
Falco Feeds extends the power of Falco by giving open source-focused companies access to expert-written rules that are continuously updated as new threats are discovered.

On October 31, 2025, CISA confirmed that CVE-2024-1086, a privilege escalation vulnerability in the Linux kernel's netfilter component, is being actively exploited in ransomware campaigns. This use-after-free vulnerability, present in the Linux kernel for over 10 years, provides attackers with a path to gaining root privileges on compromised systems. It was first discovered in January 2024, with Linux publishing a patch the following month. With privileged access provided by the vulnerability, however, attackers can still launch ransomware operations.
CVE-2024-1086 opens a path to root privileges for threat actors, so identifying and patching it should be a priority for organizations with Linux infrastructure. Since this vulnerability has been present for 10 years, legacy and seldom-relied-on systems may still be exposed. Unpatched, CVE-2024-1086 creates an open surface for ransomware attacks.
This blog, based on the Sysdig Threat Research Team’s (TRT) investigation and analysis of CVE-2024-1086, explores how attackers are exploiting the vulnerability and what defenders can do to stay ahead.
Technical analysis of CVE-2024-1086
Vulnerability details
CVE-2024-1086 (CVSS 7.8) resides in the nft_verdict_init() function of the Linux kernel’s netfilter (nftables) component. The threat stems from the function’s failure to properly validate verdict parameters, which allows attackers to trigger a double-free condition in the kernel’s memory management.
The vulnerability was introduced via a commit in February 2014, making it present in kernel versions from 3.15 to 6.8-rc1. The versions requiring urgent patching are: Linux kernels between v5.14 and v6.6, including Debian, Ubuntu, and other distributions. The following versions were released with patches applied: v5.15.149+, v6.1.76+, and v6.6.15+.
Exploit analysis
This exploit leverages unprivileged user namespaces in order to access the nf_tables component, which includes the double-free vulnerability. By allocating a large number of socket buffers (SKBs), and then passing malformed SKBs through nf_tables, the double-free vulnerability can be triggered, allowing attackers to run malicious code in the kernel. The exploit then finds and overwrites modprobe_path, which enables attackers to execute a root shell.
Prerequisites for exploitation:
- User namespaces enabled
- Unprivileged user namespaces accessible (sysctl kernel.unprivileged_userns_clone = 1)
- nf_tables module enabled
These configurations are enabled by default on major enterprise distributions, including Debian and Ubuntu, as well as many cloud-optimized images, significantly expanding the attack surface.
This vulnerability is particularly concerning in environments with:
- Multi-tenant Linux systems with unprivileged user accounts.
- Container hosts where user namespaces are required for functionality.
- Linux servers exposed to the internet with vulnerabilities or weak passwords.
Ransomware campaigns
CISA's classification of CVE-2024-1086 as "known to be used in ransomware campaigns" emphasizes its severity. While CISA hasn't attributed the exploitation to any specific group, the vulnerability provides ransomware operators with several critical capabilities:
- Post-compromise escalation: The exploit grants root privileges on affected systems, enabling full administrative control.
- Defense evasion: Root access allows attackers to disable security tools, clear logs, and establish persistence.
- Lateral movement: Elevated privileges allow additional system compromise across environments.
The timing of active exploitation coincides with the increase of Linux-targeting ransomware groups, such as RansomHub, Akira, and LockBit. RansomHub, in particular, has emerged as the dominant ransomware-as-a-service (RaaS) group, conducting over 600 attacks using GoLang-based Linux malware designed to target enterprise environments.
Once initial access is gained through vulnerable services or stolen credentials, CVE-2024-1086 provides the elevated privileges necessary for system-wide encryption and data exfiltration operations. Public proof-of-concept (PoC) code, available since March 2024, has lowered the barrier to entry for even moderately skilled attackers.
Detecting CVE-2024-1086 exploitation with Sysdig Secure
Sysdig Secure includes out-of-the-box detection for CVE-2024-1086 with the rule “Possible Exploitation of Kernel Netfilter Vulnerability (CVE-2024-1086)” in the Sysdig Runtime Behavioral Analytics policy.
