
Falco Feeds extends the power of Falco by giving open source-focused companies access to expert-written rules that are continuously updated as new threats are discovered.

Kubernetes is the foundation for modern cloud-native applications — but it also introduces scale and complexity that shift security requirements. Infrastructure and containers spin up and down in seconds. Workloads move dynamically across clusters. Misconfigurations and zero-days can emerge faster than teams can react.
This is where agentic AI for cloud security is quickly becoming a useful tool to help teams secure what matters fast. Agentic AI reshapes Kubernetes security and cloud workload protection, guiding teams to informed decision points that drive immediate action toward successful security outcomes.
The challenge: Scale, skill gaps, and signal overload
Cloud security teams are under immense pressure. A global shortage of skilled security professionals is impacting our ability to manage all of the exposures and risks that threaten cloud-native environments. Every new deployment, every Helm chart, and every RBAC update expands the attack surface.
Meanwhile, adversaries are using AI to automate reconnaissance, exploit vulnerabilities more quickly, and conceal their movements within ephemeral workloads. The result? Security teams drown in alerts, struggle to distinguish signal from noise, and leave themselves open to risk.
If there has ever been a moment when enterprises need a better way to achieve their security goals, it is now.
Securing Kubernetes - from generative to agentic AI
Generative AI has made a big impact on helping security teams get faster insights to accelerate cloud security — summarizing threats, guiding investigations, and pinpointing misconfigurations. Agentic AI goes a step further. It’s not just conversational; it’s actionable.
With agentic cloud security, AI agents independently identify, prioritize, and even assist in remediating issues across cloud and Kubernetes environments. They act as tireless teammates, continuously analyzing, prioritizing, and suggesting, at machine speed and scale.
Imagine a virtual security analyst that proactively delivers not just alerts about something bad in your Kubernetes estate, but actually does work on your behalf, sorting through signals, data, and all the relevant context to illuminate risk and propose remediation steps automatically.
This isn’t the future — it’s what agentic AI is delivering right now.
Agentic cloud security powered by Sysdig Sage™
At Sysdig, this transformation is already underway with Sysdig Sage™, our agentic AI cloud security analyst. Sysdig Sage enhances speed, precision, and confidence across every stage of the security lifecycle.
Sysdig Sage: Key capabilities
- Vulnerability triage and remediation: Helps teams focus on the vulnerabilities that truly matter and guides remediation to resolve issues fast.
- Posture insights: Interprets plain-language queries about infrastructure, workloads, and services to simplify exploration of cloud risk.
- Threat investigation and response: Interprets security alerts, surfaces business risk, and prescribes actionable steps to stop threats before they escalate.
As part of the Sysdig cloud-native application protection platform (CNAPP), Sysdig Sage acts as a force multiplier for DevSecOps, embedding AI directly into investigation, triage, and remediation workflows. You gain instant access to the context you need, achieving in minutes what used to take hours.
Next, let’s look at three domains of securing Kubernetes — vulnerability management, Kubernetes posture management, and runtime security — to see how AI built on an autonomous agents architecture empowers users to accelerate not just awareness, but also response.
Getting ahead of CVEs with agentic vulnerability management
One of the biggest headaches in Kubernetes security is dealing with common vulnerabilities and exposures (CVEs) found in container images. Traditional vulnerability management is full of friction. It’s notoriously tedious. There are too many vulnerabilities and far too many manual steps. Most organizations spend more time prioritizing a long list than they do actually fixing the issues. With agentic AI working on your behalf, you can address this problem head-on. Here’s how we’re doing it at Sysdig:
Remove the noise
The first step is cutting through the clutter, not as the final goal, but as the foundation for meaningful action. Agentic AI can perform multiple steps to identify true business risk for you. This is work that someone is likely performing today, bouncing between vulnerability lists, a configuration management database (CMDB), and potentially even spreadsheets to identify what really matters.
As a first step, using semantic analysis, an AI agent can identify and categorize key Kubernetes context such as production vs. staging vs. development, application types, and other key insights valuable for filtering a long list of critical CVEs.
