blogs
Insights at Cloud Speed

EtherRAT dissected: How a React2Shell implant delivers 5 payloads through blockchain C2
Sysdig Threat Research Team
|
December 16, 2025
EtherRAT dissected: How a React2Shell implant delivers 5 payloads through blockchain C2
Introducing runtime file integrity monitoring and response with Sysdig FIM
Paolo Polidori
|
December 16, 2025
Introducing runtime file integrity monitoring and response with Sysdig FIM

EtherRAT: DPRK uses novel Ethereum implant in React2Shell attacks
Sysdig Threat Research Team
|
December 8, 2025
EtherRAT: DPRK uses novel Ethereum implant in React2Shell attacks

Detecting React2Shell: The maximum-severity RCE vulnerability affecting React Server Components and Next.js
Sysdig Threat Research Team
|
December 5, 2025
Detecting React2Shell: The maximum-severity RCE vulnerability affecting React Server Components and Next.js
join our newsletter
Stay up to date– subscribe to get blog updates now
Thank you! Your submission has been received!
Oops! Something went wrong while submitting the form.
Detecting and Mitigating CVE-2023-4911: Local Privilege Escalation Vulnerability
October 5, 2023
Daniele Linguaglossa
Detecting and Mitigating CVE-2023-4911: Local Privilege Escalation Vulnerability
Cloud Security
Threat Research

Using Runtime Insights with Docker Scout to Prioritize Vulnerabilities
October 4, 2023
Victor Hernando
Using Runtime Insights with Docker Scout to Prioritize Vulnerabilities
Kubernetes & Container Security

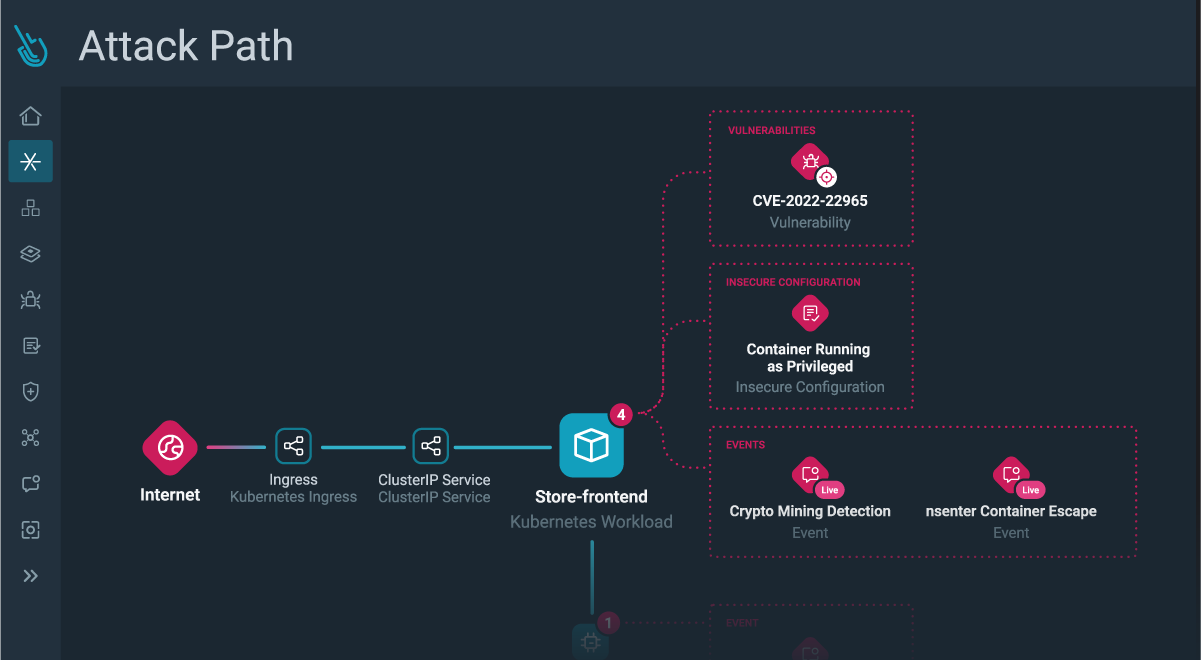
Unveiling Sysdig Secure Risks and Attack Path Analysis: Visualizing and prioritizing cloud security risks
September 27, 2023
Daniel Simionato
Unveiling Sysdig Secure Risks and Attack Path Analysis: Visualizing and prioritizing cloud security risks
Cloud Security
Kubernetes & Container Security
Sysdig Features
Introducing Agentless Vulnerability Management: A complete guide to strengthening your security
September 27, 2023
Joseph Yostos
Introducing Agentless Vulnerability Management: A complete guide to strengthening your security
Cloud Security
Kubernetes & Container Security
Sysdig Features

