blogs
Insights at Cloud Speed

EtherRAT dissected: How a React2Shell implant delivers 5 payloads through blockchain C2
Sysdig Threat Research Team
|
December 16, 2025
EtherRAT dissected: How a React2Shell implant delivers 5 payloads through blockchain C2

EtherRAT: DPRK uses novel Ethereum implant in React2Shell attacks
Sysdig Threat Research Team
|
December 8, 2025
EtherRAT: DPRK uses novel Ethereum implant in React2Shell attacks

Detecting React2Shell: The maximum-severity RCE Vulnerability affecting React Server Components and Next.js
Sysdig Threat Research Team
|
December 5, 2025
Detecting React2Shell: The maximum-severity RCE Vulnerability affecting React Server Components and Next.js

Kubernetes 1.35 - New security features
Víctor Jiménez Cerrada
|
December 2, 2025
Kubernetes 1.35 - New security features
join our newsletter
Stay up to date– subscribe to get blog updates now
Thank you! Your submission has been received!
Oops! Something went wrong while submitting the form.
CVE wake-up call: What’s ahead after the MITRE funding fiasco
April 17, 2025
ashish chakrabortty
CVE wake-up call: What’s ahead after the MITRE funding fiasco
Cloud Security

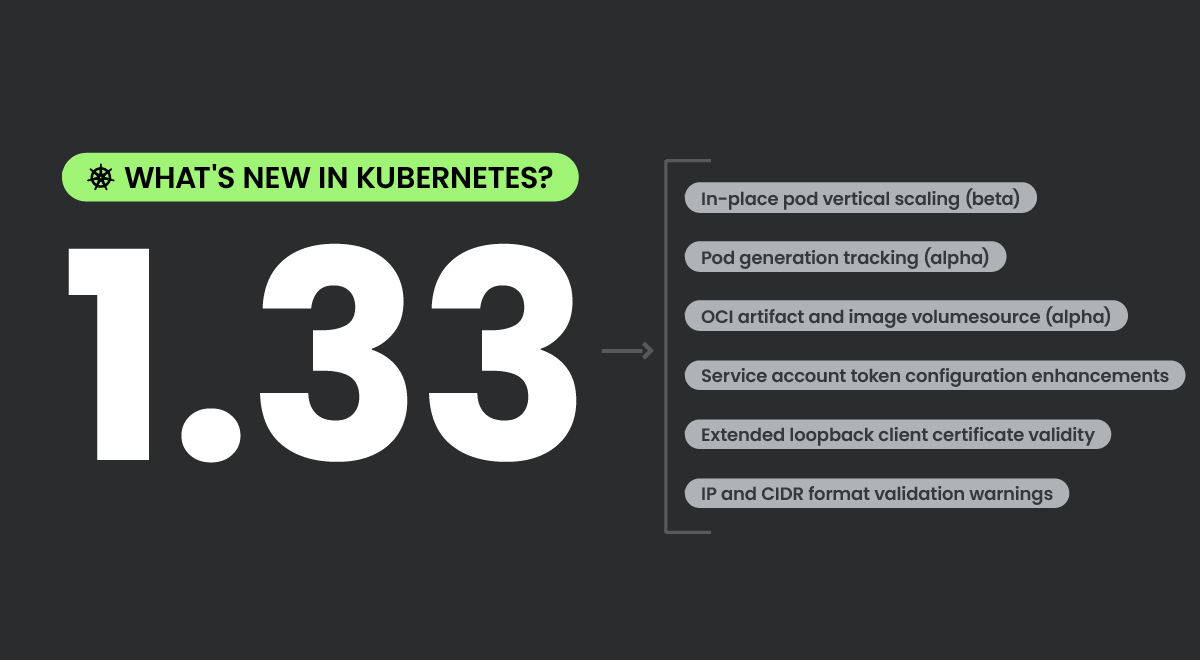
Kubernetes 1.33 – What’s new?
April 16, 2025
Sysdig Team
Kubernetes 1.33 – What’s new?
Kubernetes & Container Security
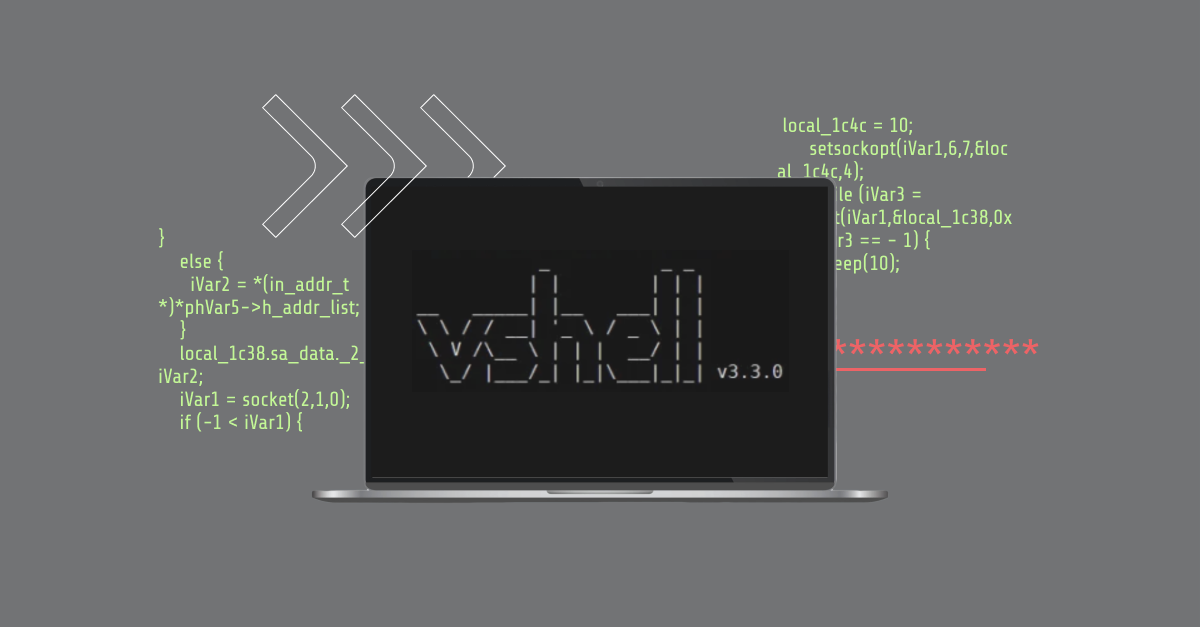
UNC5174’s evolution in China’s ongoing cyber warfare: From SNOWLIGHT to VShell
April 15, 2025
Alessandra Rizzo
UNC5174’s evolution in China’s ongoing cyber warfare: From SNOWLIGHT to VShell
Threat Research
AI-driven CSPM: How GenAI will transform cloud security posture management
April 14, 2025
Eric Carter
AI-driven CSPM: How GenAI will transform cloud security posture management
Cloud Security

The evolution of the Sysdig Agent
April 11, 2025
Radhika Puthiyetath
The evolution of the Sysdig Agent
Cloud Security