Because Sysdig captures critical insights, such as configuration and runtime usage, another step that AI agents can take on your behalf is to prioritize vulnerable packages that are in use, exposed externally, and known to be exploitable.
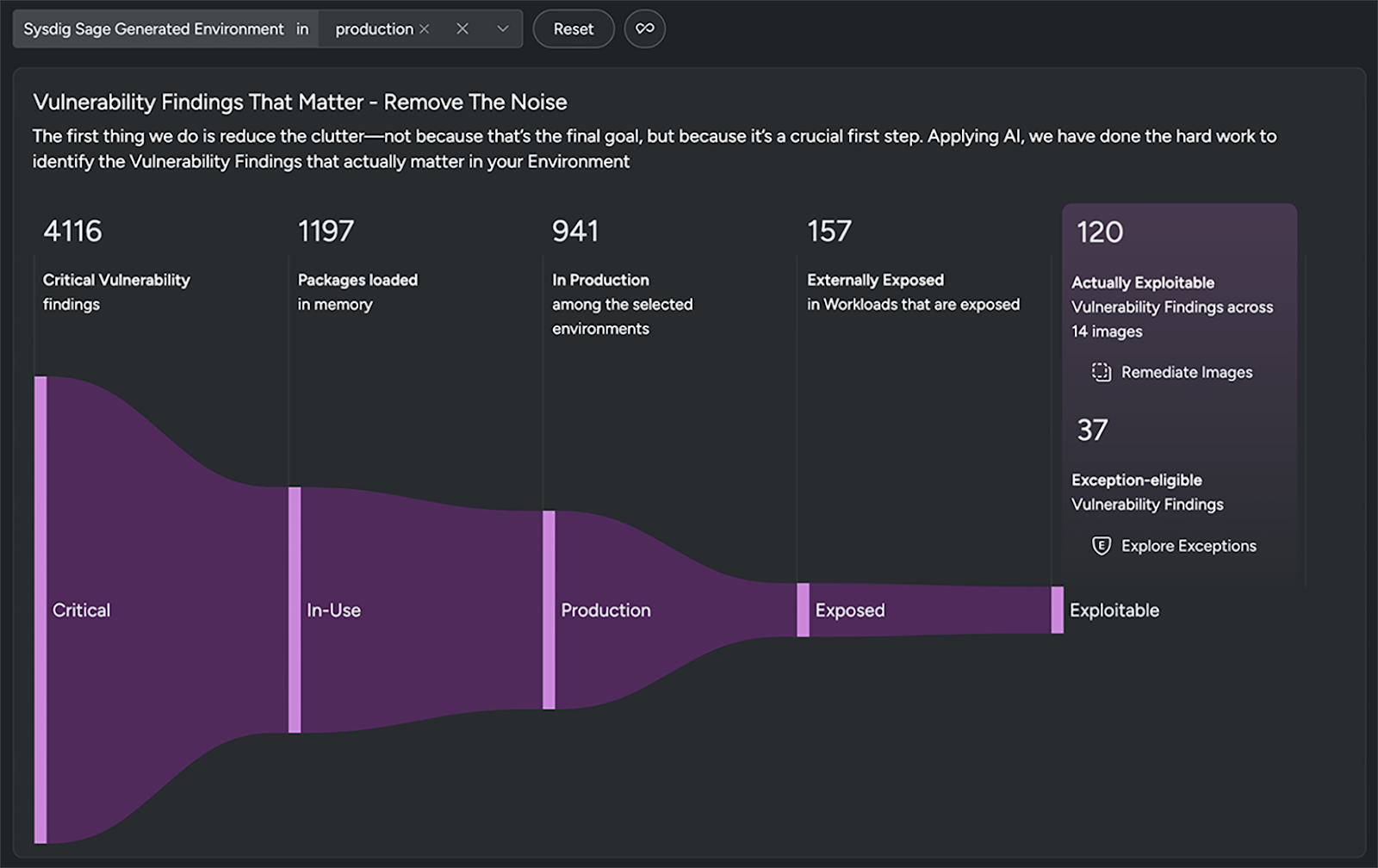
AI handles the triage, so you don’t have to. In the end, by correlating insights and filtering the long list of CVEs, agentic AI is able to focus you directly on a much smaller list, often reducing the noise by up to 95%.
