Falco Feeds extends the power of Falco by giving open source-focused companies access to expert-written rules that are continuously updated as new threats are discovered.

Containers and Kubernetes have transformed how modern applications are built and deployed. While containers offer clear benefits in terms of scalability, flexibility, and speed in the cloud, they also expand the attack surface that organizations need to defend. Unpatched vulnerabilities, risky configurations, and runtime threats create constant challenges for security teams.
Most security tools weren’t designed for cloud-native environments. They miss container-specific risks, overwhelm teams with alerts, or force organizations to stitch together multiple tools. Sysdig takes a different approach. By providing end-to-end visibility across the container lifecycle, Sysdig enables teams to prevent issues before they start, detect active threats with clarity, and respond in real time.
Vulnerability management
Sysdig’s vulnerability management for containers starts with broad coverage wherever your workloads run. Sysdig scans containers across Linux and Windows, with visibility that spans the full software development lifecycle from container registries and CI/CD pipelines to production environments.
When you open Sysdig’s Vulnerability Overview, you won’t be overwhelmed by thousands of CVEs. Instead, Sysdig highlights the vulnerabilities that matter most, focusing on those that are tied to packages running in production (in use), have a fix, and have a known exploit. This runtime-aware prioritization cuts through the noise, helping teams greatly reduce their scope and focus on the issues that require immediate action.
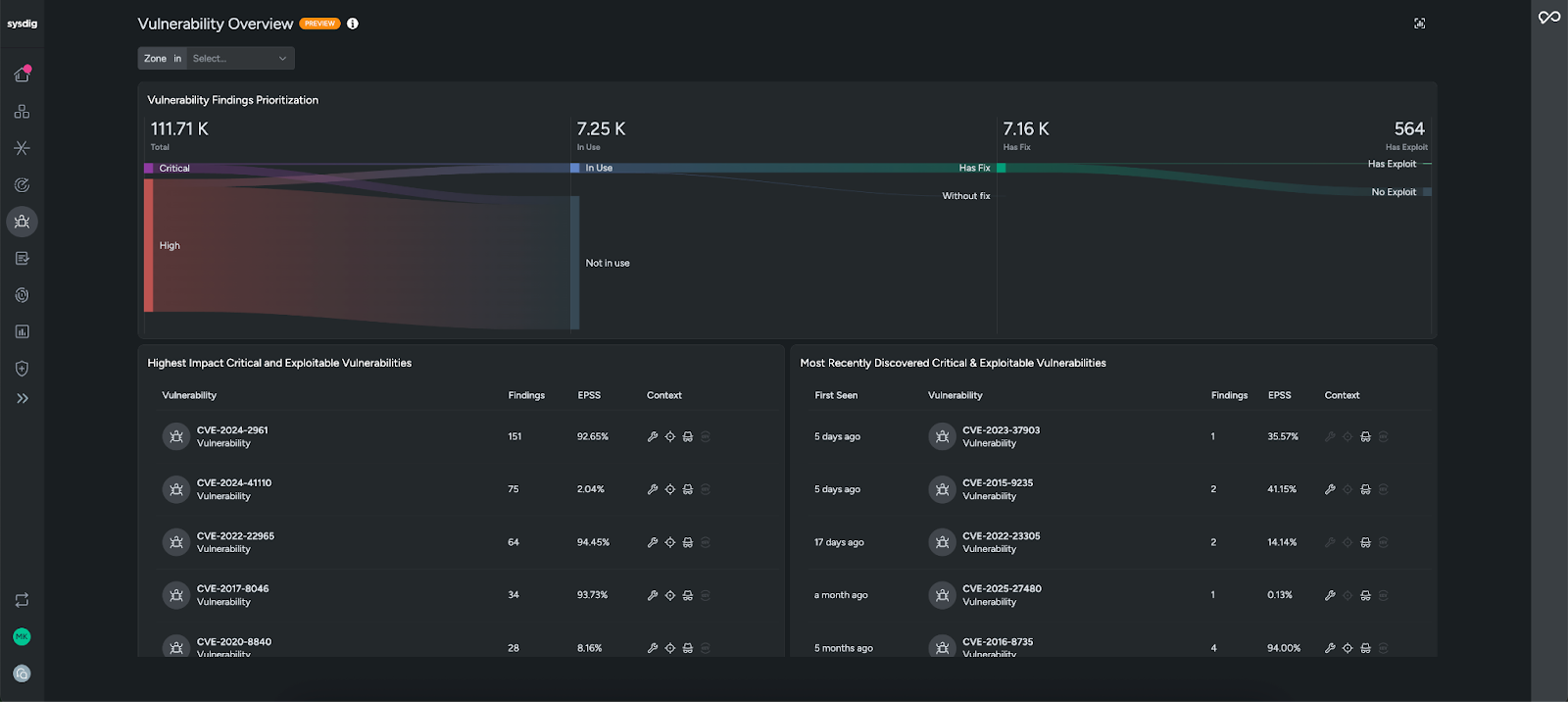
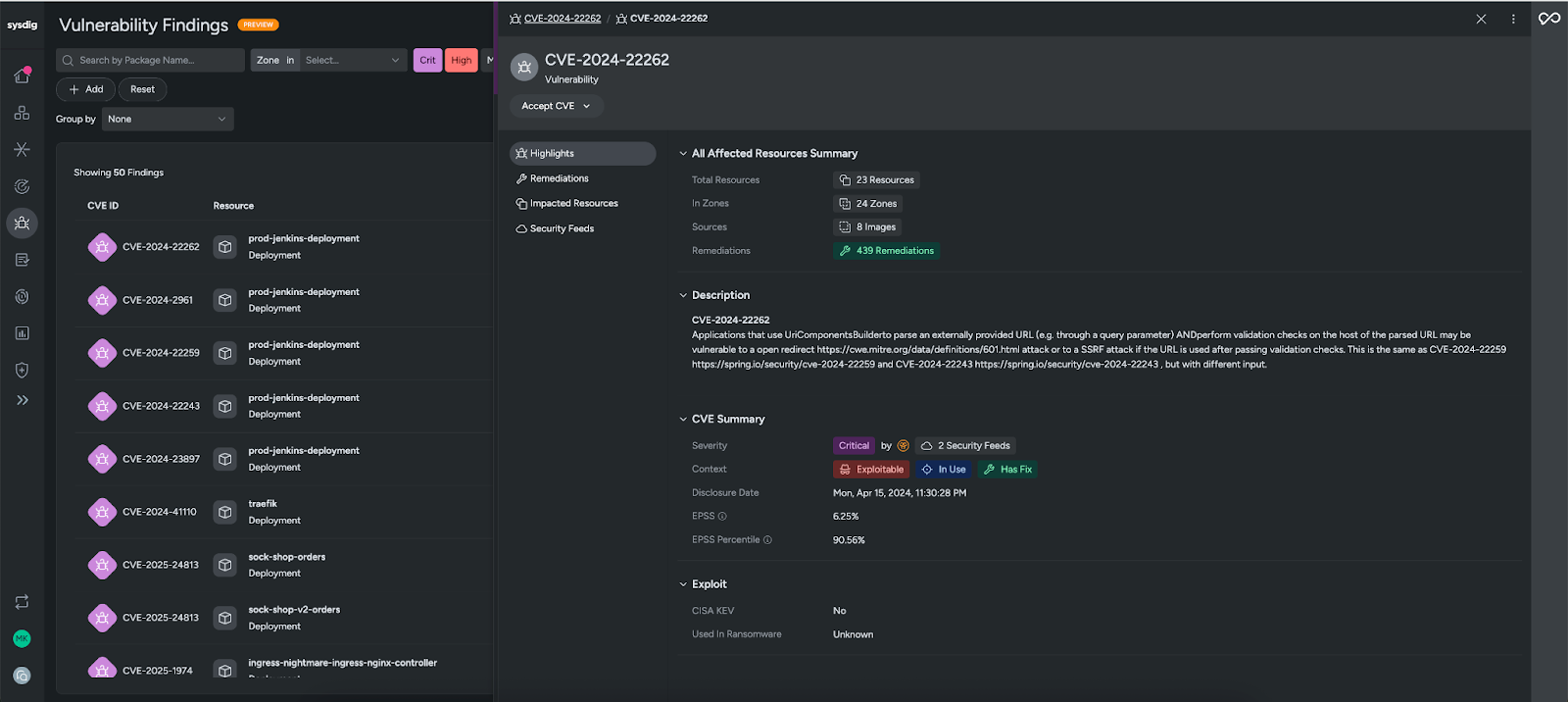
On the Vulnerability Findings page, vulnerabilities can be filtered further based on other risk criteria (e.g., exposure to the Internet). Vulnerability findings can also be grouped by CVE ID or container image. Clicking into a vulnerability provides additional context and the container it is impacting.

The CVE360 view gives complete context on all instances of this CVE throughout your environment so you can assess the scope and impact of the CVE at a glance. Relevant context like the total resources impacted, sources, and remediations helps you prioritize and understand if this is something that needs to be fixed.
