
Falco Feeds extends the power of Falco by giving open source-focused companies access to expert-written rules that are continuously updated as new threats are discovered.

Earlier this week, a widespread NPM supply chain attack was discovered, leveraging a novel worm known as Shai-Hulud that rapidly infected hundreds of packages. Unlike most NPM attacks, this malware was self-propagating, stealing credentials and replicating itself across additional packages. The incident underscored just how quickly threats in open source ecosystems can escalate, and why organizations need visibility into emerging risks the moment they appear. The Sysdig Threat Research Team (TRT) has been monitoring the worm’s progress to ensure customers can quickly understand their exposure and respond with confidence.
Shai-Hulud is just the latest reminder of how package registries like NPM have become a high-value target for adversaries. NPM is the largest software registry for JavaScript, and millions of developers depend on it every day. A single malicious update to a widely used package has the potential to cascade across thousands of applications and organizations.
That’s where the Sysdig Threat Intelligence Feed comes in.
Real-time intelligence on active threats
Sysdig’s Threat Intelligence Feed gives users a real-time view of new and widespread threats. Authored by the Sysdig TRT, each feed entry provides:
- Clear threat summaries: whether it’s malware, a CVE, or supply chain risk
- Impact confirmation: insight into whether the user’s environment is impacted
- Direct investigation link: graph search queries to pinpoint affected workloads, packages, identities, or hosts
This approach helps security teams accelerate response when impacted and avoid wasted time on false positives when they’re not.
Top malicious NPM packages
To help organizations stay ahead of fast-moving supply chain attacks targeting NPM, Sysdig provides dedicated feed entries focused on malicious NPM packages. This includes regular updates on the Top 20 Malicious NPM Packages, along with coverage of notable incidents like the Shai-Hulud worm.
The Sysdig TRT continuously monitors the ecosystem for weaponized NPM packages using proprietary technology that leverages runtime threat detection. When threat actors attempt to abuse popular repositories, Sysdig identifies those packages and surfaces the impact in a single view.
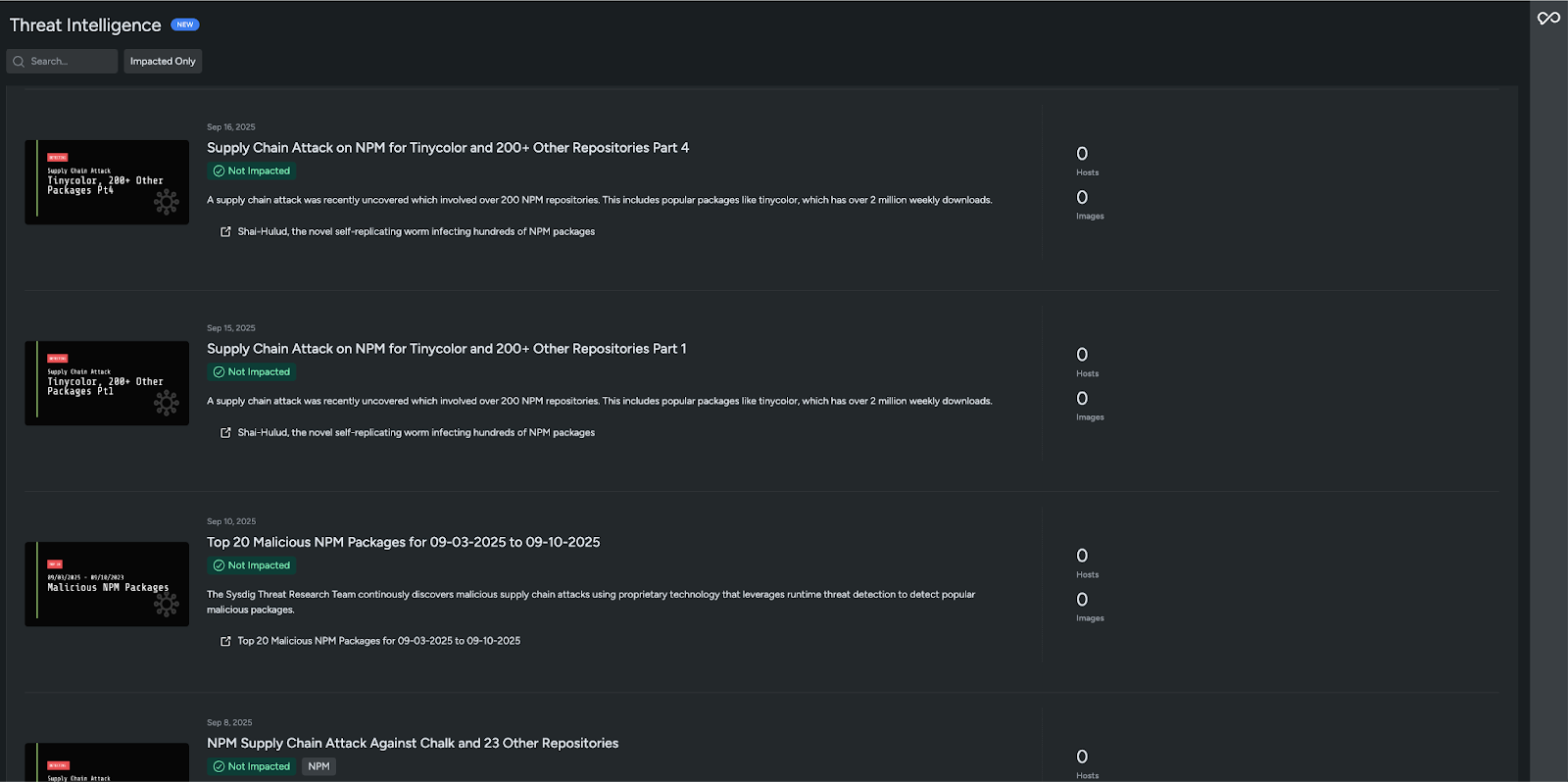
With this intelligence, users can quickly see the latest high-risk malicious NPM packages identified by Sysdig and run queries to check whether these packages are present in their environment. Security teams can confidently determine whether they are impacted or safe.
Why it matters
Supply chain threats are evolving. The Shai Hulud worm demonstrated how quickly an attacker can abuse open source ecosystems to spread malicious code at scale. Even less sophisticated attacks involving a single compromised package or credential theft can have far-reaching consequences.
By integrating malicious NPM package intelligence directly into the Threat Intelligence Feed, Sysdig ensures that customers don’t just learn about these risks after reading about these events. Instead, they can immediately verify exposure in their own environments and take action.
Stay ahead of supply chain threats
Supply chain attacks continue to be one of the most effective strategies for threat actors, and NPM packages will continue to be a prime target. The challenge for security teams is cutting through the noise, knowing immediately whether a new threat affects them and where to act.
With the Sysdig Threat Intelligence Feed, teams can zero in on what truly matters. Intelligence is immediately actionable, allowing users to move from insight to investigation in a single click. Just as importantly, the feed provides confidence when environments are safe, helping reduce unnecessary triage and wasted effort.
In the face of evolving supply chain threats, speed and precision make the difference. The Threat Intelligence Feed brings both to your fingertips.
Want to see Sysdig Secure in action? Request a demo today!


