Falco Feeds extends the power of Falco by giving open source-focused companies access to expert-written rules that are continuously updated as new threats are discovered.

Nowadays, with the growth of AI usage, companies are seeing an increase of Model Context Protocol (MCP) servers due to the requirements for integration with LLMs. With the recent launch of the Sysdig MCP server, we have been working with different use cases, and as expected, the possibilities are endless.
In fact, we already have another blog post where we show what you can accomplish when prompting with two MCPs together. For this blog post, we will focus on using Amazon Q Developer with the Sysdig MCP server.
Why pre-deployment matters
Developers, platform engineers, and SREs deploy code rapidly, and AI tools are accelerating that pace even faster. But speed without security creates risk: cloud breaches frequently start by exploiting Infrastructure as Code (IaC) misconfigurations.
This is where the "shift-left" approach becomes critical, as it catches security issues during development, not after deployment.
To help secure IaC, you can bring security scanning directly into your IDE using the Model Context Protocol (MCP). For example, by connecting Amazon Q Developer with Sysdig's MCP server, you can identify vulnerabilities, catch misconfigurations, and review your security posture before they become production threats – all through conversational prompts in your code editor.
In this post, we'll explore practical workflows for scanning infrastructure code, analyzing container images, and understanding potential attack paths-all without leaving your development environment.
The building blocks
- AWS account with access to Amazon Q Developer (Free tier)
- An IDE: VS Code
- Amazon Q Developer plugin for VS Code
- Sysdig MCP server downloaded locally
This is the detailed configuration that can be used within the MCP Server settings in the Amazon Q plugin:
Name: SysdigMCP
Transport: stdio
Command: <uv-binary-path> (e.g., /usr/<username>/.nix-profile/bin/uv)
# Arguments - optional
--directory
<sysdig-mcp-server-directory>
run
main.py
# Environment variables - optional
SYSDIG_MCP_API_HOST=<SYSDIG-SAAS-URL> (e.g., https://secure.sysdig.com)
SYSDIG_MCP_API_SECURE_TOKEN=<API-ACCOUNT-TOKEN>
SYSDIG_MCP_TRANSPORT=stdioUse cases
Context
Here we have a simple project with different kinds of files (CloudFormation, Helm Chart values, scripts, Lambda, etc.) that will be used for our use cases. Below is an overview of the directory structure:
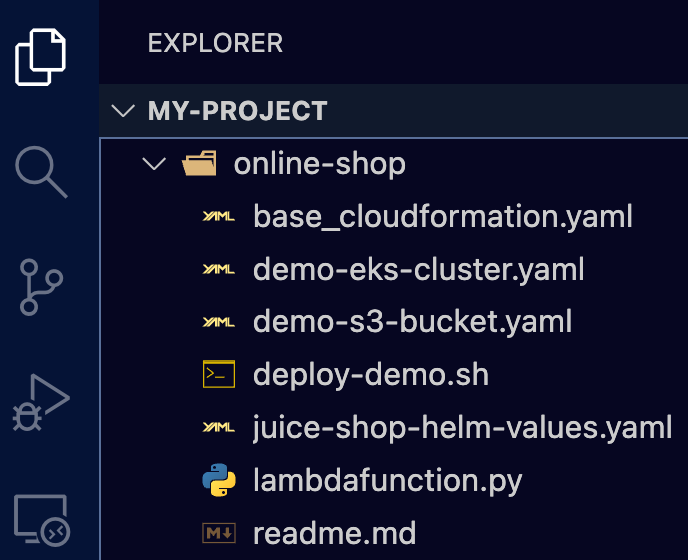
This online-shop directory will be the one that we will configure as “Context” to Amazon Q whenever we ask any question.
Workflows in action
We'll step into the role of a Site Reliability Engineer working with IaC configurations for microservices hosted in AWS. Let’s imagine you have been asked to add new features to the microservices already deployed, but you want to ensure your infrastructure changes don’t introduce security vulnerabilities.