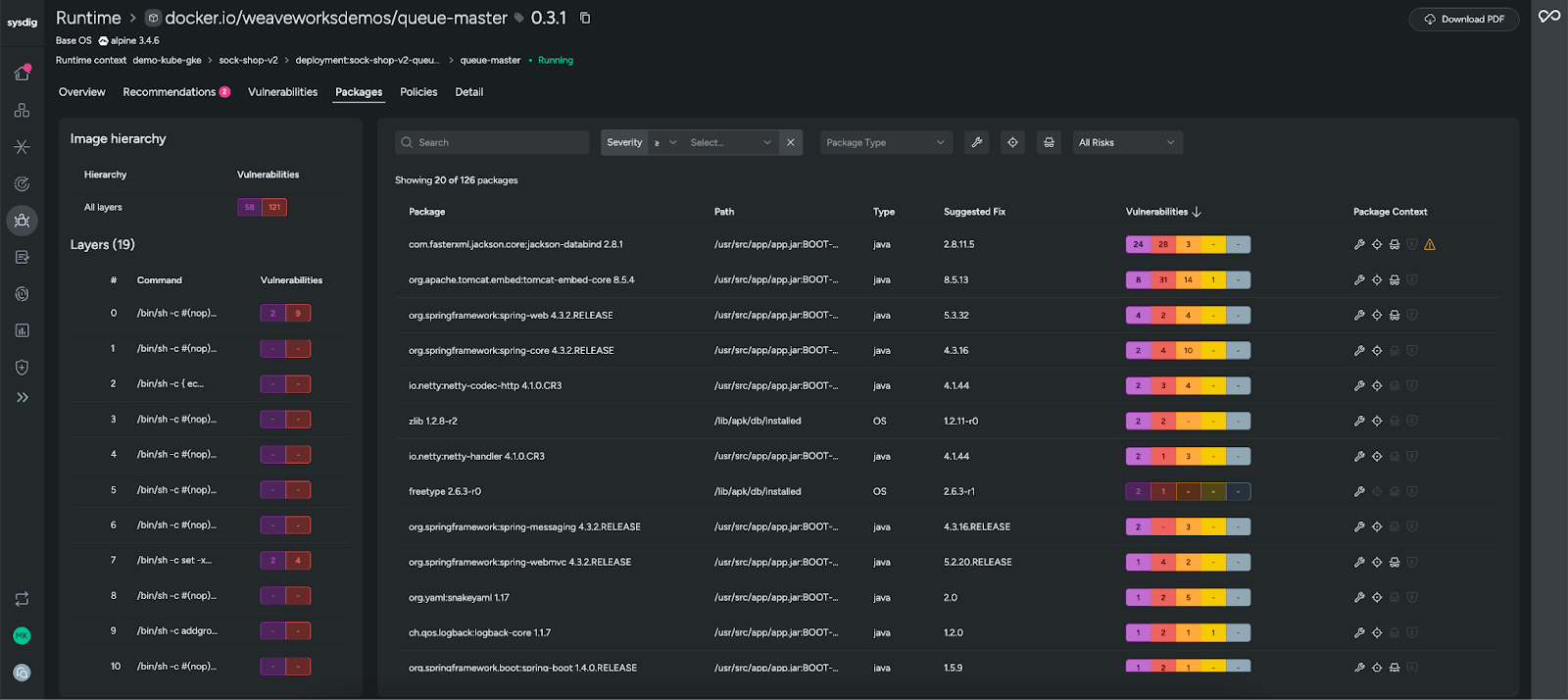
Sysdig also helps trace problems back to their source. With Layered Analysis, you can break images down by layer and pinpoint exactly where an issue originated. By fixing the problem at the source, you eliminate it everywhere it appears, making remediation faster and more durable.
When it comes to remediation, Sysdig provides actionable guidance. For container images, our AI cloud security analyst, Sysdig Sage™, generates low effort remediations that will have the greatest impact on risk reduction. Sysdig Sage turns traditional vulnerability management workflows into agentic processes, generating step-by-step instructions to remediate vulnerabilities on the container image. From here, you can automatically create a ticket and pass it along to your engineering team to remediate, which includes all of the context they will need.
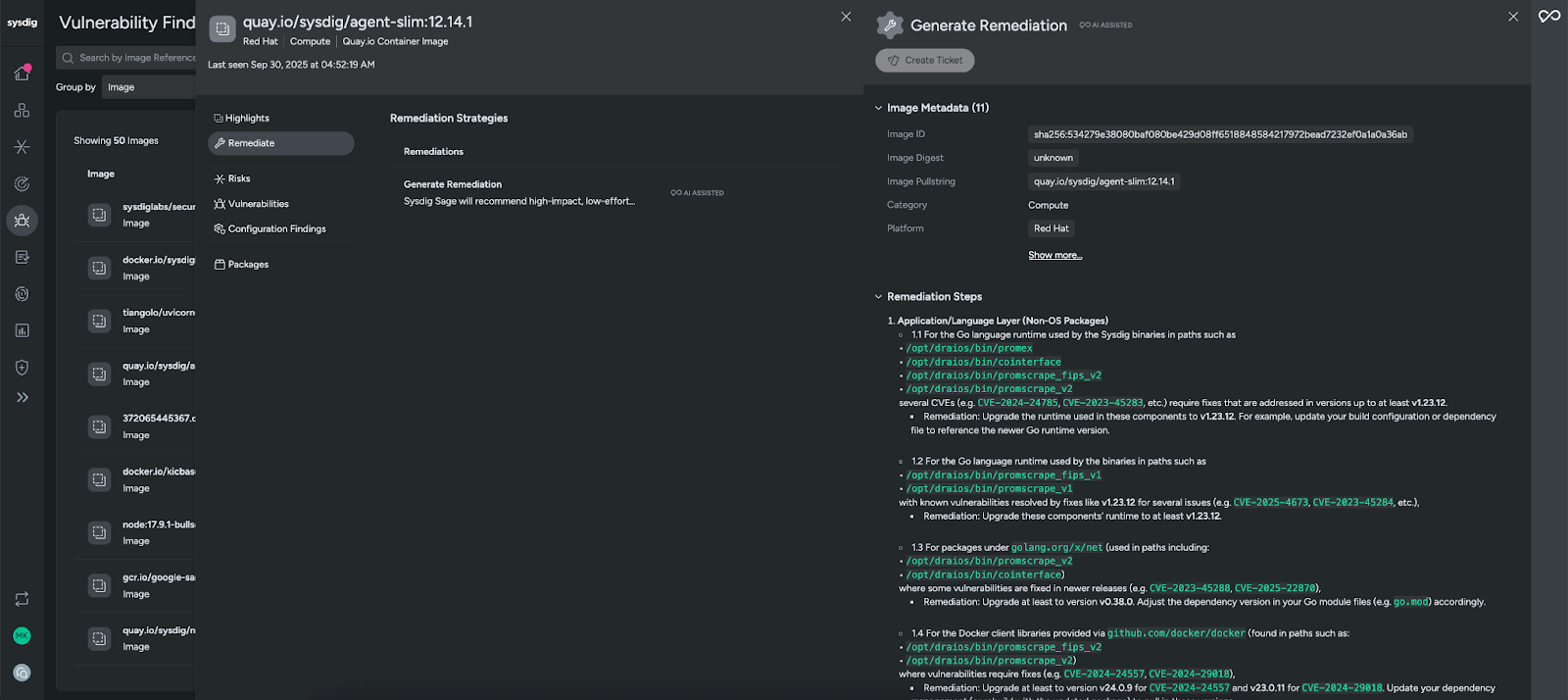
Together, these capabilities turn container vulnerabilities from a backlog of alerts into a focused, actionable workflow that reduces real risk.
