blogs
Insights at Cloud Speed

EtherRAT dissected: How a React2Shell implant delivers 5 payloads through blockchain C2
Sysdig Threat Research Team
|
December 16, 2025
EtherRAT dissected: How a React2Shell implant delivers 5 payloads through blockchain C2
Introducing runtime file integrity monitoring and response with Sysdig FIM
Paolo Polidori
|
December 16, 2025
Introducing runtime file integrity monitoring and response with Sysdig FIM

EtherRAT: DPRK uses novel Ethereum implant in React2Shell attacks
Sysdig Threat Research Team
|
December 8, 2025
EtherRAT: DPRK uses novel Ethereum implant in React2Shell attacks

Detecting React2Shell: The maximum-severity RCE vulnerability affecting React Server Components and Next.js
Sysdig Threat Research Team
|
December 5, 2025
Detecting React2Shell: The maximum-severity RCE vulnerability affecting React Server Components and Next.js
join our newsletter
Stay up to date– subscribe to get blog updates now
Thank you! Your submission has been received!
Oops! Something went wrong while submitting the form.
IBM LinuxONE and Sysdig: Building cyber resilient systems in hybrid cloud environments
September 13, 2022
Durgesh Shukla
IBM LinuxONE and Sysdig: Building cyber resilient systems in hybrid cloud environments
No items found.

How Onna Technologies uses Snyk, Google Cloud & Sysdig to secure the SDLC while saving time and money
September 12, 2022
Susan Stone
How Onna Technologies uses Snyk, Google Cloud & Sysdig to secure the SDLC while saving time and money
Cloud Security
Sysdig Features

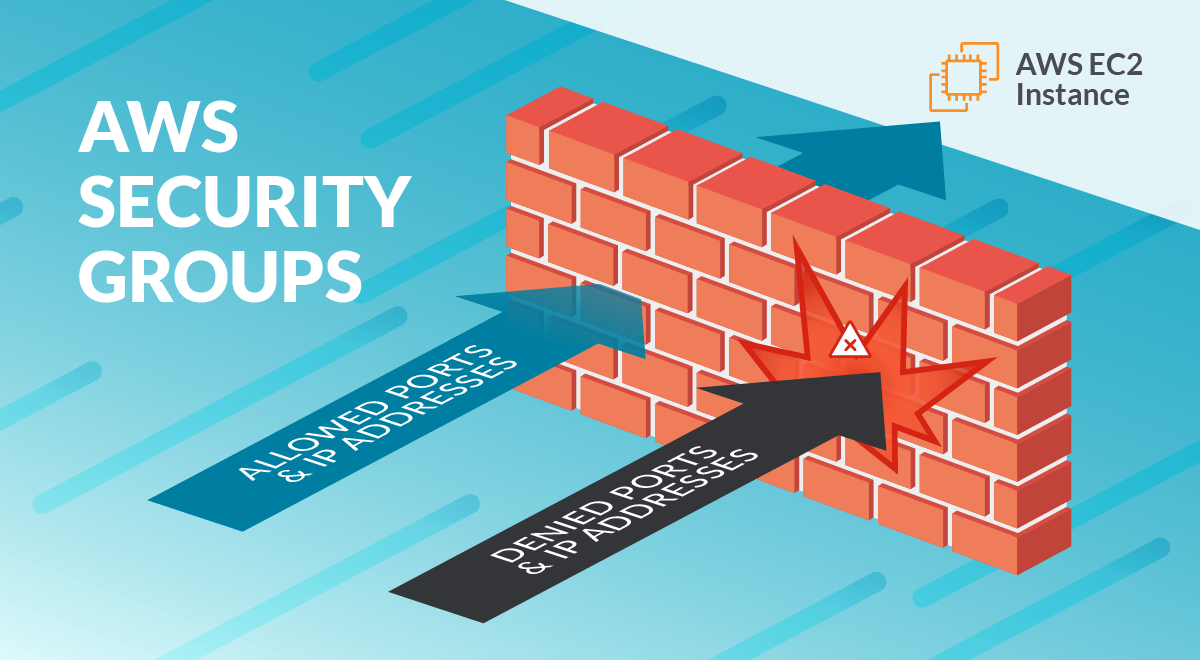
AWS Security Groups Guide
September 6, 2022
Brett Wolmarans
AWS Security Groups Guide
Cloud Security
Compliance
The Quiet Victories and False Promises of Machine Learning in Security
September 2, 2022
Anna Belak
The Quiet Victories and False Promises of Machine Learning in Security
Cloud Security
Kubernetes & Container Security
Threat Research
Turbocharge your Azure security and compliance posture with Sysdig
August 29, 2022
Durgesh Shukla
Turbocharge your Azure security and compliance posture with Sysdig
Cloud Security
Compliance

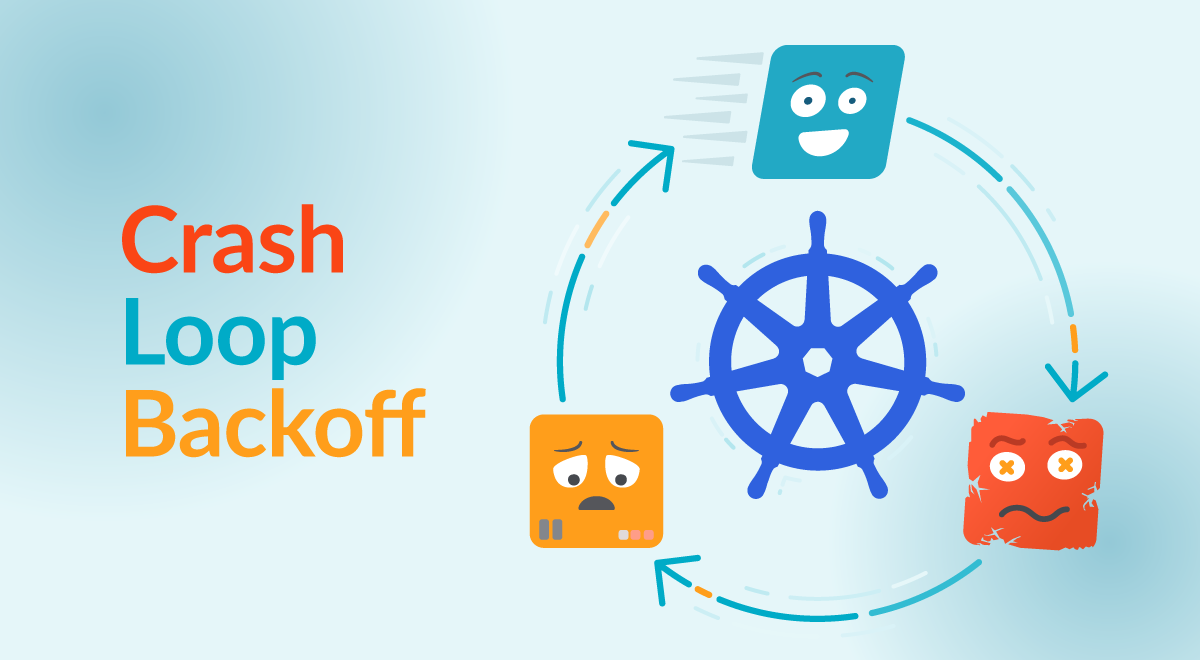
What is Kubernetes CrashLoopBackOff? And how to fix it
August 25, 2022
Javier Martínez
What is Kubernetes CrashLoopBackOff? And how to fix it
Monitoring