
Falco Feeds extends the power of Falco by giving open source-focused companies access to expert-written rules that are continuously updated as new threats are discovered.

What if you could connect most of the tools available in your digital toolbox? Business applications, messaging, cloud services — whatever you can imagine — all working together without a single line of code?
Even better than no-code: linking apps and services without manually drawing lines, dragging a trigger, or defining a workflow?
Workflow automations typically involve defining behavior programmatically or building step-by-step processes with decision trees. You may have experimented with traditional automation platforms to link and connect the critical apps, only to find yourself tangled in a web of rules and routines that cannot keep up with an ecosystem that is constantly changing.
What if there was a more innovative way? What if your workflows could build themselves? Imagine a world where your tools understand what you need, anticipate your next step, and connect seamlessly in the background... without you ever lifting a finger.
Welcome to the next generation of intelligent connectivity. Welcome to MCP: Model Context Protocol. Or, as you’ll likely come to call it: the Magic Connection Protocol.
What is MCP? A brief history of agentic AI
Artificial Intelligence (AI) and, in particular, Large Language Models (LLMs), have exploded in capability in recent years. While initially limited to narrow use-cases and bound by their training data, the latest models have evolved to acquire reasoning capabilities (always rooted in language), as well as the ability to create and run scripts or programs, and interact with the outside world (e.g., searching the web).
But these external interactions are quite limited by the mechanisms needed to discover and understand available services (such as APIs that can be invoked).
Introduced by Anthropic in November 2024, MCP was born to fill this gap. It aims to "standardize the way artificial intelligence (AI) systems like large language models (LLMs) integrate and share data with external tools, systems, and data sources."
Major AI providers, including OpenAI and Google DeepMind have adopted MCP. This allows leading AI models to discover and interact with other tools as part of the reasoning and generation process. The AI models that use MCP are called MCP clients. On the other side, an ever-growing collection of MCP servers1, 2 is being provided by service providers, like Gmail, GitHub2, and Jira, just to name a few. And now also Sysdig MCP Server.
And this is just the beginning. AI is expanding beyond the typical question-answer flow towards a more autonomous, agent-based approach. You can request a task to be completed, and AI agents will relentlessly work for you, collaborating with other agents and tools to get the job done!
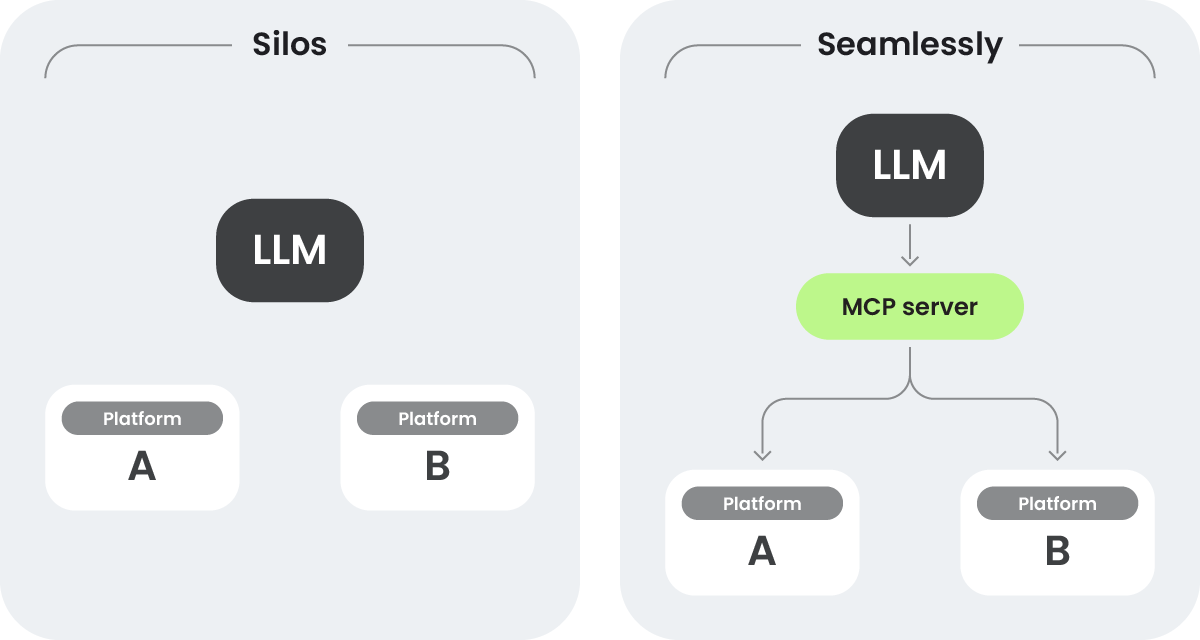
Sysdig MCP Server
Don't confuse Sysdig MCP Server with Sysdig Sage™, our integrated AI Security Analyst, which offers contextualized insights and guidance directly within the Sysdig UI.
