
Falco Feeds extends the power of Falco by giving open source-focused companies access to expert-written rules that are continuously updated as new threats are discovered.

Why cloud threat detection is overwhelming without the right tools
Detecting malicious behavior in cloud-native environments can be a tedious, error-prone process, especially without tooling purpose-built for the cloud. Because of this, teams often face a flood of alerts, many of which turn out to be frustrating false positives. Existing tools struggle to track attacker behavior across ephemeral infrastructure, leading to fragmented detections that miss the bigger picture. The result? Teams risk overlooking complex, multi-step attacks, and when they do respond, it’s often too late or an incomplete response.
Sysdig delivers continuous advancements in runtime behavioral analytics
Sysdig has supercharged the Falco agent with the ability to correlate and contextualize related security events over time. This new capability, called runtime behavioral analytics, enables Sysdig Secure to remember and connect past and present signals to detect multi-stage attacks, something traditional rule-based tools simply can’t do. So instead of only stateless, single event detections, analysts are also able to work from stateful, multi event analyses.
Building on this depth in detection, Runtime Behavioral Analytics tracks sequences of suspicious actions across workloads, containers, and identities, flagging them as a unified threat. Sysdig Behavioral Analytics is a Sysdig Secure capability that constructs behavioral context from runtime data. Essentially, these capabilities enable the detection of multistep attack patterns and the generation of runtime policy events.
Real-world example: How runtime behavioral analytics works
Let's say a user is downloading a file. This process alone might not raise eyebrows, especially if you have a noisy environment. But if that file is being downloaded to the /tmp directory, and that file is being executed in a short period of time, this begins to look very suspicious. Instead of viewing each of these steps as isolated behaviors, or even siloed with different analysts, Sysdig stitches them together and surfaces a unified threat narrative.
For the example above, the analyst would rapidly gain the following understanding:
This rule detects the dropping of a file by an ingress tool, such as curl, and its subsequent execution in the /tmp location. This may indicate successful attempts to download and run a potentially malicious binary.
Why is this behavior viewed as risky? Using /tmp for defense evasion purposes allows the attacker to live in the shadows. After all, /tmp files are rarely deleted by others, providing persistence within the attackers timeline, where they can simply delete the file later to cover their tracks. Stealth