Compliance and posture management
Preventing vulnerabilities is only part of the challenge. Security teams also need to ensure their environments meet industry and regulatory standards, while keeping configurations aligned with best practices. This often results in time-consuming audits, manual checks, and a constant risk of drift as environments evolve. Sysdig simplifies this by combining continuous compliance monitoring with Kubernetes security posture management (KSPM) and policy enforcement.
For many organizations, meeting compliance requirements is a critical security use case. Frameworks like PCI DSS, HIPAA, NIST 800-53, SOC 2, and CIS Benchmarks require continuous proof that your environments are secure. Sysdig makes this manageable with out-of-the-box policies mapped directly to these standards, giving you immediate visibility into where you stand.
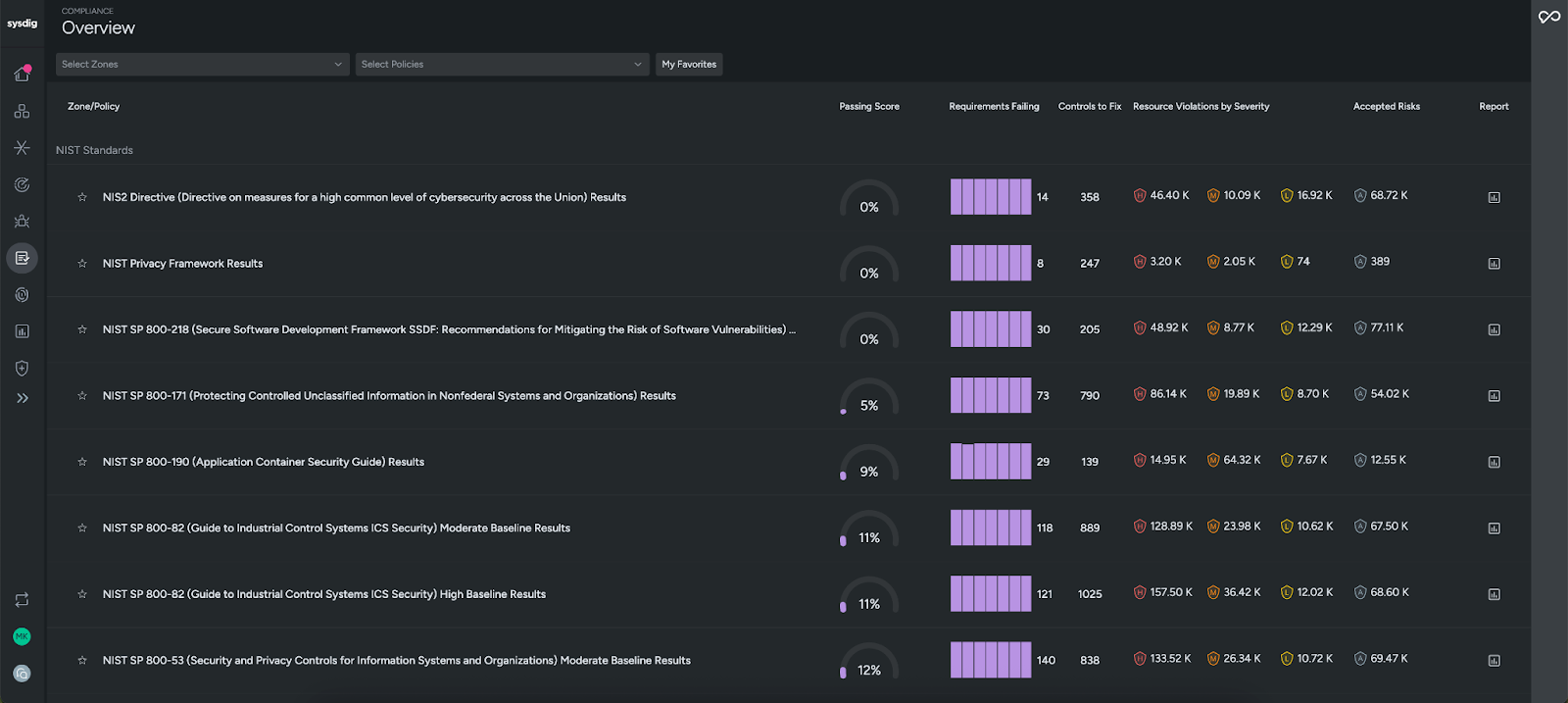
Instead of scrambling during audits, teams can generate on-demand reports in just a few clicks, monitor how posture changes over time, and drill into failed controls with clear remediation guidance. This reduces manual effort while ensuring you can demonstrate compliance to regulators, customers, and stakeholders at any time.
