels critical operations, enhances customer experience, and powers analytics-driven decisions, which makes it a high-value target for cybercriminals and state actors.
Defending sensitive data against threats and meeting regulatory compliance is often an expensive, manual process. Data sprawls across cloud environments, including in relational database services (RDS) and simple storage service (S3) buckets in AWS, which makes it difficult to understand where and what data is. At the same time, many security programs are playing a game of whack-a-mole with sensitive data: chasing alerts, battling backlogs, and scrambling to respond.
While there are no silver bullets in cybersecurity, there are solutions that can take some of the burden off of the teams tasked with stopping threat actors — and the developers relied upon to reduce risk in their builds. When you can accurately identify risk and detect when adversaries are targeting sensitive data, you’re able to quickly respond to the most urgent threats, vulnerabilities, and misconfigurations.
Introducing data security findings
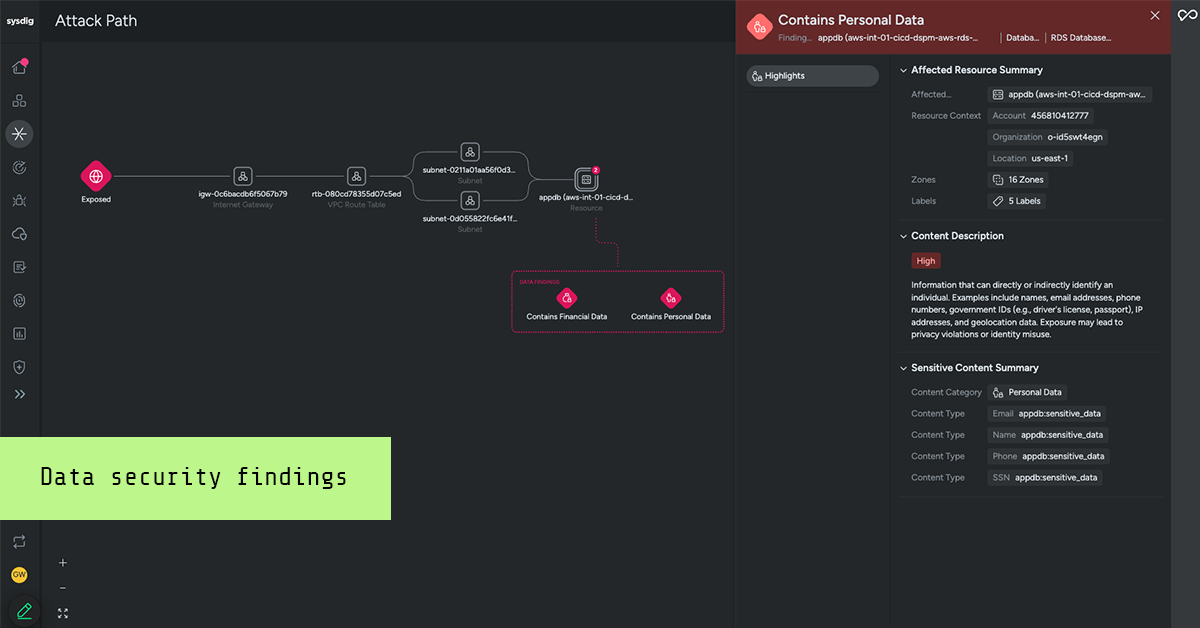
Data security findings is a new add-on feature powered by an integration with Bedrock Security that’s now available in Sysdig Secure. Data security findings provides the strategic clarity that business and security leaders need to proactively manage risk to valuable data. For practitioners, this new feature eliminates blind spots and uncertainty about data location and classification.
With data security findings, you gain the continuous scanning and AI-powered fingerprinting necessary to identify where data resides and classify what types of sensitive data you’re protecting. Bolstered by this information, you can reveal sensitive data exposure, focus remediation — including patching and misconfiguration fixes — and contextualize threats for faster, more confident response.
