Falco Feeds extends the power of Falco by giving open source-focused companies access to expert-written rules that are continuously updated as new threats are discovered.

Traditional file integrity monitoring (FIM) tools were not built for Kubernetes, containers, or cloud-scale environments. They rely on resource-heavy scans and alert on routine activity, often overwhelming security teams with noise and limited context. Agentless snapshot methods often fail to detect short-lived runtime changes or provide process-level forensic context.
Sysdig runtime FIM changes that. By leveraging Falco for event-driven detection, Sysdig delivers fast, lightweight, and context-rich file integrity monitoring. It monitors critical file paths in real time, triggers only if a file has been written to and the hash doesn't match. Through this process, Sysdig provides forensic detail that enables faster investigation, preserves system performance, reduces mean time to containment (MTTC), and meets compliance requirements without the complexity of legacy tools.
Why traditional FIM falls short
Legacy FIM tools typically operate through periodic scans that recalculate cryptographic hashes across large file sets, regardless of whether changes have occurred. In modern environments like Kubernetes, where workloads are short-lived and constantly shifting, this method results in wasted compute, excessive I/O, and a lag in threat detection. The resulting lack of reactivity in this legacy approach can lead to potential misses.
These tools also generate high volumes of low-fidelity alerts, including benign operations like log reads or configuration access. This simply adds to the already high levels of alert fatigue without delivering meaningful signals. Even when a real change is detected, traditional FIM tools often lack the context needed to investigate, and they may not even identify which process made the change, under what user, or as part of which broader event chain. Without this critical context, teams are limited in their ability to execute on their containment and remediation workflows.
How Sysdig runtime FIM works
Sysdig runtime FIM takes a fundamentally different approach. Instead of scanning files on a schedule or triggering on every access, it listens for file system events in real time and only recalculates hashes when a file is written to.
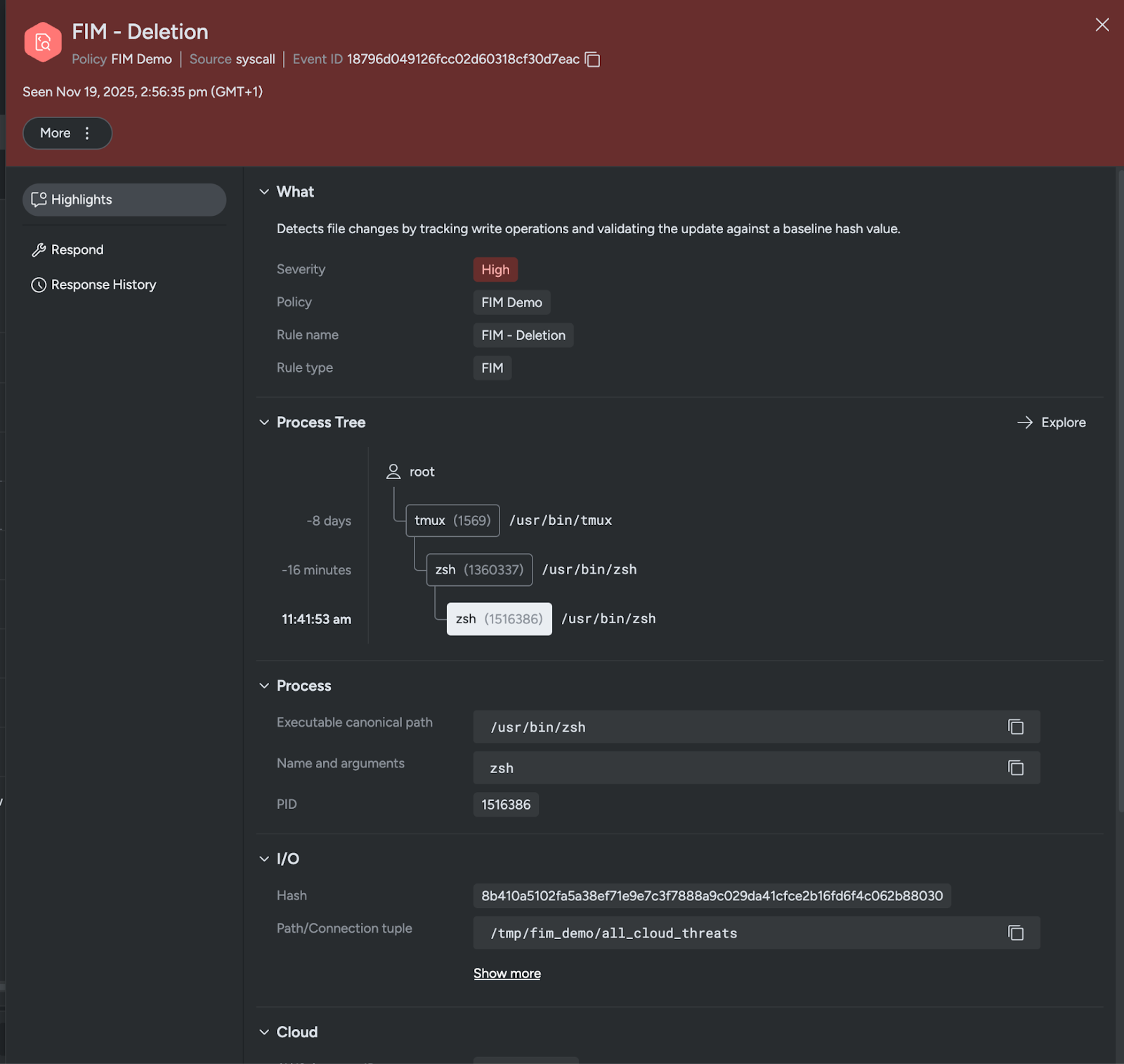
This begins with a baseline hash inventory, defined through a FIM policy. From there, Sysdig listens at runtime and selectively re-checks hashes on write events. If a file write occurs then we compare the hashes to see if a change was made. If a violation is found, an alert is surfaced along with full forensic context.