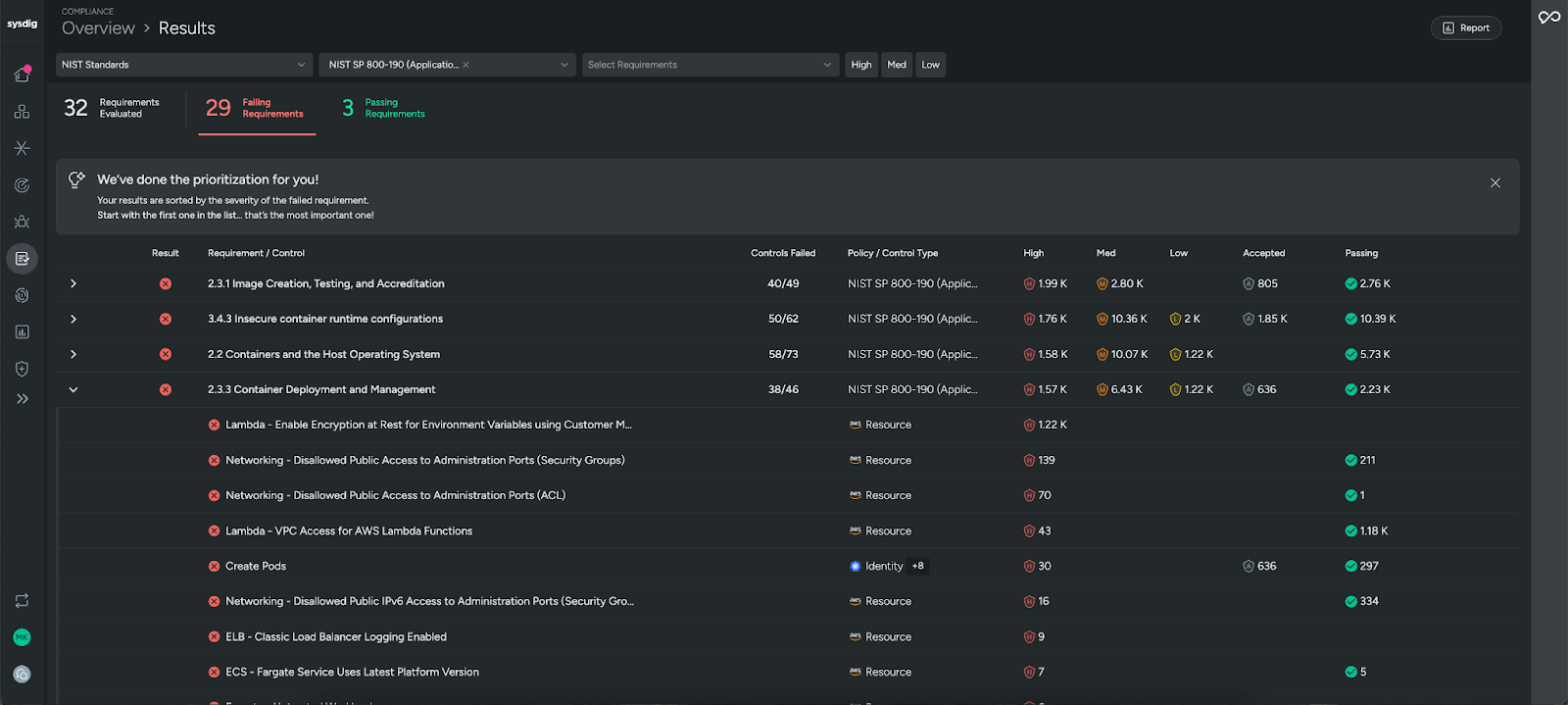
Many attacks on containers exploit Kubernetes misconfigurations such as overly permissive roles, misconfigured clusters, or privileged containers. Sysdig’s KSPM helps teams stay ahead of these risks with out-of-the-box policies mapped to Kubernetes compliance standards and best practices. Sysdig continuously checks for these risky settings, highlights issues in context, and provides guidance on how to fix them, helping you align with best practices and strengthen defenses.
