Browse all content by asset type.
Introducing the Sysdig open source community
DEFENSE REPORT
AI Helps Teams Reduce MTTR by 76%
Sysdig named representative vendor in Gartner Market Guide for CNAPP
Blog Posts
Hunting Reverse Shells: How the Sysdig Threat Research Team builds smarter detection rules
Shifting left with AI and MCP: Sysdig + Amazon Q Developer

How Falco and Stratoshark close the gap between open source runtime detection and deep forensic analysis
Briefs

The Business Value of Agentic AI for Cloud Security
Learn how agentic AI and Sysdig Sage™ combine human expertise with automation to accelerate cloud threat detection, streamline response, and cut security costs.

Sysdig Corporate Brief
Founded by the creators of open source standards — Falco, Stratoshark, and Wireshark — and built on agentic AI, Sysdig delivers real-time cloud defense grounded in the uncompromising truth of runtime.

BRIEF. 2025 Cloud‐Native Security and Usage Report
This is a special edition of Sysdig’s 2025 Cloud-Native Security and Usage Report, providing only the usage and analysis of the open source detection tool, Falco.
Case Studies

Greater Stability, Smarter Planning: How a Global Enterprise Gained Control of Its Cloud
Global Technology Leader unifies cloud monitoring to eliminate blind spots and outages

Caught in Runtime: How Sysdig Detected Credential Exposure in a Crypto Platform Before It Became a Breach
Cryptotrading Platform prevents breach with real-time visibility

Good-Enough Security Isn’t Good Enough When You Serve a Billion People
UIDAI secures 1.4B+ identities and 100M daily authentications with Sysdig.
Ebooks

Top 6 Use Cases for Monitoring Cloud-Native Workloads with Sysdig Monitor

Securing the Cloud: The Benefits of Falco with an Enterprise Experience
An ebook with 3 mini case studies heavily featuring Falco and how it works with Sysdig, plus a callout to Falco Feeds at the end.
Guides

Cloud Security for Google Cloud
This guide outlines key requirements and capabilities for establishing comprehensive security for Google Cloud services and containers.

Cloud Security for Amazon Web Services
This guide outlines key requirements and capabilities for establishing comprehensive security for AWS cloud services and containers.

Secure Your Cloud in Minutes - Your Checklist for Meeting the 555 Benchmark
Sysdig’s 555 Benchmark for Cloud Detection and Response offers a standard to use when measuring how fast your security teams can counter attackers. Specifically, the benchmark finds that to outpace attacks, your security teams need to detect threats within 5 seconds, correlate and triage data within the first 5 minutes, and initiate a tactical response within the next 5 minutes.Sysdig’s 555 Benchmark for Cloud Detection and Response offers a standard to use when measuring how fast your security teams can counter attackers. Specifically, the benchmark finds that to outpace attacks, your security teams need to detect threats within 5 seconds, correlate and triage data within the first 5 minutes, and initiate a tactical response within the next 5 minutes.
Infographics


The Evolution of Modern Cloud Security
Remember asking your teachers why you needed to know history? They probably said that learning history is important in understanding how society has changed and progressed over time, and that we can learn from past experiences and mistakes.


The Grand Atlas of Software Security
This infographic demonstrates how to secure each stage of the software lifecycle, with a focus on the Shift Left approach, where early remediation reduces risks and costs.
Podcasts

Exploring Advanced Cybersecurity with Michael Isbitski
"Cybersecurity leader Mike Isbitski explores the intricacies of cloud-native security and vulnerability management in today's technological landscape. With over 25 years of experience, he provides valuable insights into the challenges and complexities organizations face in securing ephemeral infrastructure and machine identities in the cloud. This episode also explores the cautious adoption of AI in cybersecurity, emphasizing the need for a balanced approach that maintains operational functionality while addressing evolving security concerns."

Screaming in the Cloud: Benchmarking Security Attack Response Times in the Age of Automation with Anna Belak
"Anna Belak, Director of the Office of Cybersecurity Strategy at Sysdig, joins Corey on Screaming in the Cloud to discuss the newest benchmark for responding to security threats, 5/5/5. Anna describes why it was necessary to set a new benchmark for responding to security threats in a timely manner, and how the Sysdig team did research to determine the best practices for detecting, correlating, and responding to potential attacks. Corey and Anna discuss the importance of focusing on improving your own benchmarks towards a goal, as well as how prevention and threat detection are both essential parts of a solid security program."