Now, we will proceed to analyze different themes using Amazon Q and the Sysdig MCP server within the VS Code IDE.
Scanning my local code for IaC misconfigurations
Let’s review if we have any misconfigurations within our IaC files so we are not introducing any new risks without knowing it.
Use the Sysdig IAC scanner to scan my project and AmazonQ for the CloudFormation templates, then share a summary of the issues found.
Finding vulnerabilities in container images
Before deploying our changes, we need to know if there are any vulnerabilities in our container images. Software Composition Analysis (SCA) usually happens in the CI/CD pipeline, but we can do it earlier instead of waiting for builds and potentially blocking issues.
Use Sysdig CLI to scan the docker image pointed by the juice-shop-helm-values.yamlReviewing our baseline: What’s already deployed?
Even if our code is perfectly secure, deploying into an environment with existing vulnerabilities could create unexpected attack paths (e.g., deploying a secure microservice that uses a compromised S3 bucket). Hence, it is critical to review our environment and, if necessary, fix first, deploy second.
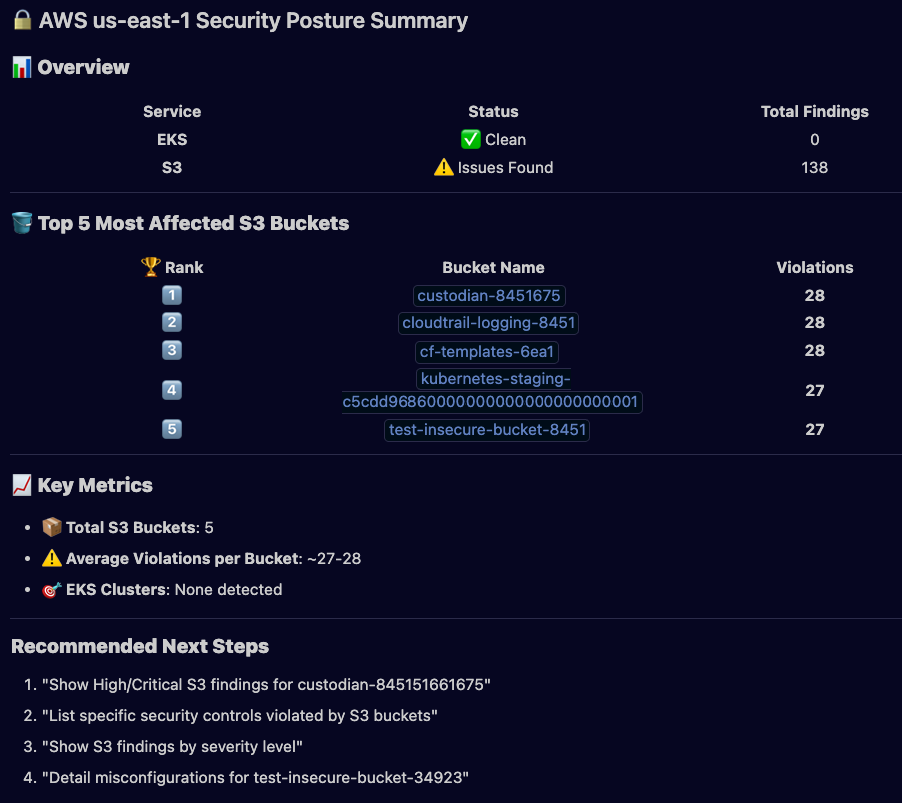
Use Sysdig to summarize the current EKS and S3 security posture in AWS us-east-1.
- Return only aggregated results: counts by severity and status, top 5 misconfigurations, and top 5 affected resources (name + count).
- Do not list raw findings or evidence. Keep the output small and sensible.
- If more details are needed, suggest next drill-downs (e.g. top 10 High/Critical findings).As the output, we can see that it shares a nice representation of our current posture by querying the Sysdig MCP:
Analyzing future posture: What happens when we deploy?