For every stage, you can ask AI to explain and immediately get a clear, contextual description of the work it performed, why certain vulnerabilities are considered business-critical, and why, for some, some vulnerabilities are worthy of exceptions.
Focus on remediation impact
After arriving at a much more reasonable list of CVEs to address, AI can also help you zero in on high-impact actions. Agentic AI automatically identifies the impact that fixing a particular container image can make on your list of findings.
For example, fixing a single image with seven critical vulnerabilities might reduce 7,000 findings across your environment and address 20% of your overall risk because the image is widely used across many clusters. The result: faster decisions, less wasted effort, and reduced risk.
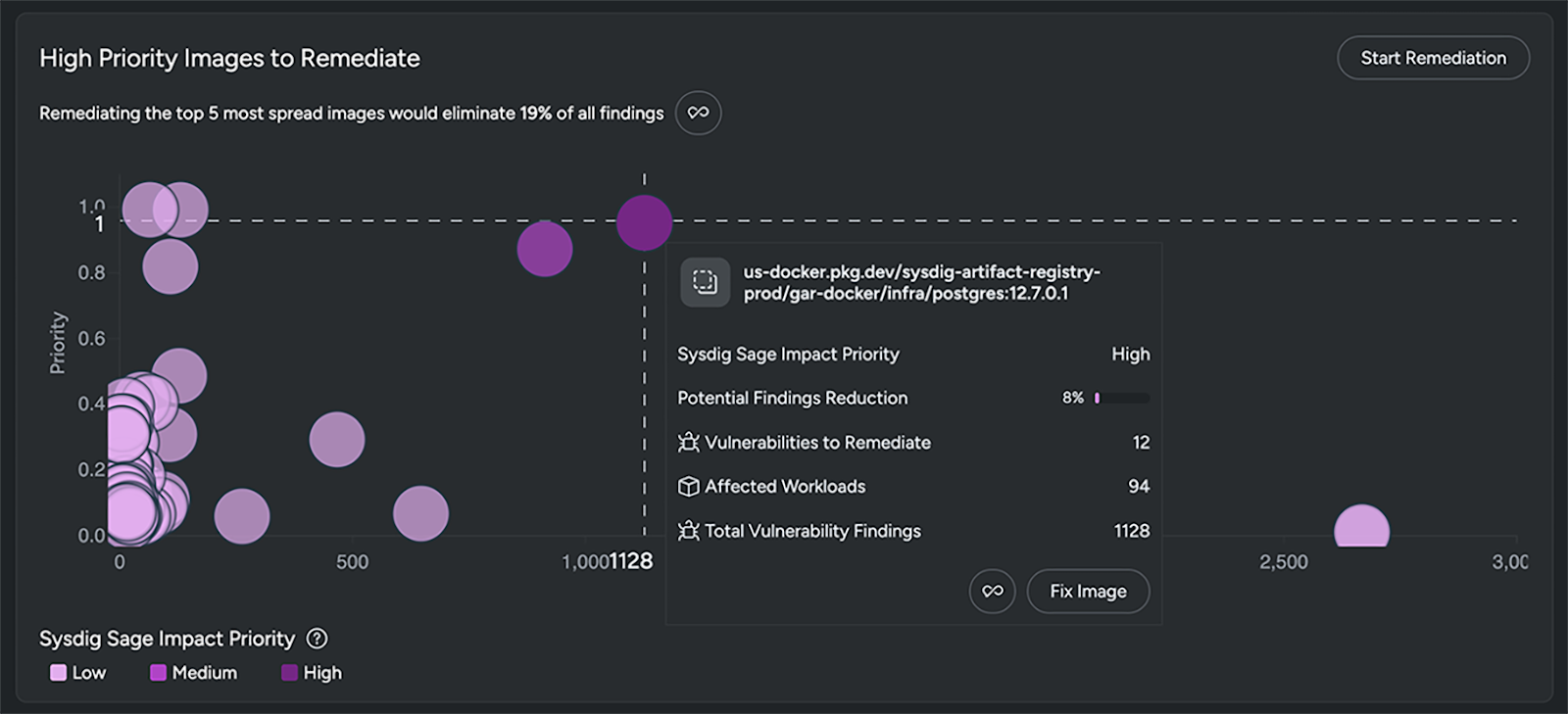
Accelerate remediation
As a final step, AI can provide your developers with guidance on how to address the relevant CVEs. AI is aware of vulnerabilities from advisories and forums, and other sources where they are explained. Using these insights, agentic AI can generate remediation instructions for your application layer and base image layer, giving clear and specific guidance tailored to your environment.
