
Falco Feeds extends the power of Falco by giving open source-focused companies access to expert-written rules that are continuously updated as new threats are discovered.

On December 3, 2025, the React Team disclosed CVE-2025-55182, a critical unauthenticated remote code execution (RCE) vulnerability in React Server Components (RSCs). Dubbed "React2Shell", this maximum-severity flaw (CVSS 10.0) allows for potentially malicious code execution with a single crafted HTTP request. Next.js, which can be impacted downstream by React2Shell, has assigned CVE-2025-66478 to track its exposure.
For threat actors, React2Shell enables arbitrary server-side code execution upon exploitation, opening the door to data theft, lateral movement, and/or malware deployment. At the time of this writing, a public proof-of-concept (PoC) exploit has been released. Researchers report roughly 100% exploitation success rates against default configurations, which positions React2Shell as highly likely to be mass-exploited.
Following a detailed analysis, the Sysdig Threat Research Team (TRT) has developed a Falco detection rule for React2Shell, now available directly within Sysdig Secure. The Sysdig TRT recommends that all organizations running React 19 with Server Components take immediate action. Below, we provide detailed steps for remediation, along with a technical analysis of the vulnerability and its exploitation implications.
For a quick breakdown, look at our React2Shell video.
Technical analysis of React2Shell
Vulnerability details
CVE-2025-55182 resides in the RSC "Flight" protocol, specifically in how a react-server handles HTTP requests for Server Function endpoints. This deserialization flaw allows attacker-controlled data to influence server-side execution when processing crafted payloads.
React Server Functions allow clients to invoke server functions, with React providing integration points for frameworks. The vulnerable code deserialises HTTP payloads unsafely, enabling unauthenticated RCE.
Affected packages (versions 19.0.0, 19.1.0, 19.1.1, 19.2.0):
react-server-dom-parcelreact-server-dom-turbopackreact-server-dom-webpack
Applications are vulnerable even without explicit Server Function endpoints. The flaw is exploitable wherever RSC is supported.
Frameworks affected by React2Shell
- Next.js (15.0.4 through 16.0.6, plus canaries from 14.3.0-canary.77)
- React Router (RSC mode)
- Waku
- Parcel RSC (
@parcel/rsc) - Vite RSC (
@vitejs/plugin-rsc) - RedwoodSDK (
rwsdk)
A standard create-next-app production build is vulnerable without modifications. Default configurations are exploitable out of the box.
What attackers can do
Unauthenticated access, remote exploitability, and React's ubiquity create extreme risk, as the maximum-severity CVSS score suggests. After achieving code execution, attackers can:
- Exfiltrate data by accessing secrets, credentials, and user information.