We already validated our code locally and reviewed what is currently deployed (posture). Now let’s predict the security implications before deploying our code (will introduce new risks, new attack paths, or improve the security posture?

Tracing attack paths after deployment
By analyzing potential attack paths, we are doing something similar to the previous workflow, but now understanding how it could be exploited. This will reveal how those findings connect to create a potential exploitable chain.
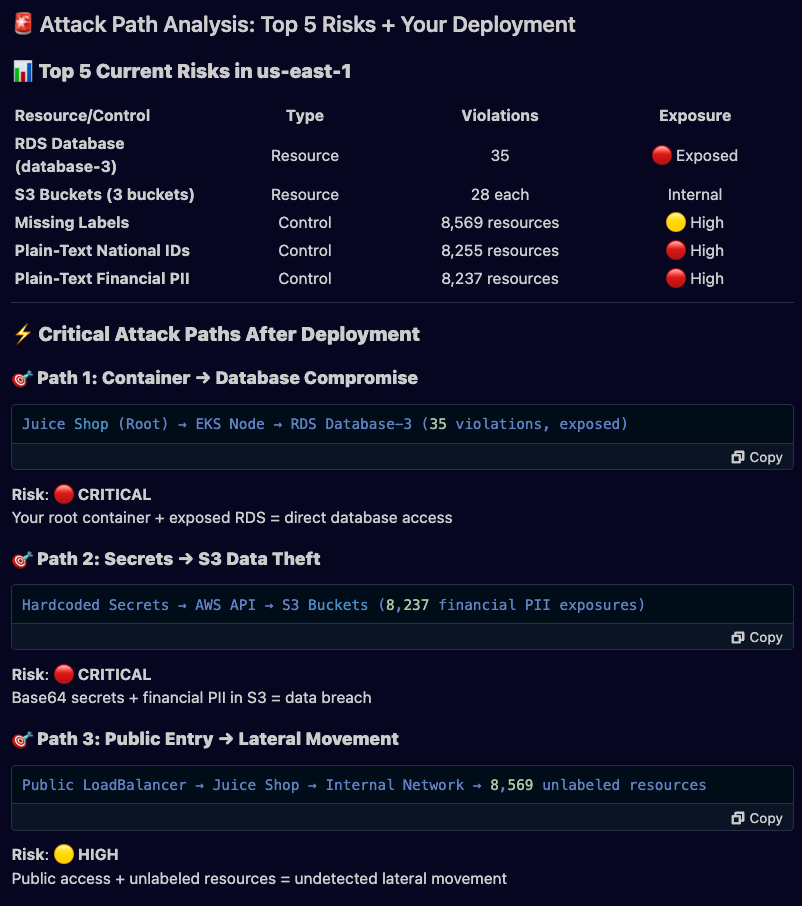
Ask Sysdig what are the current top risks in us-east-1. Use that information to see if there could be an attack path if I deploy all resources from the project.
Return only aggregated results with limit 5.Amazon Q shared a very interesting report showing potential exploitable paths in our “online-shop” project:

Final thoughts
The combination of Model Context Protocol (MCP) servers and AI opens up a great variety of use cases for combining tools that were previously harder to combine.
By pairing Amazon Q and Sysdig in VS Code, you can empower your shift-left approach by hunting IaC misconfigurations, vulnerabilities, and potential attack paths before your code gets into a CI/CD pipeline. But it goes beyond that - you can even predict your future security posture and impact – all from your IDE.
That’s why testing new MCPs can unlock new use cases you may not have tried before, because the barrier to integrating different technologies has dropped significantly thanks to the MCP. It's worth exploring what other MCP servers could enhance your workflow.
What’s next?
Try Sysdig MCP Server today and combine it with the Amazon Q Developer plugin for VS Code so you can test these workflows and unlock even other ones which we haven’t discussed here.