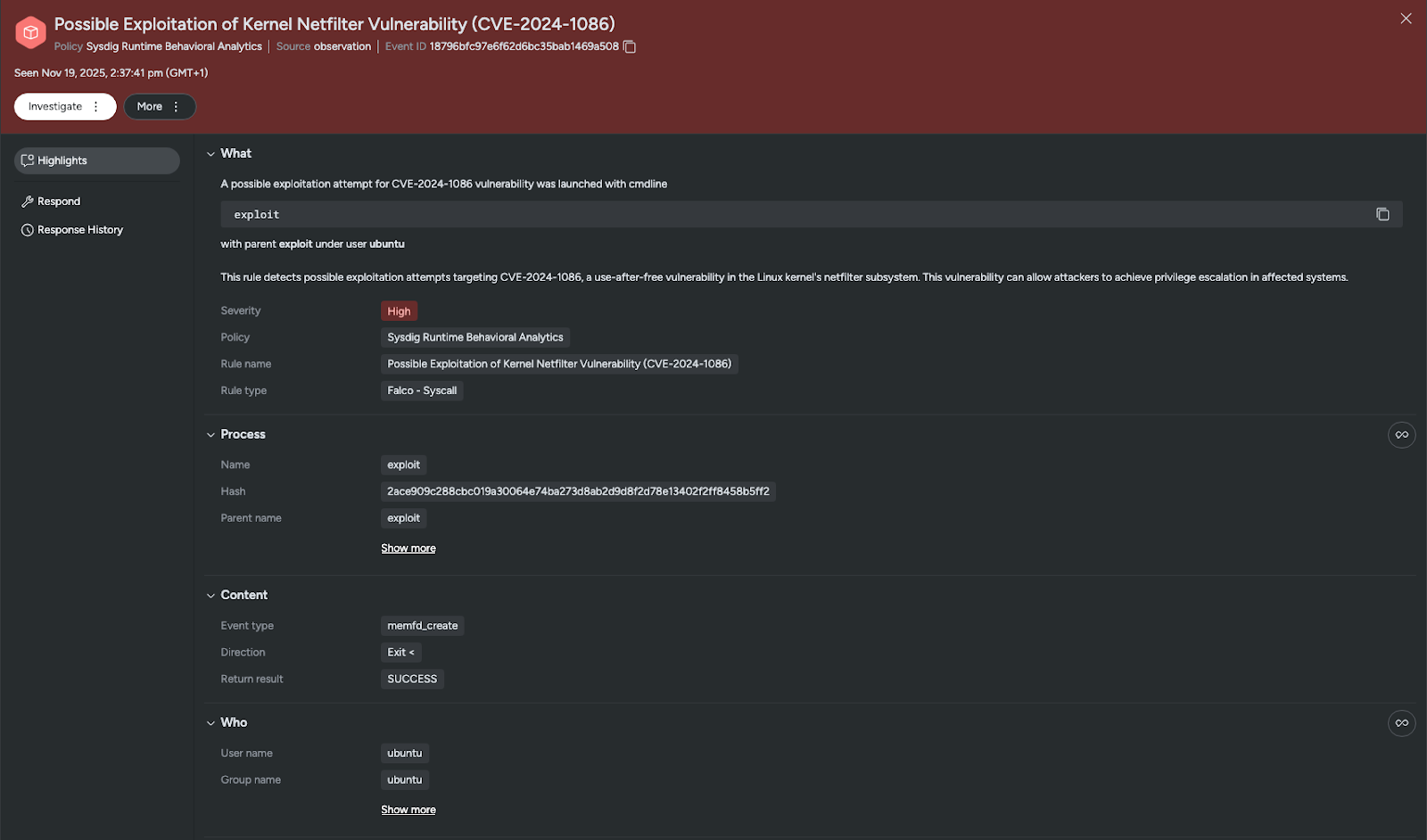
Ransomware detection is also provided through multiple mechanisms, including the Malware Detection policy and the runtime threat detection rule “Ransomware Filenames Detected,” which detects common file extensions and ransom note filenames. The Ransomware rule is enabled by default in the Sysdig Runtime Threat Detection policy.
Conclusion
CVE-2024-1086 is a critical security vulnerability, now included in CISA's KEV catalog, which bridges initial access to full system compromise and is highly valued by ransomware operators. The combination of reliable exploitation, public PoC code, and sophisticated Linux-targeting ransomware creates extreme risk to organizations if the vulnerability is not patched.
Since this vulnerability grants a path to root privileges, patching CVE-2024-1086 is a top priority for all Linux infrastructure. Its decade-long presence means legacy and forgotten systems remain exposed, offering persistent footholds for ransomware attacks.
While patching the vulnerability is the primary defense, robust runtime threat detection and response capabilities are crucial for identifying exploitation attempts, neutralizing them, and detecting post-compromise lateral movement before patches can be universally applied.
Follow the Sysdig Threat Research Team for ongoing analysis and updates on critical threats, like CVE-2024-1086.