Security teams gain deep visibility into the change, including the responsible process, parent process, and container metadata. This accelerates the investigation and helps determine whether the modification is benign, suspicious, or clearly malicious.
Reducing false positives and improving performance
By calculating hashes only when write events occur, Sysdig avoids the two biggest problems of legacy FIM tools: unnecessary resource consumption and excessive alert noise. This event-driven model allows FIM to scale efficiently in containerized environments running across many nodes and clusters.
Because detection is driven by system events captured in real time, there is no need for a background process continuously scanning the file system. The result is lower CPU usage, reduced I/O pressure, and better overall performance for monitored workloads.
Reducing MTTC with real-time forensics
Sysdig FIM does more than detect unauthorized file changes. It enables faster, more accurate responses by providing security analysts with critical context tied to each alert, including the process tree, user ID, and container or pod metadata.
One of the most valuable aspects of detection context is process lineage. In many attacks, malicious changes are made by short-lived processes or under generic service accounts. Without lineage data, security teams can struggle to piece together what happened. Sysdig solves this by tracing file modifications back to their origin with high fidelity.
Through Sysdig Automations, teams can also collect the modified files for examination. These collections are automatic, without complications and delivered in a timely manner, before any further changes can happen. This post event analysis can help you to understand if the event in question was malicious, simply a bad practice, or even a false positive, just by looking at the file content. Alternatively, you can also take responsive actions, such as choosing to contain the action and take definitive countermeasures like killing the Kubernetes pod or the process that wrote it.
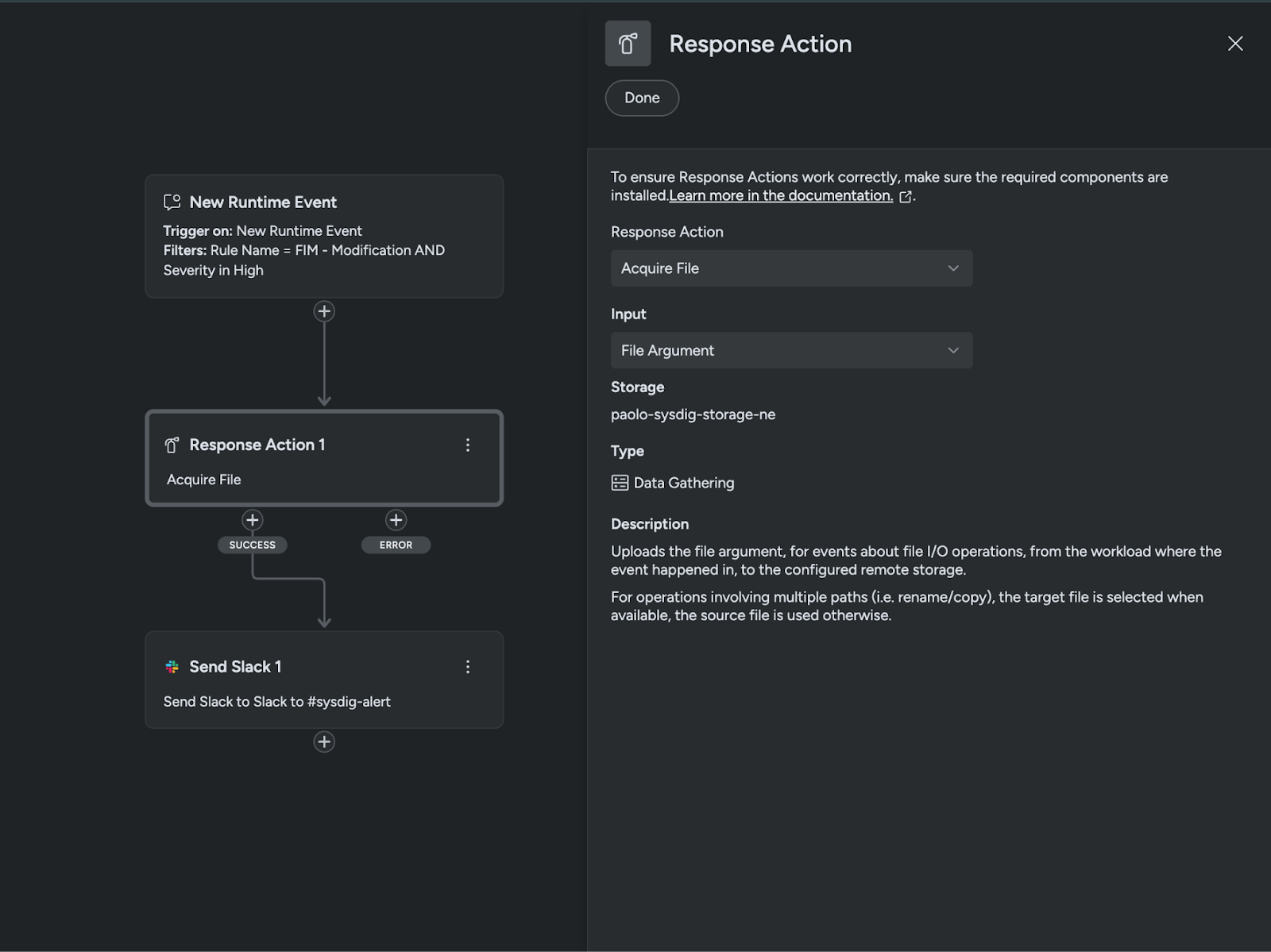
By surfacing this data in real time, Sysdig significantly reduces mean time to contain (MTTC). Analysts can quickly understand the scope and impact of a file-based threat, take corrective action, and limit potential damage before it spreads.
Built for compliance in regulated environments
File integrity monitoring remains a required control for many compliance frameworks, including PCI-DSS, NIST SP 800-53, HIPAA, ISO 27001, and GDPR. However, meeting these requirements in a cloud-native environment can be challenging without the right tools.