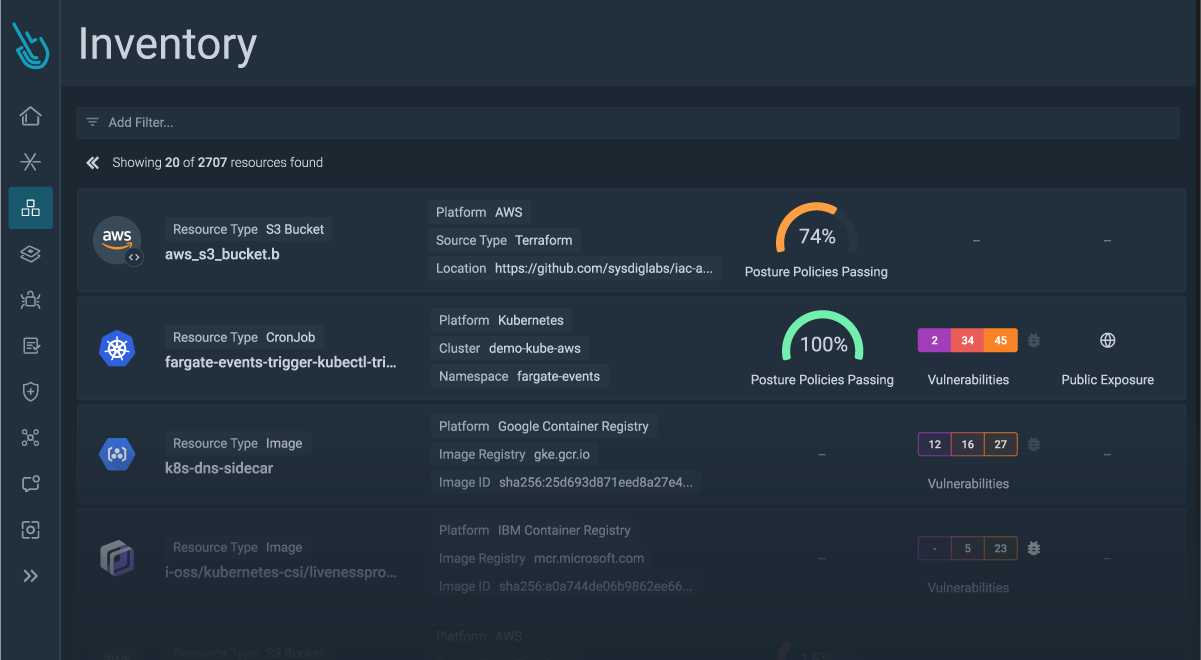
Introducing Sysdig’s Enhanced Searchable Inventory for complete cloud visibility
September 27, 2023
Daniel Simionato
Introducing Sysdig’s Enhanced Searchable Inventory for complete cloud visibility
Cloud Security
Compliance
Kubernetes & Container Security
Sysdig Features
When Seconds Count: Expanding Real-Time Capabilities Across CNAPP
September 27, 2023
Nick Fisher
When Seconds Count: Expanding Real-Time Capabilities Across CNAPP
Cloud Security
Kubernetes & Container Security
Sysdig Features
