
Falco Feeds extends the power of Falco by giving open source-focused companies access to expert-written rules that are continuously updated as new threats are discovered.

There is no shortage of velocity when it comes to new threats. Prioritization helps, but how do we rapidly find what's being exploited in the wild?
In this article, we’ll dive into IngressNightmare, a fast-moving Kubernetes vulnerability making waves across the cloud security landscape. This zero-day vulnerability impacted an estimated 40% of Kubernetes environments due to the widespread use of the NGINX Ingress Controller. In-high gravity scenarios like these, security teams are under pressure to do more than just apply patches. They need to rapidly identify exposure, investigate any signs of compromise, and respond with confidence.
The Sysdig Threat Research Team
Being able to detect zero-day vulnerabilities isn’t a trivial task; it requires extensive experience, advanced methodologies, and adequate resources to find, analyze, and validate the unknowns. That’s why a dedicated resource like Sysdig’s Threat Research Team makes a big difference. As soon as the IngressNightmare vulnerability was uncovered, the Sysdig team moved quickly to develop a runtime detection rule capable of identifying active exploitation in real time. This rule was immediately added to Sysdig’s Managed Runtime Threat Detection policy, giving all Sysdig Secure customers instant protection across their environments the day the vulnerability was disclosed, before widespread exploitation began.
So what is the secret weapon that allows the Sysdig Threat Research Team to rapidly respond with high-fidelity detections? The secret lies in Falco, Sysdig’s open source runtime security engine and the foundation of its detection capabilities. Falco enables the rapid creation of flexible, powerful detection rules by tapping directly into the Linux kernel and monitoring system calls in real time. Every command, file access, network connection, and process is observed in real time, providing deep visibility into system activity and making it possible to detect threats with extreme precision.
To dive deeper into the IngressNightmare vulnerability and how Sysdig’s Threat Research Team responded, check out our full blog post on detecting and mitigating IngressNightmare.
Threat hunting with Sysdig
When it comes to identifying vulnerabilities, especially those that are actively being exploited, speed is critical. When a new vulnerability like this is disclosed, how can you check if it exists in your environment? More importantly, what happens if you don’t closely monitor cybersecurity news, and don't know to look for the vulnerability at all? That’s where Sysdig’s new Threat Intelligence Feeds come into play. These feeds help you quickly assess your exposure to emerging and high-profile threats. Each entry provides a concise summary of the threat, whether it’s malware, a CVE, a misconfiguration, or a supply chain risk, along with insight into whether your environment is impacted. You’ll also get a direct link to Graph Search, enabling you to immediately investigate affected workloads, packages, identities, or hosts that may require remediation.
For high-profile vulnerabilities like IngressNightmare, the Threat Intelligence Feed helps answer the critical question “Am I at risk?” and allows you to focus your response efforts efficiently, avoiding unnecessary triage if you’re unaffected.
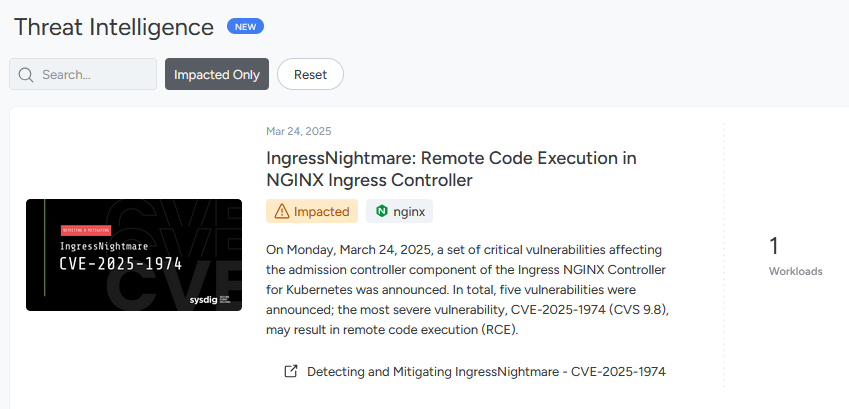
Sysdig Graph Search
Directly from the Sysdig Threat Feed seen above, we can quickly launch a pre-built Graph Search query to instantly drill into the affected resources, providing immediate visibility into which workloads, packages, or hosts are at risk.