Screaming in the Cloud: An Open-Source Mindset in Cloud Security with Alex Lawrence
"Alex Lawrence, Field CISO at Sysdig, joins Corey Quinn on Screaming in the Cloud to discuss how he went from studying bioluminescence and mycology to working in tech, and his stance on why open source is the future of cloud security."
Press Releases
Sysdig Advances Its Vision for an Open Source Cloud Security Platform
Sysdig, the leader in real-time cloud security, today announced new open source threat investigation and analysis capabilities for Falco, the standard for runtime cloud threat detection used by more than 60% of the Fortune 500. These updates deepen Falco’s ability to integrate with Stratoshark, creating a unified, end-to-end cloud security workload built entirely on open source.

Sysdig Expands the Power of Runtime Context with New MCP Server and Partner Integration Hub
Sysdig, the leader in real-time cloud security, today announced the launch of its Model Context Protocol (MCP) server and partner integration hub, giving customers access to AI-powered security insights across their entire ecosystem.
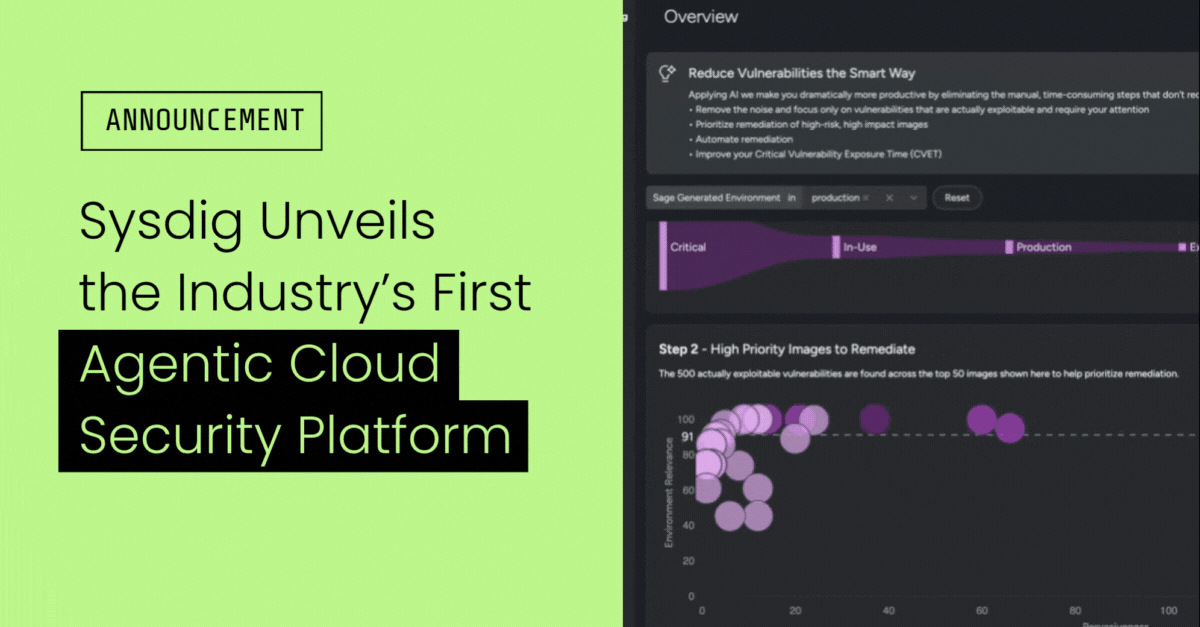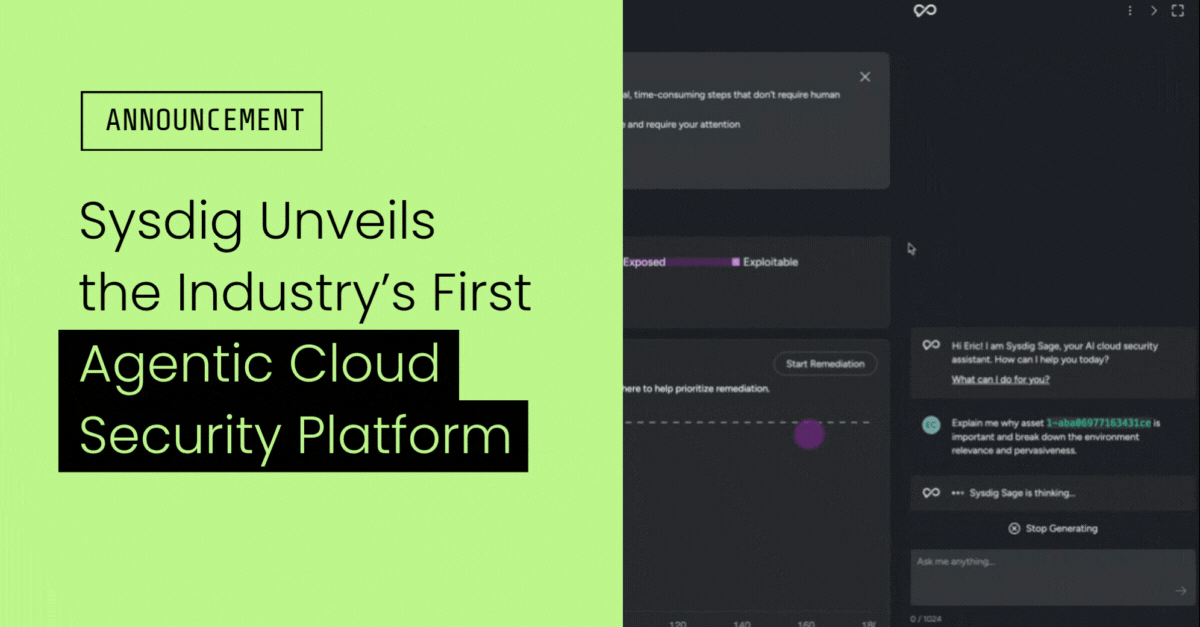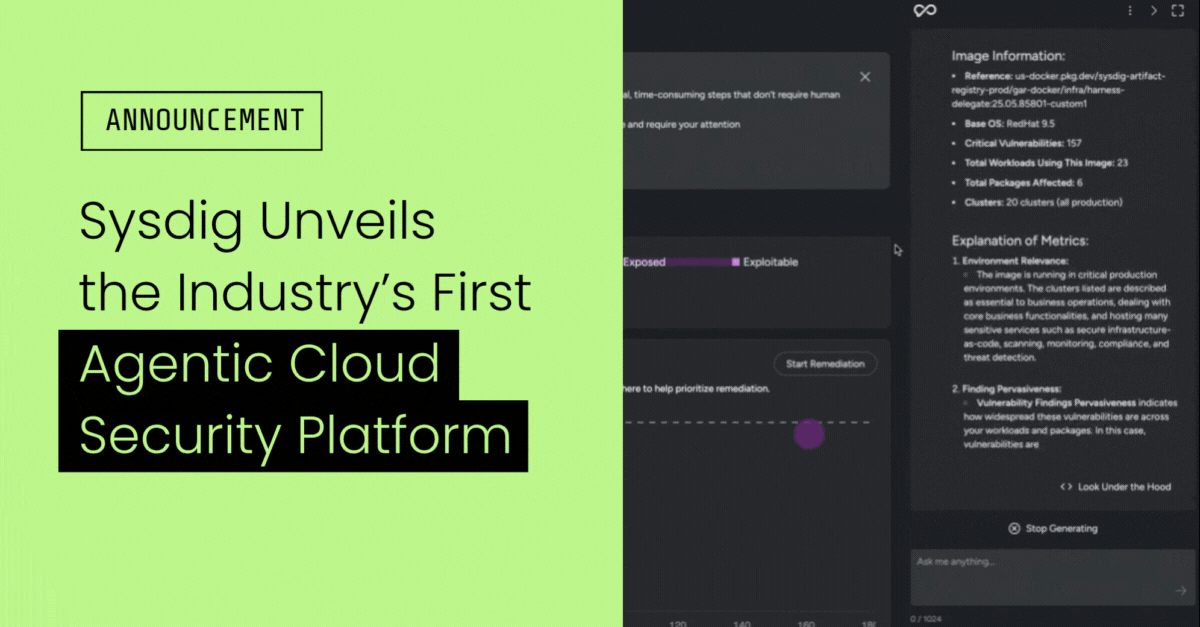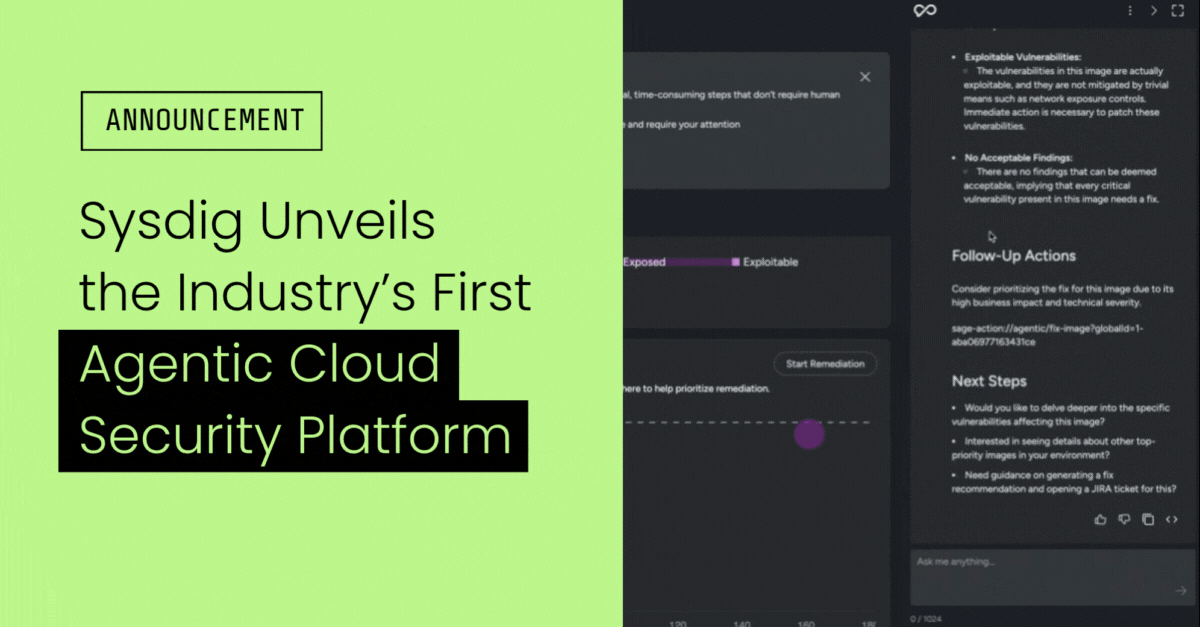
Sysdig Unveils the Industry’s First Agentic Cloud Security Platform
With semantic analysis powered by autonomous AI agents, Sysdig Sage™ surfaces critical business risks and helps organizations fix them at the source in minutes
Reports