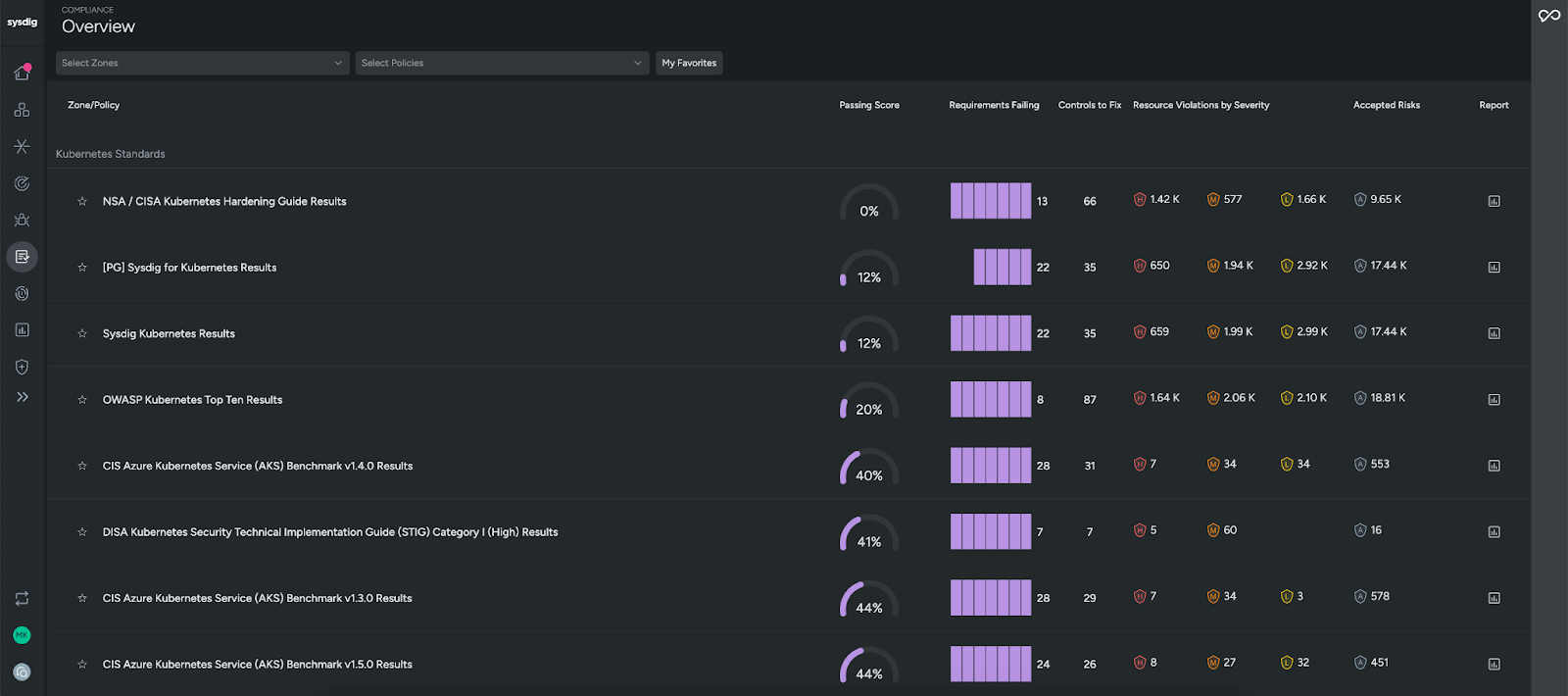
Sysdig doesn’t just flag compliance gaps or Kubernetes misconfigurations. We also make it easy to fix them. The remediation workflow explains the issue in plain language, then provides a patch generated specifically for the problem. You can apply the fix manually by copying the patch code into production, or automate the process by creating a pull request that integrates the patch directly into source code, complete with formatting checks. This flexibility helps teams remediate quickly while keeping development workflows intact.

Sysdig also helps enforce compliance and posture requirements before risky workloads reach production. With our Admission Controller, non-compliant or vulnerable deployments are blocked at deploy time, ensuring that issues don’t slip into runtime.
By combining compliance automation, posture management, and preventative enforcement, Sysdig enables teams to both prove security to auditors and improve security in practice, without slowing down development velocity.
Threat detection and response
Even with strong preventative measures in place, no environment is immune to runtime threats. Containers are dynamic and fast-moving, and attackers look to exploit misconfigurations, vulnerable packages, or exposed credentials. That’s why fast and reliable detection and response are critical. Sysdig helps teams move quickly by correlating signals into meaningful threats, giving deep visibility for investigation, and enabling rapid response actions.