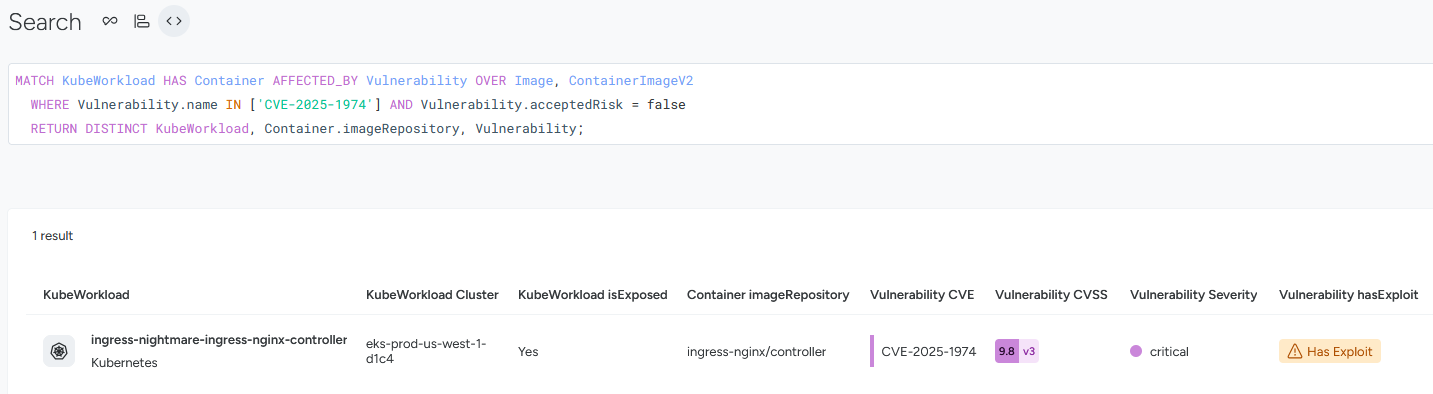
With the query complete, we’re now focused on the affected Kubernetes resource itself. By opening the resource panel, we can see critical risk indicators. This workload has multiple high-severity vulnerabilities, is exposed to the internet, and has active runtime threats triggered against it. These insights are surfaced immediately, helping prioritize what needs attention first.
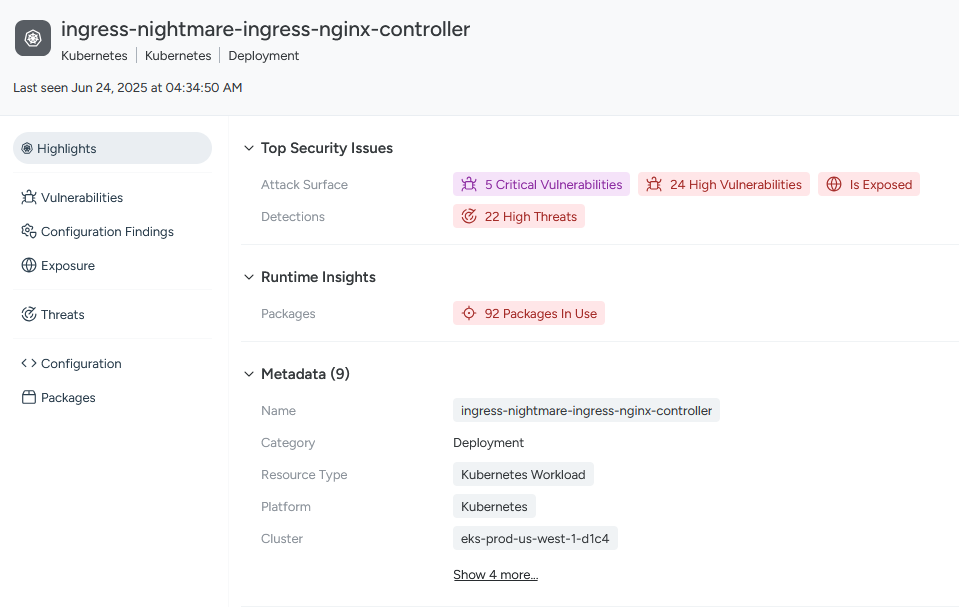
Sysdig Threat Management
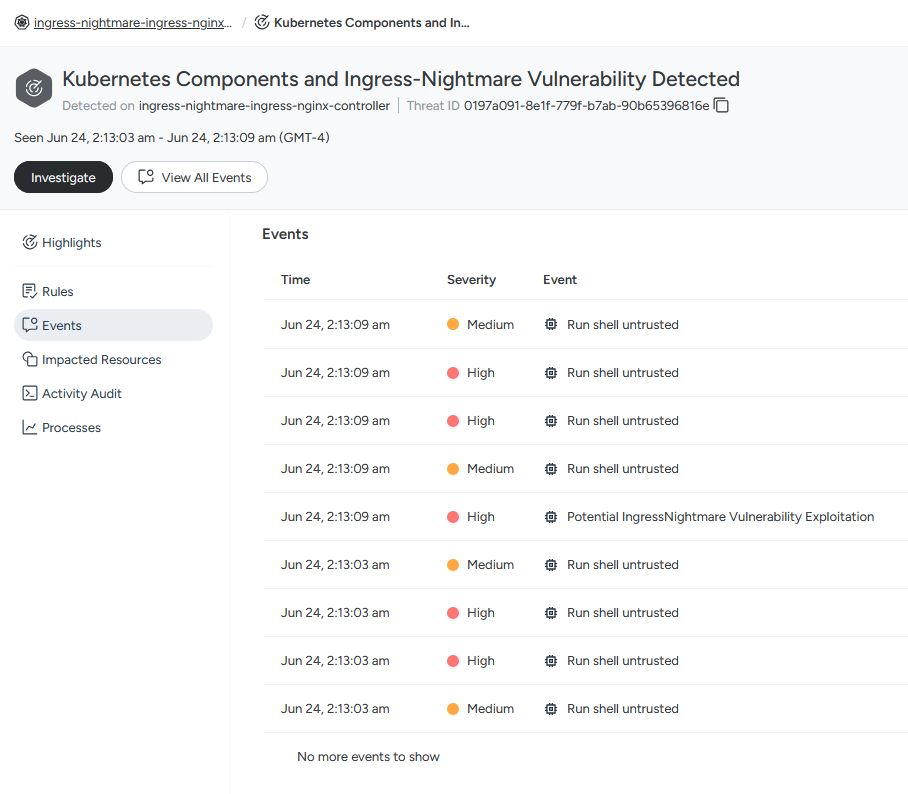
Within Sysdig Threat Management, we see active runtime detections that were triggered on this workload just 9 hours ago. By drilling into the Threat, we get a detailed view of the associated runtime activity, clearly mapping the full attack chain. This context is crucial for confirming whether the vulnerability we’re investigating has already been exploited in our environment.