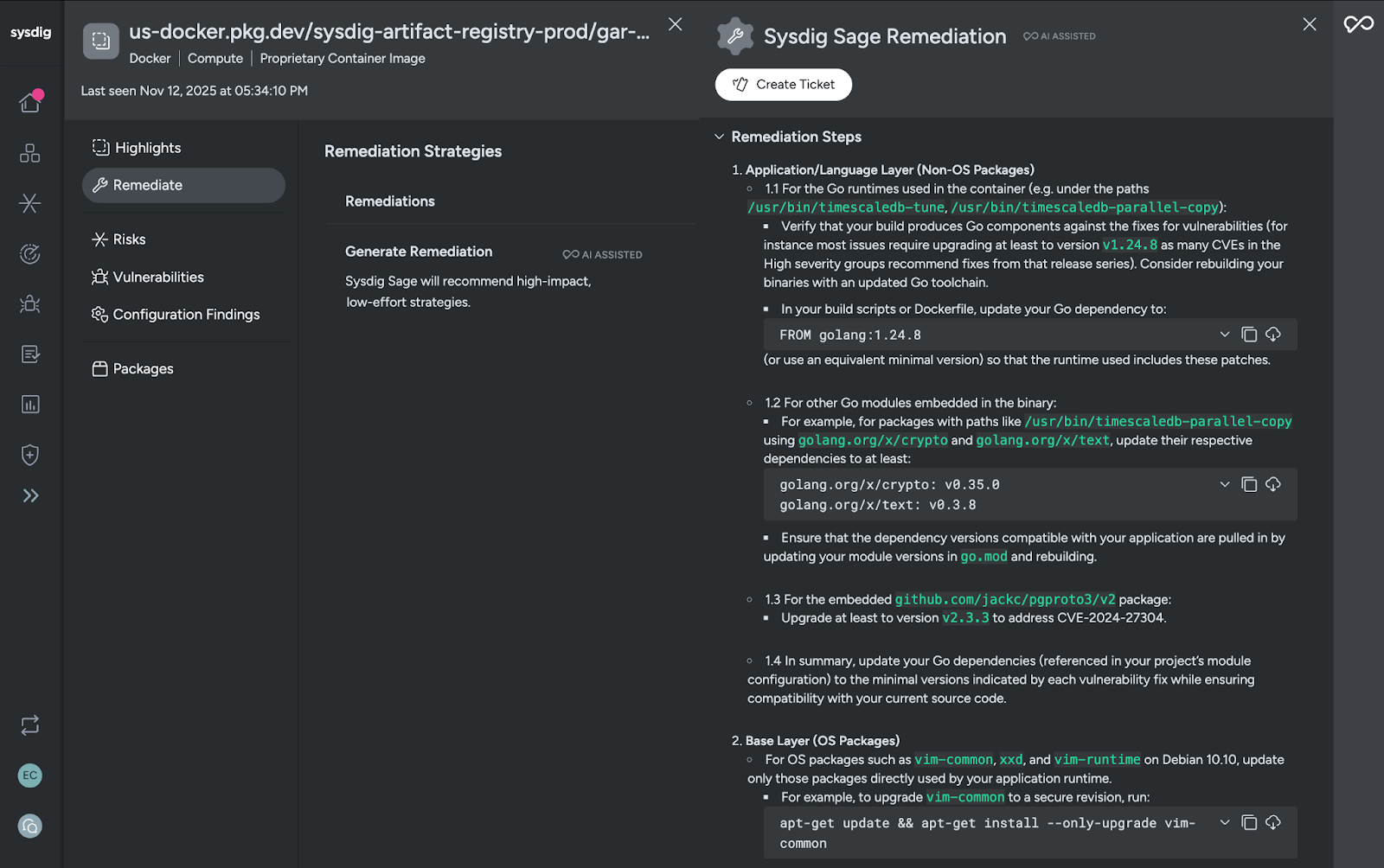
Through integration with ticketing such as Jira, AI can automate ticket creation and open an issue pre-filled with all relevant fix information and image context.
