blogs
Insights at Cloud Speed

EtherRAT dissected: How a React2Shell implant delivers 5 payloads through blockchain C2
Sysdig Threat Research Team
|
December 16, 2025
EtherRAT dissected: How a React2Shell implant delivers 5 payloads through blockchain C2
Introducing runtime file integrity monitoring and response with Sysdig FIM
Paolo Polidori
|
December 16, 2025
Introducing runtime file integrity monitoring and response with Sysdig FIM

EtherRAT: DPRK uses novel Ethereum implant in React2Shell attacks
Sysdig Threat Research Team
|
December 8, 2025
EtherRAT: DPRK uses novel Ethereum implant in React2Shell attacks

Detecting React2Shell: The maximum-severity RCE vulnerability affecting React Server Components and Next.js
Sysdig Threat Research Team
|
December 5, 2025
Detecting React2Shell: The maximum-severity RCE vulnerability affecting React Server Components and Next.js
join our newsletter
Stay up to date– subscribe to get blog updates now
Thank you! Your submission has been received!
Oops! Something went wrong while submitting the form.
How highly effective CISOs lean forward with proactive risk management
August 13, 2024
Matt Stamper
How highly effective CISOs lean forward with proactive risk management
Cloud Security
Kubernetes & Container Security

How to securely onboard customers during a cloud security solution migration
August 8, 2024
Igor Eulalio
How to securely onboard customers during a cloud security solution migration
Cloud Security
Detect and respond to compromised identities in minutes with Sysdig
August 7, 2024
ashish chakrabortty
Detect and respond to compromised identities in minutes with Sysdig
Cloud Security
Sysdig Features
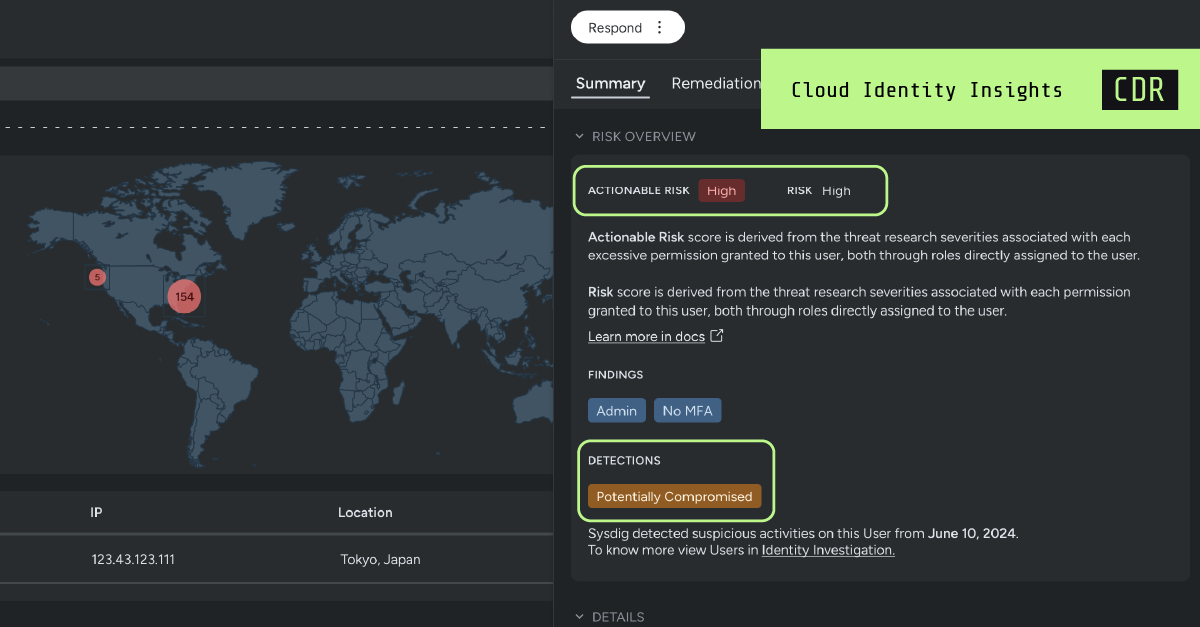
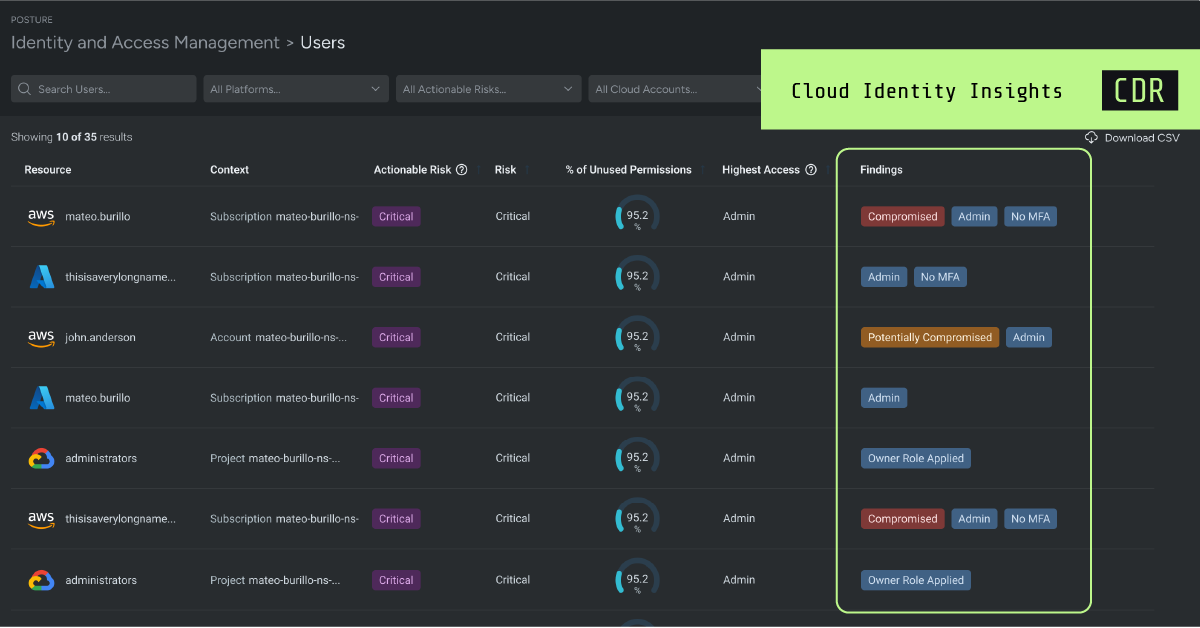
Introducing Cloud Identity Insights for Sysdig Secure
August 7, 2024
Maya Levine
Introducing Cloud Identity Insights for Sysdig Secure
Cloud Security
Sysdig Features
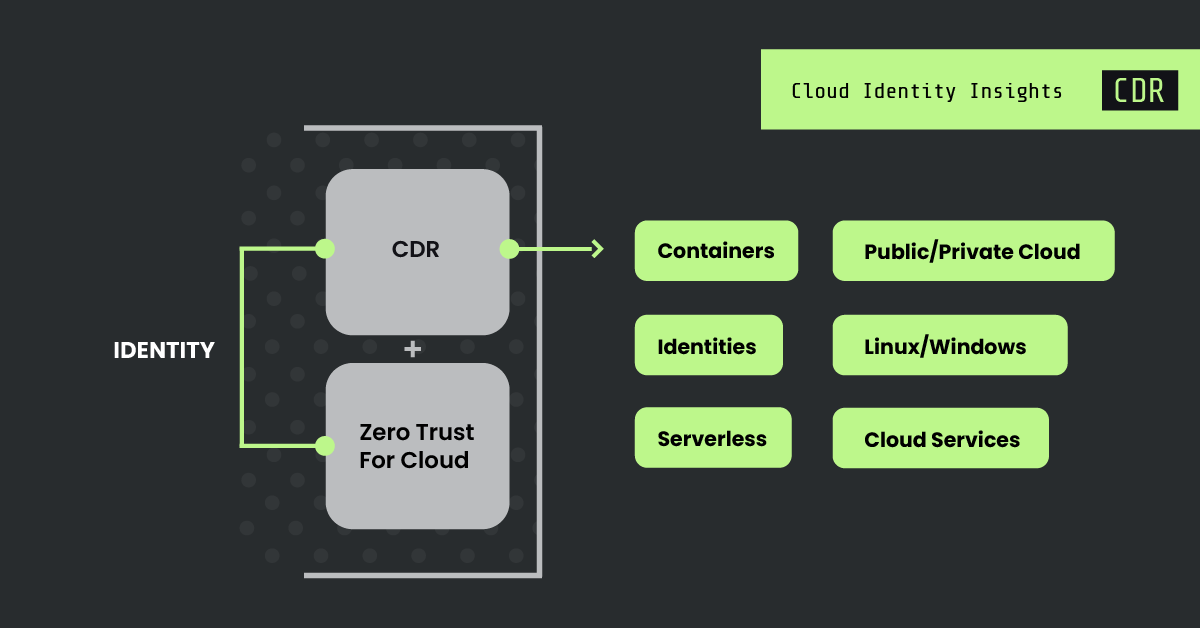
Evolving cloud security: Why identity infused CDR is the key
August 7, 2024
Matt Kim
Evolving cloud security: Why identity infused CDR is the key
Cloud Security
Sysdig Features
Unmatched coverage for cloud and hybrid workloads: Meet Sysdig’s next generation instrumentation
August 7, 2024
Christian Laffin
Unmatched coverage for cloud and hybrid workloads: Meet Sysdig’s next generation instrumentation
Cloud Security
Sysdig Features