Latio Tech 2025 Cloud Security Market Report
The 2025 Latio Cloud Security Market Report examines the technologies and strategies shaping the next generation of cloud and AI defense. As organizations adopt AI workloads and distributed architectures, the traditional boundaries of security continue to dissolve. Latio’s analysis highlights how the market is shifting from visibility to real-time, runtime protection—and why this evolution is critical to managing machine-speed risk. Within the report, Latio names Sysdig a leader for its ability to deliver the depth of telemetry, customization, and AI-driven correlation security teams need to operationalize cloud incident-response programs. By combining open innovation with deep runtime visibility, Sysdig helps organizations detect, prioritize, and respond to threats faster—across hybrid and AI-powered environments. This report serves as the most comprehensive guide for security leaders looking to understand where the market is headed, what capabilities define the leaders, and how to prepare their organizations for the future of cloud and AI security.


2025 Cloud Defense Report
Cloud attacks are accelerating, vulnerabilities are multiplying, and AI is reshaping both the attack surface and expectations for defense. In 2025, security leaders face a defining paradox: embracing AI to innovate and protect, while defending against the very AI-powered threats that evolve in seconds. The future of security lies in real-time, context-aware defense—rooted in visibility, collaboration, and AI that empowers defenders to move as fast as attackers.


Sysdig 2024 Cloud-Native Security and Usage Report
Videos

Detecting Threats to Kubernetes, Containers, and Google Cloud
See how Sysdig helps secure and accelerate innovation with Google Cloud.

Secure DevOps Practices at Yahoo Japan
With more than 3,000 developers and a large Kubernetes environment, learn how Yahoo Japan is preventing cyber-attacks and unauthorized access by introducing appropriate security measures for the container environment.

Securing and Monitoring AWS Container Services
Developers, operations, and security teams must work together to address key workflows to secure and monitor containers, Kubernetes and cloud services across...
Webinars

Securing Kubernetes with Agentic AI: From Noise to Clarity
See how Agentic AI turns Kubernetes security noise into actionable insight and faster response.
.png)
Streamlining Incident Response in the Cloud
Cloud environments move fast. Security teams can’t afford slow, manual response when incidents happen. That’s why modern organizations are shifting from reactive processes to continuous detection, runtime visibility, and automated remediation.
.png)
Shai-Hulud: The self-replicating NPM worm
How it works, why it matters, and how to defend
Events
Whitepapers


Securing AI: Navigating a New Frontier of Security Risk
Organizations worldwide are turning to artificial intelligence (AI) to gain insights, optimize operations, and remain competitive in an increasingly digitized economy. As businesses move workloads to cloud‑native environments to support these AI initiatives, they encounter a new frontier of security risk. For security managers building cloud security programs, it’s crucial to take a step back and ask: Does your current program truly cover the unique risks AI workloads bring?


The 555 Guide for Cloud Security Practitioners
The Sysdig 555 Benchmark for Cloud Detection and Response sets the standard for operating securely in the cloud, emphasizing the need for security teams to detect, triage, and respond to attacks within the average time it takes threat actors to conduct them: 10minutes.