What exactly is Sysdig MCP Server? It enables your already existing AI model (like ChatGPT, Claude, and others) to be fully aware of Sysdig services and APIs, and use them as part of the reasoning and response process.
With Sysdig MCP Server, you can ask your favorite LLM about security findings in your Kubernetes clusters, the most critical vulnerabilities in your container images, or suspicious behaviors detected by Falco threat detection rules. The LLM will retrieve that information and include it in its response.
But it’s not just about getting data from an external service. What if the AI assistant could also act on that data, filter it, identify urgent actions, dispatch alerts to Slack or a pager, or take the worst vulnerabilities and create tickets assigned to the responsible teams? Enabling multiple MCP servers and having them work together opens up an infinite world of possibilities!
To install and get started with Sysdig MCP Server, please check the README in our GitHub repository.
Usage examples
Disclaimer: Please note that all examples provided below are examples or proof-of-concepts to demonstrate the potential of the technology, but are not officially supported by Sysdig, and your experience might severely vary depending on the availability and configuration of other MCP servers, the AI model, and the prompt and context of the LLM.
IngressNightmare investigation with ChatGPT and Sysdig MCP Server
This is an example conversation:
- Search for threat events related to the IngressNightmare exploit in the last 2 days.
- What were the processes involved in the event?
- I want detailed info on that event and the vulnerabilities that could be affecting that Kubernetes workload resource.
- And what are the running vulnerabilities in the Kubernetes deployment?
- Now give me a full scan of the last 'resultId' to see if we are passing the "IngressNightmare Detection" vuln policy, and show me the rule bundle names failing.
- Using Sage, give me a query to identify all the Kubernetes workloads affected by the CVE = CVE-2025-1974, and give me a table view of the affected resources in my environment.
- Give me the SySQL query used.
- Create a PDF report with tables and dashboards, with the conversation investigation highlights.
Local image scanning and impact analysis
Sysdig provides a Command Line Interface (CLI) Scanner tool that allows developers to scan container images for vulnerabilities directly on their local machines. While powerful for CI/CD pipelines, this traditionally provides a static, point-in-time view of an image's security.
This use case transforms the static check into a dynamic risk assessment by leveraging the Sysdig MCP Server. An external AI assistant, acting as an MCP client, can be prompted to not only perform the scan via the MCP server but also to cross-reference the findings with your live cloud environment immediately. The LLM can query Sysdig for the runtime impact of any discovered vulnerabilities, asking for a comprehensive security context, like threats and existing exposures. By checking for related threat activity in your running infrastructure, the AI can provide a holistic "go/no-go" recommendation before a single line of code is deployed.
On-demand personalized reporting
Instead of relying on rigid, pre-defined templates or interfaces, the Sysdig MCP Server allows an AI assistant to act as a custom report generator, creating outputs tailored to any user's needs in response to a simple question.