Remediation isn’t just about fixing; it’s about showing progress. Agentic AI can automatically track progress and plot metrics that help visualize the impact made on vulnerability risk exposure. Ultimately, agentic AI enables security teams to shift from reactive ticket triage to strategic improvement.
Identifying Kubernetes posture risk with AI
Another critical aspect of Kubernetes security is managing the defense of clusters and workloads by monitoring for and correcting misconfigurations. Kubernetes security posture management (KSPM) helps you evaluate configurations, check against compliance requirements, and identify risks.
Security software providers, such as Sysdig, have developed solutions utilizing graph databases to simplify the mapping of relationships between Kubernetes resources, containers, users, security configurations, and risk.
Employing AI as a graph search assistant gives users an easier way to interact with and extract insights from their Kubernetes security data. You can simply express security questions in natural language, which are automatically interpreted and translated into queries that help you seamlessly explore the state of your Kubernetes estate and workloads. In this case, AI helps you to:
- Understand how Kubernetes components interact and affect each other
- Target security findings and configurations for security analysis
- Perform context-driven compliance analysis
AI bridges the gap between investigative goals and the vast amount of low-level data, accelerating posture management workflows such as policy validation.
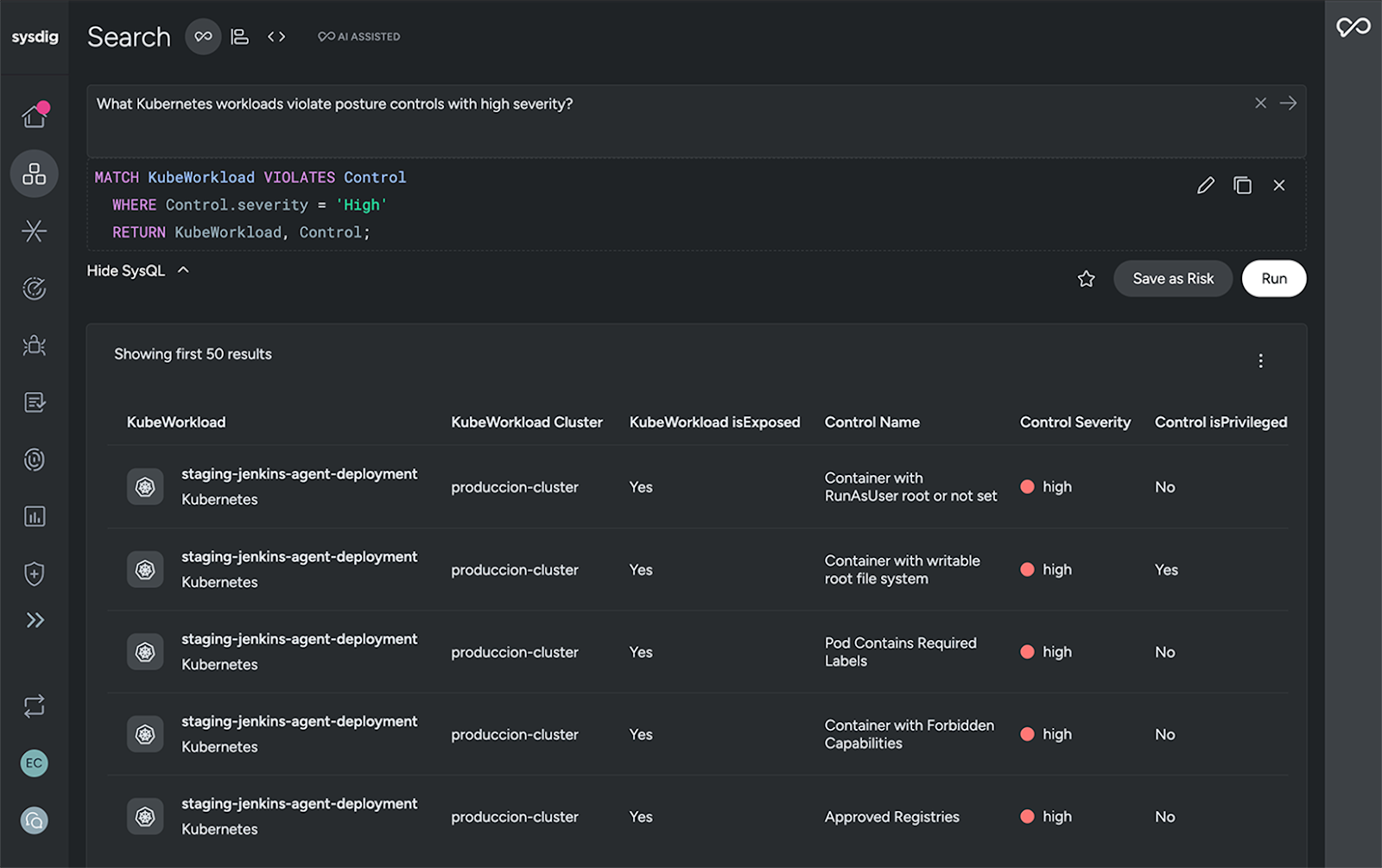
Learn more about how it works with Sysdig Sage.
Demystifying and accelerating runtime security with AI
Runtime security is a vital component for Kubernetes security. It helps to detect suspicious activity, zero-day exploits, and attacks on your infrastructure and workloads.
Threats that target the exploitation of Kubernetes misconfigurations, supply chain vulnerabilities, inadequate access controls, and other weaknesses are unfortunately common. With the right solutions in place, you can protect your environment through hardening, while also leveraging runtime security to detect and block attempts to compromise it.
The unfortunate result of threat activity is a flood of alerts and telemetry that security analysts must sort through to identify real risk and take action. This is another key area where AI can help you surface and understand the most important events. AI agents can automatically enrich threat alerts with easy-to-understand summaries and high-fidelity context, providing the situational awareness you need to take definitive action more quickly.