Sysdig powers runtime threat detection with flexible policies built on the open source Falco rules engine. Falco continuously monitors system calls and Kubernetes audit logs and checks them against curated rules to identify suspicious activity in real time. With Sysdig, you get out-of-the-box detection rules and policies tailored for containers and Kubernetes, so you can spot threats quickly.
Sysdig’s Threat Management feature reduces noise by correlating runtime activity into prioritized incidents. Instead of hundreds of raw alerts, detection events are analyzed in real time and grouped into a clear attack or threat category.
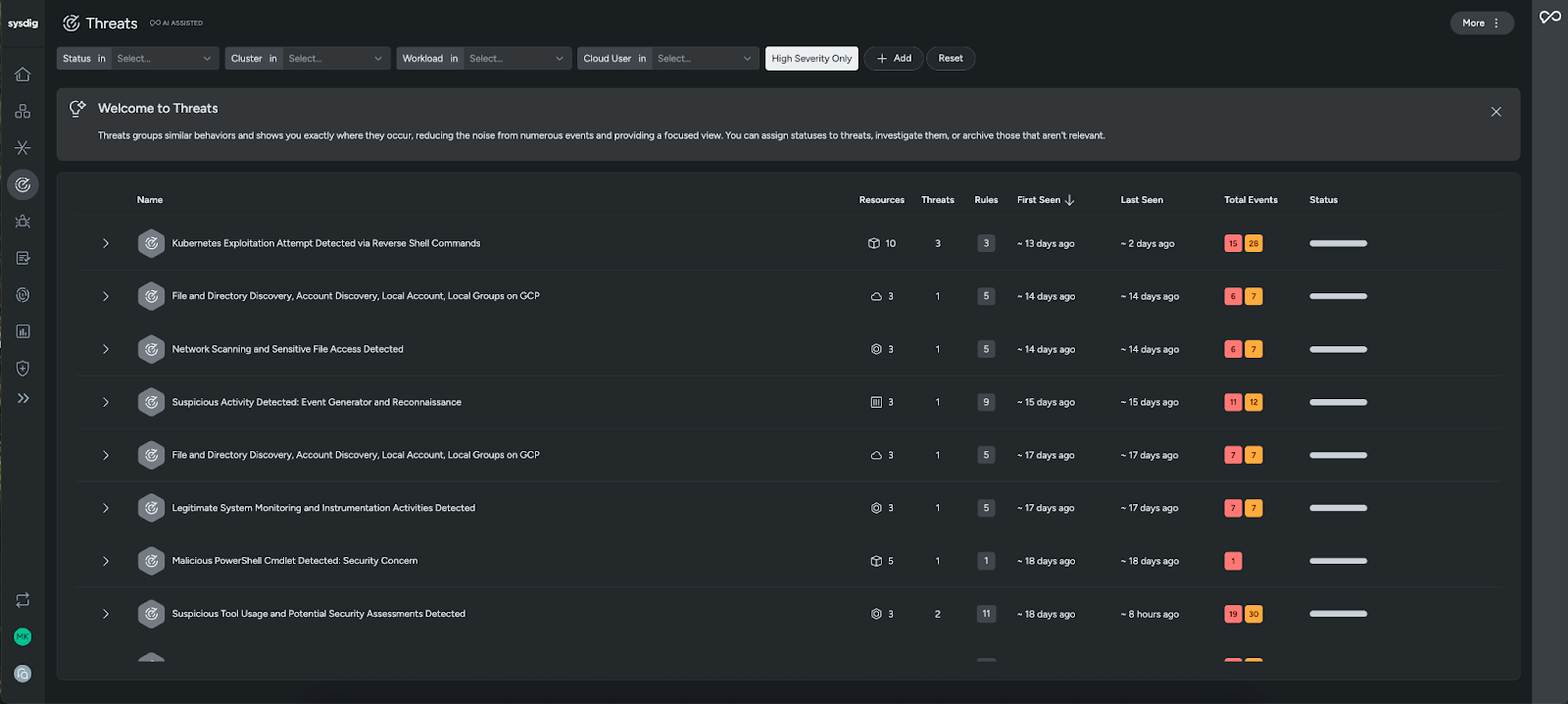
Each finding gives the full context, including what happened, which user carried out the actions, and where they occurred. Sysdig Sage enriches threats with an easy to understand summary, helping you understand potential impact and next steps immediately.

Events can also be viewed individually in the Events Feed. When suspicious behavior is detected, you can seamlessly drill into all events on the relevant container workload.
You can talk to Sysdig Sage to ask questions and get more understanding of the threat.

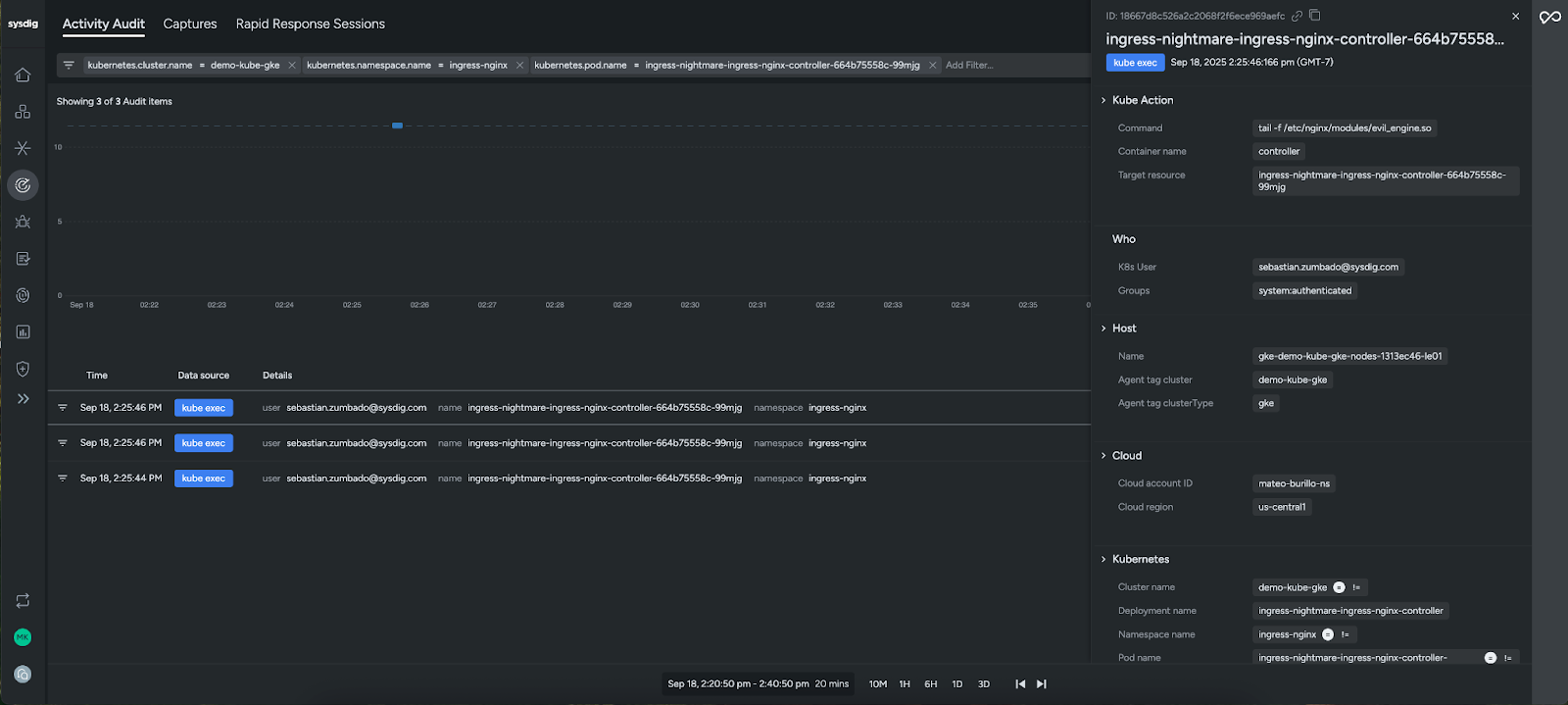
Sysdig also offers forensic analysis capabilities to investigate even after a container is gone. Activity Audit shows executed commands, file access, and network connections, while Captures let you take a system snapshot at the moment of an event for forensic analysis. Together, these capabilities let you trace an incident from the first signal all the way down to the specific system call, cutting investigation time dramatically.