Key benefits of data security findings
Data security findings provides organizations with many capabilities found in standalone cloud-native data security posture management (DSPM) tools, without the need to swivel between solutions or tabs. With Data Security Findings, you can:
- Reveal data exposure: Automatically discover and classify personally identifiable information (PII), personal health information (PHI), and financial data to surface hidden risk. These risks could include sensitive data being involved in a security detection or residing in a database or S3 bucket with known vulnerabilities or misconfigurations.
- Focus remediation: Prioritize patching and configuration fixes for vulnerable or misconfigured resources where sensitive data resides. Even after a vulnerability is discovered by security analysts, it can take days, weeks, months, or even longer to patch by overwhelmed developers. By being able to identify when sensitive data is at risk, security teams can provide context to developers, who can then focus their efforts where they will make a significant difference.
- Contextualize threats: Visualize sensitive data in attack paths to quickly understand blast radius and confidently elevate the most critical alerts. Sysdig Secure Attack Path Analysis offers a quick and efficient way to uncover the critical paths that attackers may exploit to reach sensitive data. This feature also bridges the gap between potential risks and real-time events, enabling you to stop attacks before they can move laterally.
Together, these capabilities empower security and DevOps teams to protect sensitive data more confidently and efficiently.
Use cases for Sysdig’s data security findings
Data security findings supports a wide range of data-centric use cases, including:
- Improve regulatory compliance: Inform reporting aligned to compliance. By identifying, classifying, and protecting PII, PHI, and financial data, you can take informed action to avoid penalties and adhere to regulations such as HIPAA, GDPR, PCI DSS, and more.
- Enhance Incident Response Context: Enables you to quickly identify if an affected resource contains sensitive data to immediately understand blast radius and prioritize response.
- Quantify and reduce business risk from sensitive data exposure: Identify overexposed data, map risk paths, and prioritize remediation to reduce the likelihood of breaches.
- Enable proactive vulnerability and misconfiguration management: Reduce MTTR and improve collaboration between security and DevOps teams by using Data Security Findings information to prioritize patching and configuration fixes.
By addressing these critical use cases, Sysdig’s data security findings help organizations take a proactive, data-driven approach to security. Users can minimize risk, respond to threats faster, and accelerate vulnerability and misconfiguration management.
Strengthening cloud-native cybersecurity
With the addition of data security findings, Sysdig is continuing to add to a portfolio of features designed to enhance risk detection and remediation, reduce visibility gaps, and eliminate tool sprawl. Other Sysdig Secure capabilities include:
Cloud security posture management (CSPM): Enables users to monitor, identify, and remediate compliance risks and misconfigurations. CSPM features help you better prevent attacks, improve security hygiene with runtime insights, and understand what is in use in production.
Cloud workload protection (CWP): Provides robust security with deep runtime visibility and control for physical servers, virtual machines, containers, and serverless functions across cloud and on-premises architectures.
Cloud detection and response (CDR): Cloud attacks move fast — happening in 10 minutes or less. Sysdig CDR, underpinned by open source Falco, gives you real-time visibility into cloud assets and activities to meet the 555 Benchmark for Cloud Detection and Response.
Vulnerability management: Combines deep runtime with AI-powered remediation guidance to help you identify high-impact fixes and take fast, confident action.
Cloud infrastructure entitlement management (CIEM): Offers a comprehensive view of cloud resources to help prevent unauthorized access and lateral movement.
Conclusion
Almost 95% of companies [1] have a cloud footprint. While cloud infrastructures accelerate innovation and reduce operational overhead, they can also make protecting sensitive data more difficult. Cloud complexity introduces blind spots in data visibility — 83% of organizations said they have visibility gaps [2] — and these gaps increase risk while slowing remediation.
Data Security Findings enables you to quickly identify risk and detect when adversaries are targeting sensitive data. With this information, you can confidently manage vulnerabilities and configuration fixes while putting yourself into the best position to respond to the most urgent threats.
[1] Colorlib, “Cloud Computing Statistics,” July 2024.
[2] Bedrock Security, 2025 Enterprise Data Security Confidence Index, 2025.