- Establish persistence by deploying backdoors or web shells.
- Move laterally by pivoting to internal systems.
- Deploy ransomware by encrypting data for extortion.
Unauthenticated RCE in a massively deployed framework suggests significant potential for abuse. This type of exploit can be easily automated and sweep the internet for vulnerable servers.
Detection and mitigation
Runtime detection
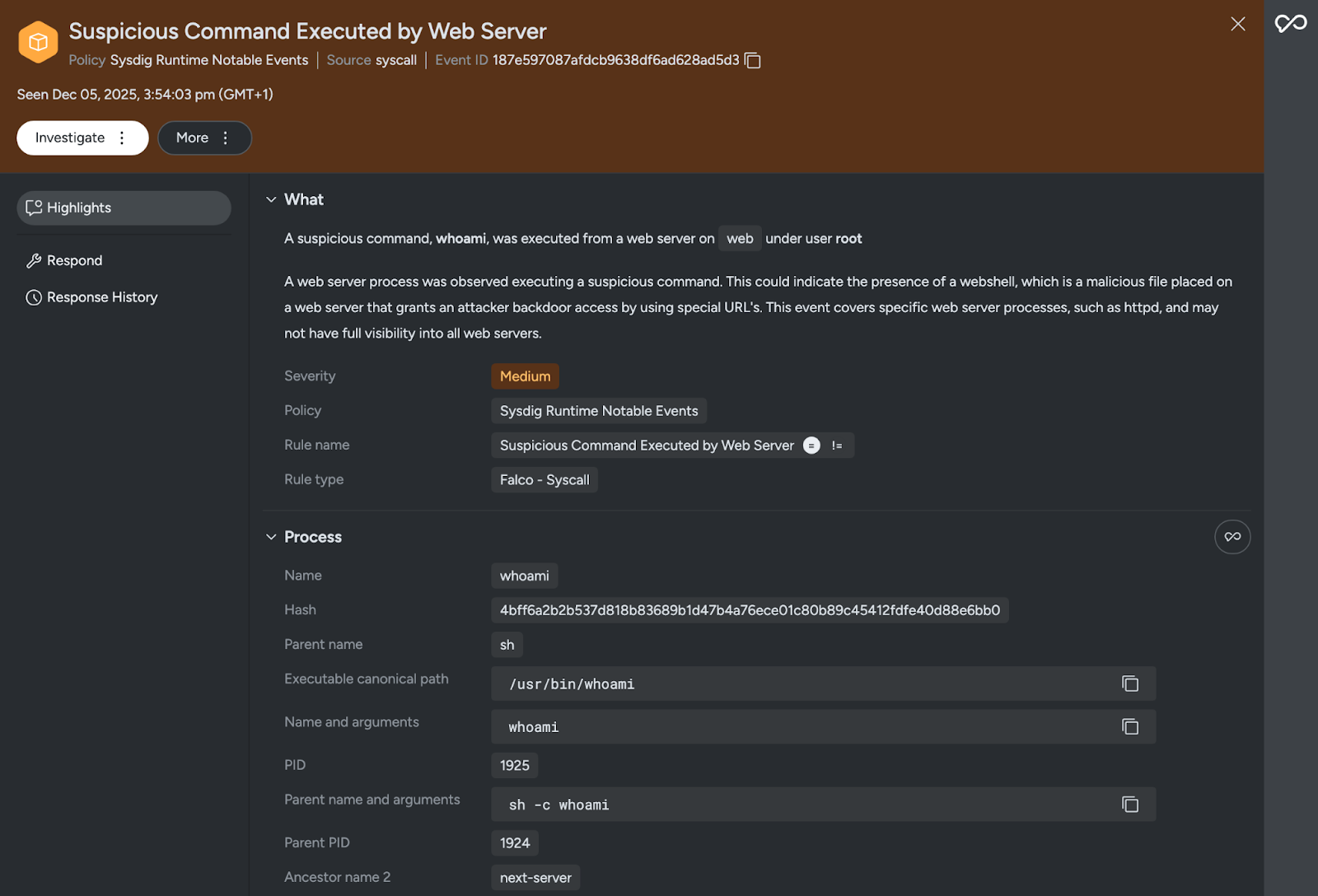
The Sysdig TRT has reinforced the “Suspicious Command Executed by Web Server” rule. This detection catches most unexpected, arbitrary commands spawned by web servers, raising alerts for Remote Command Execution in such applications. The following Falco rule can be used to detect suspicious commands. (Please note that the “proc.aname” fields may need to be adjusted for your environment. Additional commands can also be added to the minimal_unix_commands macro.)
- list: minimal_unix_commands
items: [ls, cp, mv, rm, mkdir, rmdir, find, touch, cat, less, head, tail, nano, vi, chmod … ]
- list: shell_binaries
items: [ash, bash, csh, ksh, sh, tcsh, zsh, dash]
- macro: spawned_process
condition: (evt.type in (execve, execveat) and evt.dir=< and evt.arg.res=0)
- rule: Detecting React2Shell Remote Code Execution
desc: This rule detects exploitation attempts of the React2shell vulnerability. Leveraging it, attackers can execute arbitrary commands in React applications.
condition: >
( spawned_process and
proc.name in (minimal_unix_commands) and
proc.pname in (shell_binaries) and
( proc.aname startswith 'next-server' or proc.aname startswith 'react-router' or proc.aname in (waku,vite))
)
output: Possible React2shell exploitation attempts detected with %proc.cmdline and parent name %proc.pname in %container.name under user %user.name (proc.name=%proc.name proc.exepath=%proc.exepath proc.pname=%proc.pname gparent=%proc.aname[2] ggparent=%proc.aname[3] gggparent=%proc.aname[4] user.name=%user.name image=%container.image.repository proc.cmdline=%proc.cmdline proc.pcmdline=%proc.pcmdline container.id=%container.id evt.type=%evt.type evt.res=%evt.res gcmdline=%proc.acmdline[2] ggcmdline=%proc.acmdline[3] proc.cwd=%proc.cwd proc.pid=%proc.pid proc.cwd=%proc.cwd proc.ppid=%proc.ppid proc.sid=%proc.sid user.uid=%user.uid user.loginuid=%user.loginuid user.loginname=%user.loginname group.gid=%group.gid group.name=%group.name container.name=%container.name)
priority: WARNING
tags: [host, container, network, MITRE, MITRE_TA0002_execution, MITRE_T1059_command_and_scripting_interpreter, MITRE_T1104_multi_stage_channels]
Sysdig Secure customers can find this rule in the Sysdig Runtime Notable Events policy. Other Sysdig rules have been seen triggering when this vulnerability is exploited, including Reverse Shell Detected and Reverse Shell Redirects STDIN/STDOUT Using UNIX Socket. Suspicious Command by Web Server offers more generic protection.