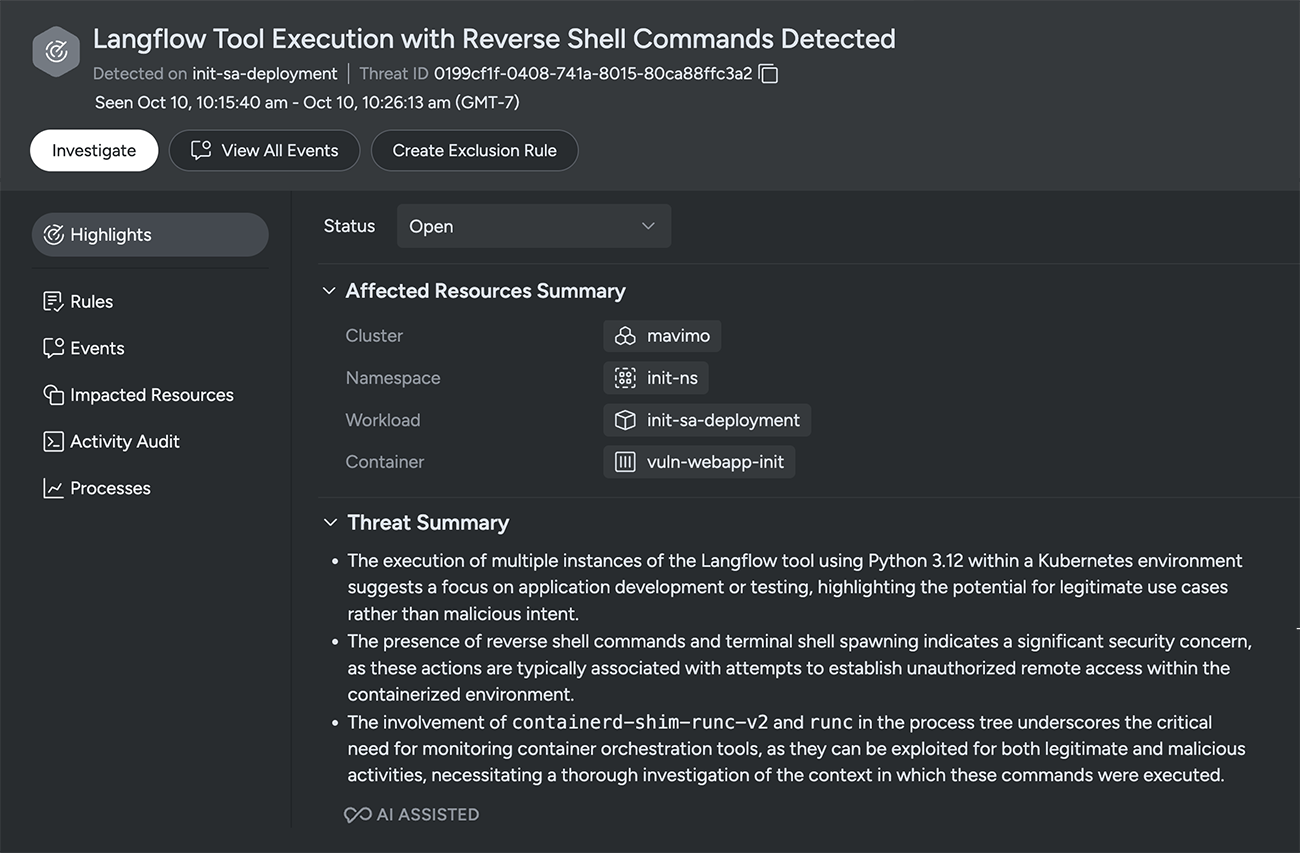
In addition, as is the case with Sysdig Sage, a runtime security chat assistant can help teams peel back the layers of security events to quickly understand the nature of threats. A click of a button provides custom insights into the issue you’re investigating. To dive deeper and understand what to do next, you can ask straightforward questions such as:
- What’s the root cause of this incident?
- What related alerts should I be aware of?
- Is this part of a larger compromise?
- What is the best way to respond to this threat?
This helps reduce time-to-detection and accelerates response in environments where containers often live for only a short period of time.

Learn more about AI-assistance for runtime threats.
Proven Impact: Faster MTTR, lower costs, and greater confidence
The business outcomes of AI-powered cloud security are clear. According to IBM’s Cost of a Data Breach Report 2025, organizations using AI extensively save $1.9 million per breach on average. Google Cloud’s ROI of AI 2025 report found that 77% of companies improved threat identification, and 61% reduced time to resolution
Sysdig customers are already seeing those results:
- A leading U.S. bank cut incident response costs by 52%
- A healthcare technology provider improved mean time to respond (MTTR) by 76%
- Teams report 95% noise reduction in vulnerability management with intelligent prioritization and automation
Kubernetes introduces distinct security challenges. The new battleground is powered by a human-AI partnership. Having an AI-powered teammate that helps you understand, prioritize, and act can make the difference between containment and compromise.
See agentic AI in action. Watch the webinar: Securing Kubernetes with Agentic AI: From Noise to Clarity.