Sysdig FIM helps teams comply by allowing them to define flexible policies targeting specific file paths, users, containers, or Kubernetes labels. Because the system detects and responds to changes as they occur, it satisfies not just the letter of compliance controls, but also the intent, providing a reliable, real-time safeguard for production systems.
Why event-driven detection matters
Traditional FIM tools that rely on scheduled scans introduce latency. A malicious change might go undetected for minutes or hours, depending on the scan frequency. That window of time is more than enough for an attacker to cause damage or erase their tracks.
Sysdig FIM closes this gap. It monitors system calls in real time using Falco, the open source engine created by Sysdig, which is now a CNCF-graduated project. When a file write occurs, Falco evaluates whether it matches a defined policy. If so, Sysdig FIM triggers an alert enriched with all the telemetry needed to investigate and respond immediately.
Because alerts are tied directly to actual write events, instead of just access or scheduled checks, security teams only receive a detection notification when meaningful changes occur. This high signal-to-noise ratio makes it easier to focus on true risks and respond with confidence.
Fully integrated with the Sysdig Secure platform
Sysdig FIM is built into the Sysdig Secure CNAPP platform, working alongside runtime threat detection, cloud configuration monitoring, container and Kubernetes security, and vulnerability management. File integrity events are visible in the Threat Management Dashboard and managed using the same rule-based policy model used across Sysdig.
This allows security and platform teams to create unified policies, enforce controls across cloud and hybrid environments, and scale monitoring across multiple clusters without performance trade-offs.
Whether you're monitoring sensitive configuration files, container startup scripts, or application directories, Sysdig FIM gives you the flexibility and control to implement FIM the right way in a cloud-native world.
Conclusion
File integrity monitoring is no longer just a checkbox for audits; it has evolved into a critical control for early threat detection, system integrity, and regulatory compliance. Traditional scan-based tools cannot meet the speed, scale, and complexity of today’s cloud-native environments.
Sysdig FIM delivers a modern solution built for runtime, with low overhead, fewer false positives, and full forensic visibility. By detecting and responding to file-based threats in real time, it helps teams reduce MTTC, minimize risk, and maintain performance at scale.
Ready to modernize your FIM strategy? Request a demo to see Sysdig FIM in action.