WAF protections
In response to CVE-2025-55182, cloud providers have deployed web application firewall (WAF) rules to block potential exploitation:
- Cloudflare deployed rules detecting unsafe deserialization in POST requests.
- Google Cloud Armor added a
cve-canaryrule. - Vercel deployed platform-level protections.
- Firebase Hosting/App Hosting is enforcing exploitation-limiting rules.
WAF rules provide defense-in-depth, but can be bypassed. Therefore, vulnerable organizations must patch the underlying code in order to comprehensively secure their environments.
Vulnerability scanning
Many PoCs on GitHub misdiagnose the root cause or fail to confirm React2Shell’s exploitability. Some even appear to be AI-generated: plausible-looking but broken. The original researcher confirmed that public PoCs differ from the actual exploit.
One organization, Assetnote, released a scanner that differentiates vulnerable from patched hosts. Their writeup details the mechanism, which sends ["$1:a:a"] against an empty object and causes vulnerable servers to return 500 with E{"digest": ...}. Patched versions, on the other hand, prevent this crash.
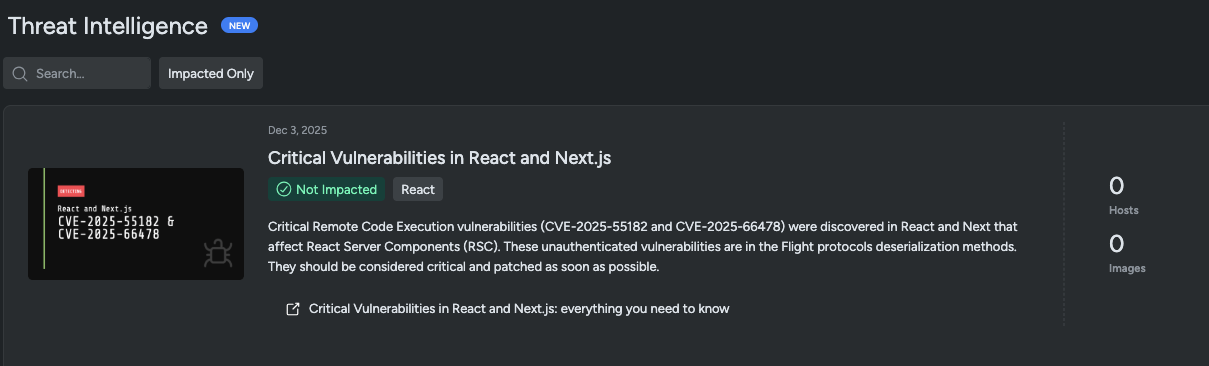
Vulnerability management in Sysdig Secure currently identifies packages affected by React2Shell. Also, the Threat Intelligence Feed within Sysdig Secure also provides immediate visibility into affected packages based on your inventory.
Remediation
Patching is the only fix for affected versions of React.
Fixed versions include:
- React Server Components: 19.0.1, 19.1.2, 19.2.1
- Next.js: 15.0.5, 15.1.9, 15.2.6, 15.3.6, 15.4.8, 15.5.7, 16.0.7
Required actions:
- Update RSC packages.
- Update Next.js to the patched version for your minor release.
- Downgrade Next.js canaries (14.3.0-canary.77+) to stable 14.x.
- Update other frameworks to the latest versions.
- Deploy runtime detections with Falco or Sysdig Secure.
- Enable WAF protections as a temporary mitigation.
Conclusion
CVE-2025-55182 and CVE-2025-66478 expose RSC applications to unauthenticated RCE. Maximum severity, default-configuration exploitability, and widespread adoption create urgent risk.
All organizations running the affected versions of React should patch them immediately. Runtime threat detections should also be deployed to detect the active exploitation of React2Shell. WAF rules can be used as temporary mitigations, but updating systems to fixed versions eliminates the risk. Teams should deploy runtime detection for environments where immediate patching isn't possible.