In the Events section of the threat, we’re presented with a detailed timeline of all detection events tied to the incident. Here, it becomes clear the IngressNightmare exploit was executed, granting the attacker remote code execution and allowing them to open a shell on the workload. This level of visibility is essential for understanding the attacker’s actions and scope of impact.
Sysdig Inline Response
Now that we’ve confirmed our environment is both vulnerable to IngressNightmare and actively being exploited, it’s critical to act fast. Containment becomes the top priority while we work on remediation.
Sysdig streamlines this process with both automated and manual response actions built right into the platform. From the threat event, we simply navigate to the Respond section, where we can select and trigger the appropriate response — whether that’s isolating the affected workload, killing a suspicious process, or quarantining a file for later forensic analysis.
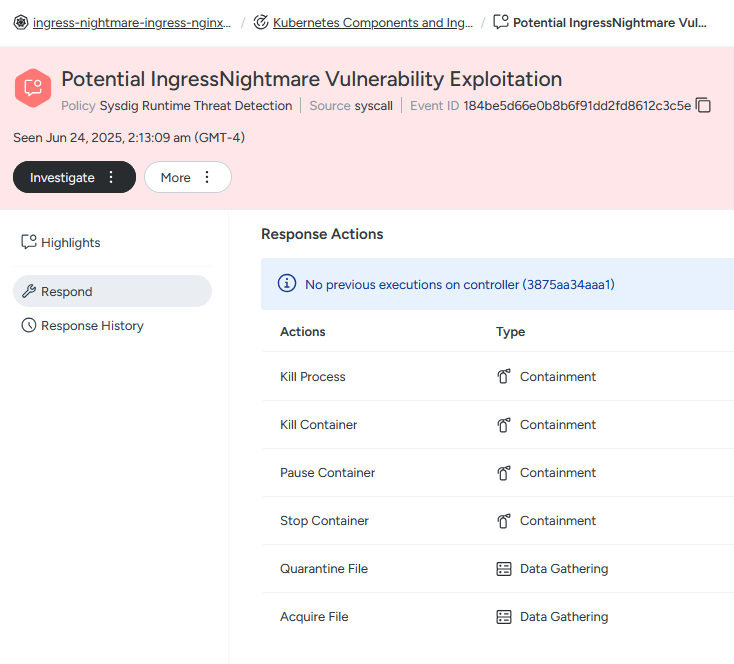
Here, we’ll choose to kill the affected container, effectively halting the attack in its tracks. This action immediately terminates any active processes or remote sessions the attacker may have established. It's a fast, decisive way to contain the threat while avoiding broader disruption to the cluster. By stopping the container, we buy time to investigate further and begin remediation with confidence.
Sysdig Sage remediation guidance
To complete this investigation and fully contain the threat, the next crucial step is to remediate the workload itself. Fortunately, Sysdig Sage simplifies this by automatically generating detailed, AI-powered remediation guidance for every vulnerable package within the container image, as well as for the base image, ensuring a comprehensive fix for the entire application. Once these remediations have been applied, we can be confident that the threat is completely contained.

Sysdig’s commitment to cloud security
Threat hunting and vulnerability remediation have never been easier thanks to Sysdig’s powerful, streamlined platform. Real-time detections paired with a dynamic relationship-mapping graph database give you unmatched visibility and context, helping you quickly correlate events across workloads, hosts, and identities. With intuitive workflows, you can move seamlessly from detecting a threat to drilling down into affected resources and understanding the full attack chain. Sysdig Sage then accelerates remediation by automatically generating AI-driven guidance for every vulnerable package and base image update, simplifying complex security tasks and helping you close gaps faster. Together, these capabilities make threat hunting and response faster, smarter, and more efficient, so your team can focus on what matters most: protecting your environment.
Discover how Sysdig can enhance the security of your cloud environment — request a personalized demo today to explore how our solutions align with your specific needs.