This capability moves beyond live HTML dashboards to include a variety of formats for different audiences. A user can request formal PDF reports for audits, concise markdown summaries for Jira or Slack tickets, or even raw data exports like a CSV for deeper analysis. The AI can also tailor the narrative, translating the same technical data into a high-level business risk summary for an executive or a detailed remediation guide for a developer. This transforms reporting from a static process into a dynamic conversation, ensuring any stakeholder gets the exact data they need, in the format they require, on demand.
Automated vulnerability remediation workflow
This example uses multiple MCP servers:
Sample prompt:
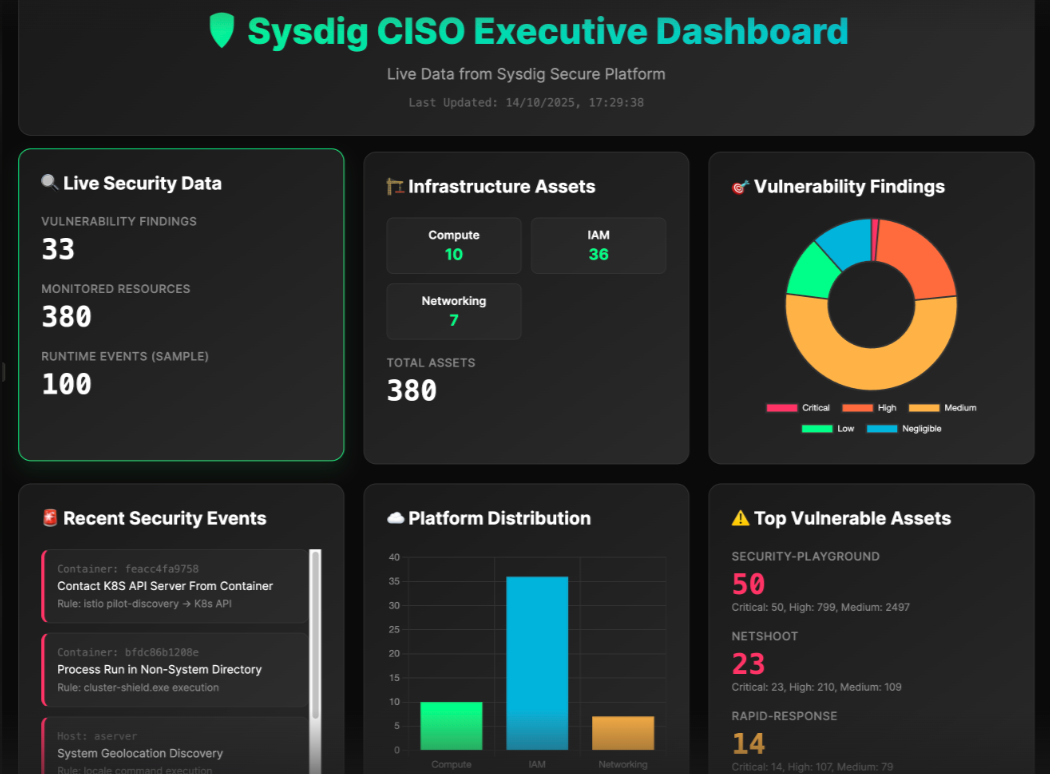
Automated CISO executive dashboard in seconds
The MCP server opens up powerful possibilities for automation and visualization. One compelling use case is creating a CISO dashboard, a visual interface that displays updated information.
Sample prompt:
In closing
The future of security automation isn’t about manually building ever more complex workflows. It’s about letting your tools autonomously collaborate and adapt in real time, powered by AI and the MCP ecosystem.
With Sysdig MCP Server, you’re not just integrating services; you’re unleashing a new era of autonomous security agents working tirelessly to protect what matters most.
Ready to experience the future right now? Try Sysdig MCP Server today. Contribute your ideas, and join the movement redefining how security and AI connect.
3 https://github.com/modelcontextprotocol/servers