is achieved through these standard file types blending in with legitimate activities, making them less likely to face scrutiny. From the /tmp file, attackers can execute as they see fit, be it malware, bitcoinminers, or initiating data exfiltration.
Behavioral analytics adds additional detections used to compose Threats, within Sysdig Threat management
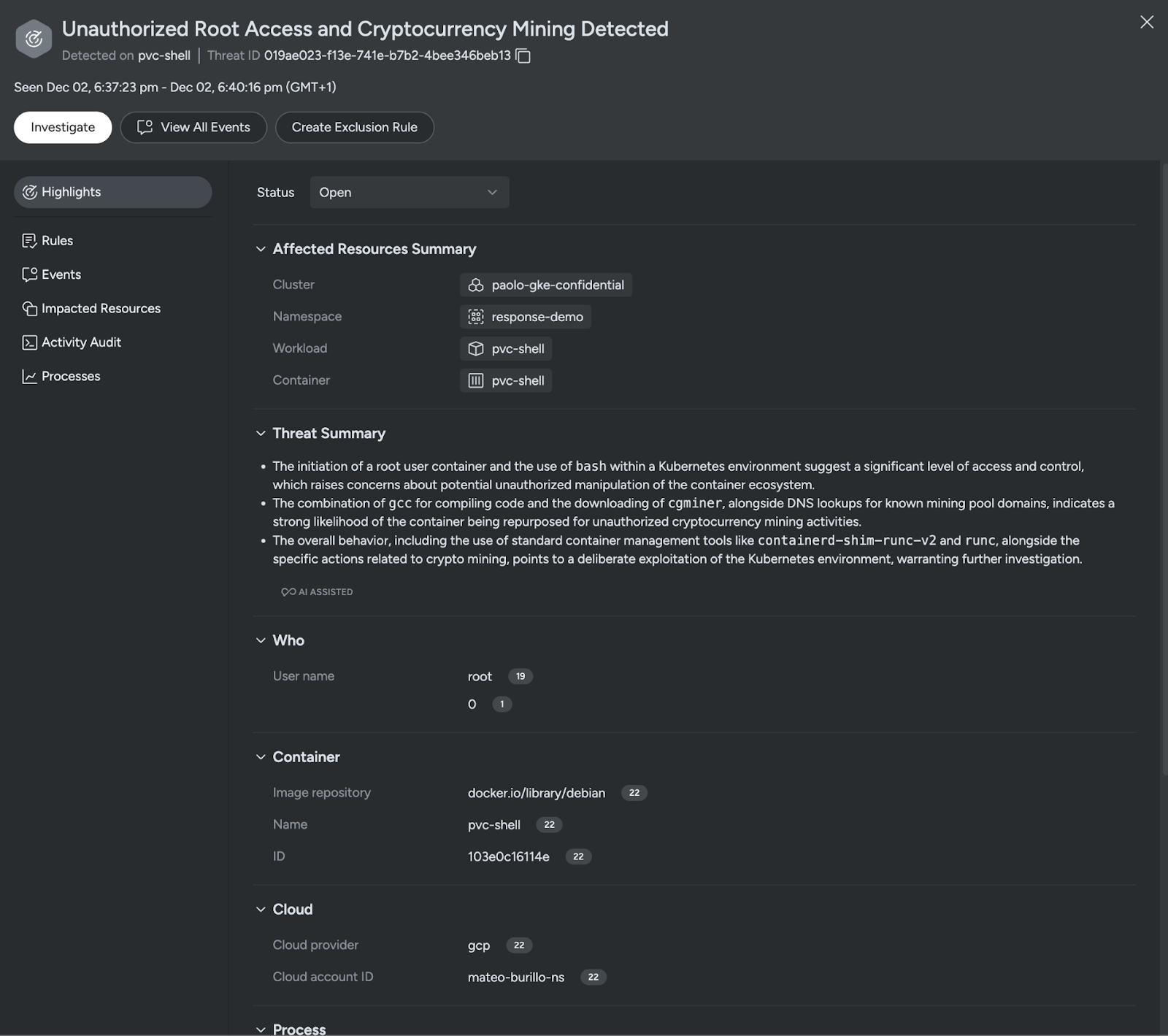
In this case, looking at the events composing this Threat, we notice that a key event was a binary dropped in /tmp and executed from that location.

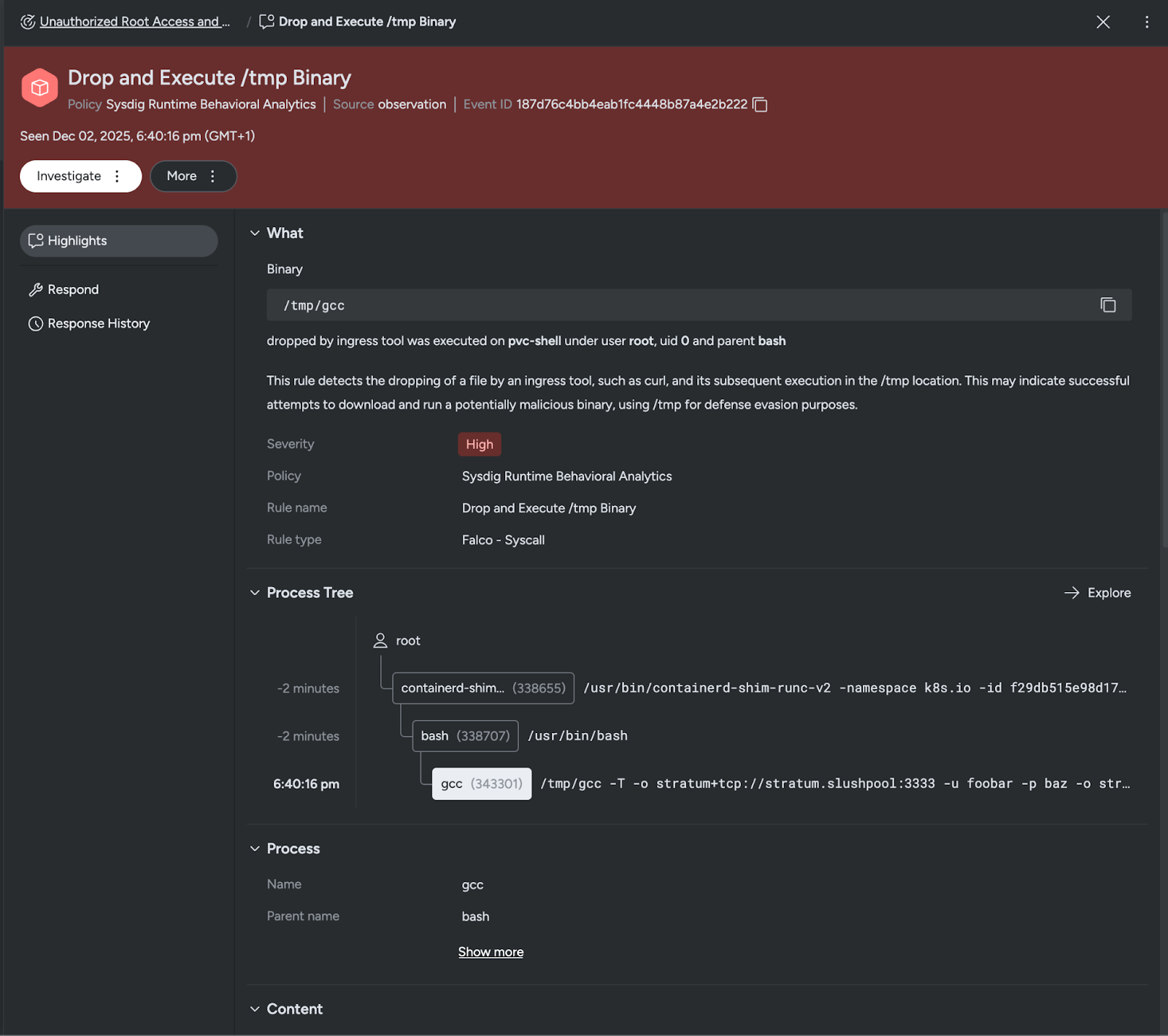
Expanding the event, we can see all the details: what actions were executed, by whom, where and even gain details through the process tree.
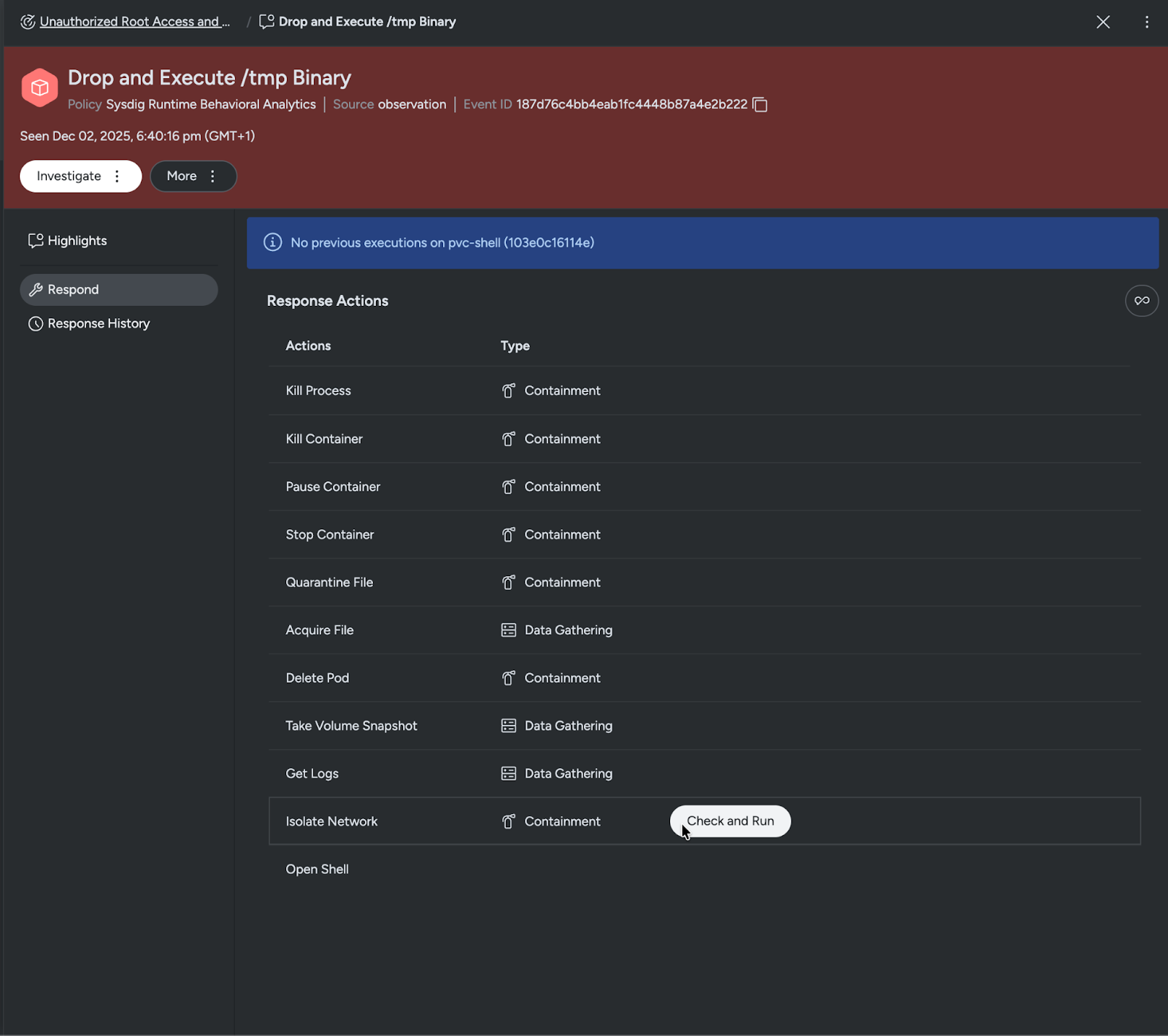
After the initial analysis and if appropriate, teams can seamlessly trigger inline response actions, to gather additional information or stop the ongoing threat, all within Sysdig Secure.
Real-world scenarios detected
Sysdig Runtime Behavioral Analytics detects sophisticated threats that often slip past traditional tools. A few examples include:
Staged Meterpreter reverse shell
Detects binaries used in exploit chains that stage lightweight payloads before initiating full shell access.
Dynamic linker hijacking (LD_PRELOAD)
Flags shared object creation followed by suspicious LD_PRELOAD behavior used for stealthy code injection.
Process injection via PTRACE
Identifies manipulation of running processes to inject malicious code — commonly linked to privilege escalation.
Data exfiltration via DNS
Tracks encoding, compression, and outbound DNS activity — often a red flag for stealthy data leaks.
Why runtime behavioral analytics matter
By observing behaviors over time instead of just firing on every event, Sysdig Runtime Behavioral Analytics reduces risk, enhancing complex threat detection and connecting the dots for multistep attack visibility. This shift from event-driven detection to context-driven analytics means security teams can move faster, miss less, and investigate smarter, putting them on the path toward achieving the 555 Benchmark (5 seconds to detect, 5 minutes to triage, 5 minutes to respond). This acceleration into the 555 Benchmark translates into a reduced mean time to response (MTTR). The overall reduction in noise and increases in operation efficiencies also lowers overhead costs.
The big picture
Sysdig’s Runtime Behavioral Analytics expands detection capabilities in cloud-native environments where complexity and ephemerality are the norm. The Sysdig Behavioral Analytics continuous innovation strengthens the core of Sysdig Secure runtime detection and response, making it easier to catch what others miss without drowning teams in noise.
From noise to meaningful detections, Sysdig delivers runtime detection and response, the right way.