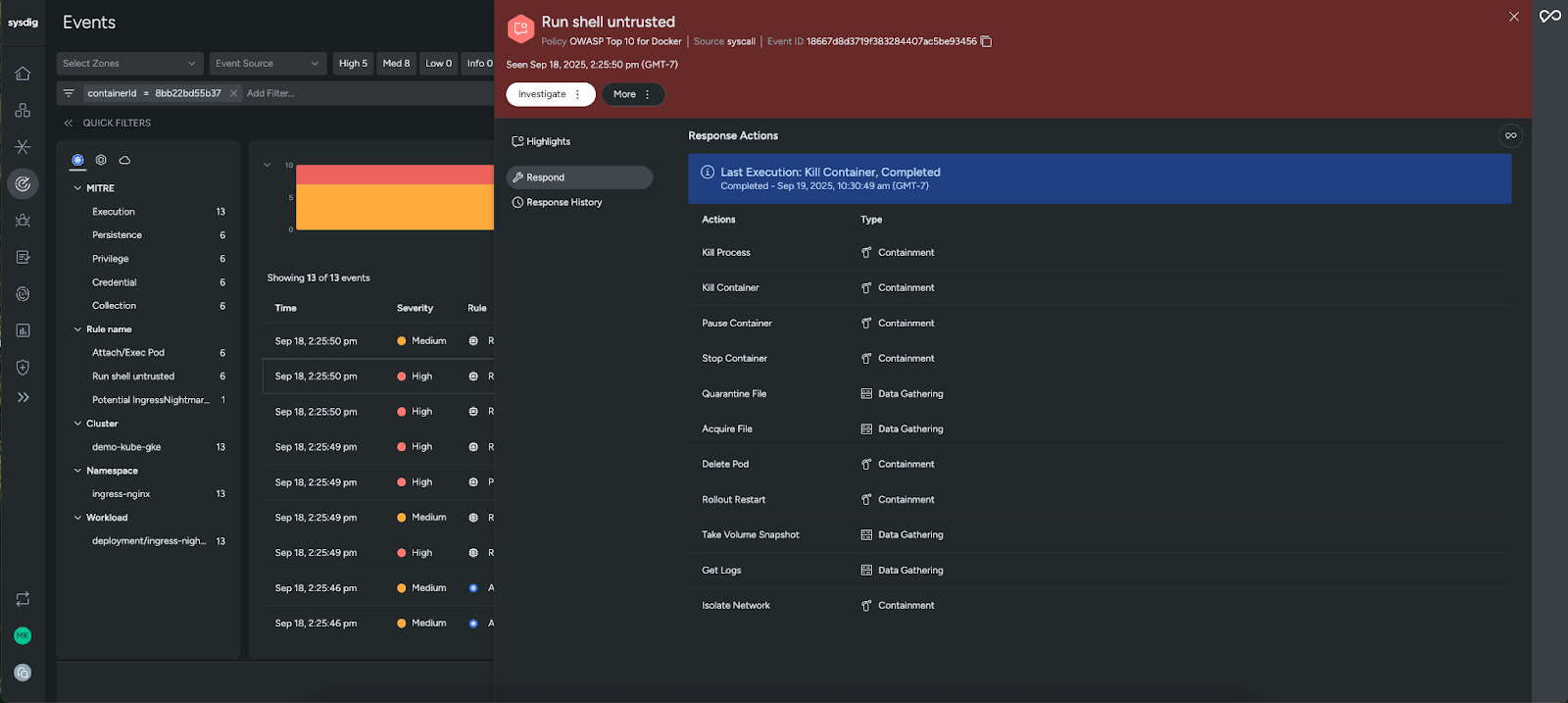
Once you’ve confirmed a threat, Sysdig makes it simple to contain and remediate. With Response Actions, you can kill or pause a container, isolate a workload from the network, or quarantine a suspicious file directly from the Events Feed. For more hands-on response, Rapid Response provides a secure remote shell so authorized users can investigate and remediate with the same commands they’re accustomed to. This flexibility allows teams to adapt response to the severity of the incident, from automated containment to deeper manual investigation.
By bringing detection, investigation, and response together, Sysdig compresses the time from first signal to containment from hours or days down to minutes — giving security teams the confidence to stop active threats before they spread.
Cloud-native demands a unique approach
Container security requires a platform built specifically for cloud-native environments. Sysdig unifies prevention, compliance, detection, and response in a single solution, giving teams the visibility and speed they need to protect modern applications. With AI-powered vulnerability management, continuous posture management, and real-time threat detection and response, Sysdig helps organizations reduce risk and stop attacks without slowing down innovation.
Want to see these capabilities in action? Request a personalized demo today to explore how our solutions align with your specific needs.


